The combined address box and search bar at the top of the Chrome window is called the omnibox. The icon and optional verbose state text adjacent to that icon are collectively known as the Security Chip:
![]()
The security chip can render in a number of states, depending on the status of the page:
| Secure – Shown for HTTPS pages that were securely delivered using a valid certificate and not compromised by mixed content or other problems. | |
| Secure, Extended Validation – Shown for Secure pages whose certificate indicates that Extended Validation was performed. | |
Neutral – Shown for HTTP pages, as well as Chrome’s built-in pages, like chrome://extensions, as well as pages containing passive mixed content, or delivered using a policy-allowed SHA-1 certificates. |
|
| Not Secure – Shown for HTTP pages that contain a password or credit card input field. Learn more. | |
Not Secure (Red) – What Chrome will eventually show for all HTTP pages. You can configure a flag (chrome://flags/#mark-non-secure-as) to Always mark HTTP as actively dangerous today to get this experience early. |
|
| Not Secure, Certificate Error – Shown when a site has a major problem with its certificate (e.g. it’s expired). | |
| Dangerous – Shown when Google Safe Browsing has identified this page as a source of malware or phishing attacks. |
The flyout that appears when you click the security chip is called PageInfo or Website Settings; it shows the security status of the page and the permissions assigned to the origin website:

The text atop the pageinfo flyout explains the security state of the page:





Clicking the Learn More link on the flyout for valid HTTPS sites once opened the Chrome Developer Tools’ Security Panel, but now it goes to a Help article. To learn more about the HTTPS state of the page, instead press F12 and select the Security Panel:

The View certificate button opens the Windows certificate viewer and displays the current origin’s certificate. Reload the page with the Developer Tools open to see all of the secure origins in the Secure Origins List; selecting any origin allows you to view information about the connection and examine its certificate.

The floating grey box at the bottom of the Chrome window that appears when you over over a link is called the status bubble. It is not a security surface and, like IE’s status bar, it is easily spoofed.

Navigation to sites with severe security problems is blocked by an interstitial page.

(A list of interstitial pages in Chrome can be found at chrome://interstitials/ ).
Clicking on the error code (e.g. ERR_CERT_AUTHORITY_INVALID in the screenshot below) will show more information about the certificate of the blocked site:

Clicking the Advanced link shows more information, and in some cases will show an override link that allows you to disregard the security protection and proceed to the site anyway.
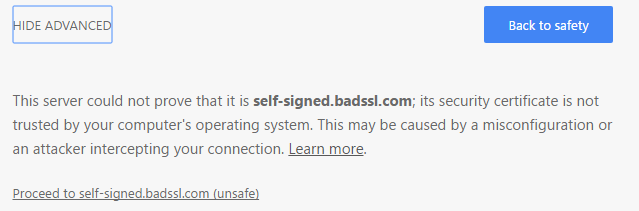
If a site uses HTTP Strict Transport Security, the Proceed link is hidden and the user has no visible option to proceed.

In current versions of Chrome, the user can type a fixed string (sometimes referred to as a Konami code) to bypass HSTS, but this option is deliberately undocumented and slated for removal from Chrome.
If a HTTPS problem is sufficiently bad, the network stack will not connect to the site and will show a network error page instead.

-Eric
PS: There exists a developer reference to Chrome Security UI across platforms, but it’s somewhat outdated.

Amazing doc. Thanks for sharing it.
As a user of Fiddler who often inspects HTTPS web traffic for hosts I don’t control, it would be awesome if this “Konami code” became a documented feature / config setting in Chrome.
Otherwise, Chrome is unusable for sites that have set up HSTS (unless I find a way to clear Chrome’s HSTS cache).
The bypass is expected to be removed.
The right way to handle your scenario is to configure the OS to trust Fiddler’s root certificate. This also bypasses HPKP.
Thanks a lot for this writeup!