For some time now, operating behind the scenes and going mostly unnoticed, Google has been changing the infrastructure used to provide HTTPS certificates for its sites and services.
You’ll note that I said mostly. Over the last few months, I’ve periodically encountered complaints from users who try to load a Google site and get an unexpected error page:

Now, there are a variety of different problems that can cause errors like this one– in most cases, the problem is that the user has some software (security software or malware) installed locally that is generating fake certificates that are deemed invalid for various reasons.
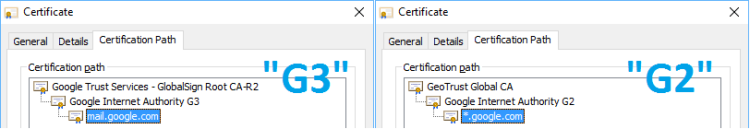
However, when following troubleshooting steps, we’ve determined that a small number of users encountering this NET::ERR_CERT_AUTHORITY_INVALID error page are hitting it for the correct and valid Google certificates that chain through Google’s new intermediate Google Internet Authority G3. That’s weird.
What’s going on?
The first thing to understand is that Google operates a number of different certificate trust chains, and we have multiple trust chains deployed at the same time. So a given user will likely encounter some certificate chains that go through the older Google Internet Authority G2 chain and some that go through the newer Google Internet Authority G3 chain– this isn’t something the client controls.
You can visit this GIA G3-specific test page to see if the G3 root is properly trusted by your system.
More surprisingly, it’s also the case that you might be getting a G3 chain for a particular Google site (e.g. https://mail.google.com) while some other user is getting a G2 chain for the same URL. You might even end up with a different chain simply based on what Google sites you’ve visited first, due to a feature called HTTP/2 connection coalescing.
In order to see the raw details of the certificate encountered on an error page, you can click the error code text on the blocking page. (If the site loaded without errors, you can view the certificate like so).
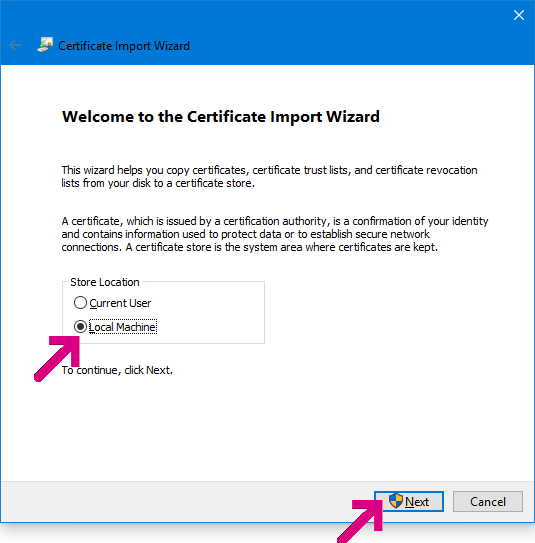
Google’s new certificate chain is certainly supposed to be trusted automatically– if your operating system (e.g. Windows 7) didn’t already have the proper certificates installed, it’s expected to automatically download the root certificate from the update servers (e.g. Microsoft WindowsUpdate) and install it so that the certificate chain is recognized as trusted. In rare instances, we’ve heard of this process not working– for instance, some network administrators have disabled root certificate updates for their enterprise’s PCs.
On modern versions of Windows, you can direct Windows to check its trusted certificate list against the WindowsUpdate servers by running the following from a command prompt:
certutil -f -verifyCTL AuthRootWU
Older versions of Windows might not support the -verifyCTL command. You might instead try downloading the R2 GlobalSign Root Certificate directly and then installing it in your Trusted Root Certification Authorities:




Overall, the number of users reporting problems here is very low, but I’m determined to help ensure that Chrome and Google sites work for everyone.
-Eric
Excellent! Remarks..
(Editorial) The first thing you need to know…
(better) A site certificate needs a valid Certificate Path or Issuer chain of site..intermediate..root certificates. (cont..) Google operates…at the same time. The new G3 is a new intermediate and also has a new root.
So a given user…
(end of editorial stuff)
The RootR2.crt file should have GlobalSign in it’s name.
Installing the new GlobalSign root fixes the Connection Not Private failure, but doesn’t cache the new G3 intermediate. This is only an efficiency hit. I’m guessing the SSL connection gets the new G3 in memory, but fails to save it to the Intermediate store, for the same reason the root is not being saved to the Trusted Root store. Inspecting the cert store with certmgr.msc never sees G3, even when the client automatically installs the root cert, unless G3 is manually installed,
E.g. my Win10 laptop auto loads the GlobalSign-R2 root, but doesn’t save G3 to the Intermediate store. If I wasn’t debugging this I would never have noticed. GMail works just fine.
I’ll begin redirecting trouble reports to text/plain. I was going to setup a similar condensed Chrome forum thread. This is much nicer..
All:
To check if this fix applies to your problem: click the NET:ERR_CERT_AUTHORITY_INVALID tag,
to display the diagnostic text,
if the second PEM block begins: MIIEXDCCA0SgAwIB…
then installing the new Google root certificate will likely fix the problem.
Eric
I just ran a certUtil AuthRootWU test, I did:
delete the new Google root: GlobalSignGoogleTrustSvcsRootCA-R2
from certmgr.msc, close the certmgr.
ran certutil -f -verifyCTL AuthRootWU (as me, with admin privs, but not runAs Admin)
which updated many, then failed.
It installed a GlobalSign ECC Root CA – R5, but not the new Google GlobalSign Root CA-R2.
Accessing GMail then updated the missing Google root -R2.
The certutil AuthRootWU update may not fix the GMail problem for users..
Eric:
I have a user or two who is willing to post a net-export log for the GMail root cert failure. Is there a CR where we can focus the technical discussion?
Eric: The failed root cert install is affecting: IE & Chome, YouTube ads, text/plain, and a few *.google.countryCode sites.
As this is a Windows cert management issue, who can help us track this down with Microsoft network stack experience? Are there registry/policy values we should look at?
E.g. HKLM/Software/Policies/Microsoft/SystemCertificates/
AuthRoot/DisableRootAutoUpdate
Unfortunately, no, I don’t know anyone at Microsoft that works on this space anymore. The G3 issue likely affects many different Google sites. text/plain does not use a Google certificate and any user having problems reaching this blog likely has a different problem. It will affect any browser that uses the Windows certificate store (so, most browsers other than Firefox).
Please help
NET::ERR_CERT_AUTHORITY_INVALID
Subject: *.google.co.th
Issuer: Google Internet Authority G3
Expires on: Jan 9, 2018
Current date: Oct 30, 2017
PEM encoded chain:
—–BEGIN CERTIFICATE—–
MIIEmjCCA4KgAwIBAgIIQQOo+4ZJLiswDQYJKoZIhvcNAQELBQAwVDELMAkGA1UE
BhMCVVMxHjAcBgNVBAoTFUdvb2dsZSBUcnVzdCBTZXJ2aWNlczElMCMGA1UEAxMc
R29vZ2xlIEludGVybmV0IEF1dGhvcml0eSBHMzAeFw0xNzEwMTcxMTAxMjhaFw0x
ODAxMDkxMDAwMDBaMGgxCzAJBgNVBAYTAlVTMRMwEQYDVQQIDApDYWxpZm9ybmlh
MRYwFAYDVQQHDA1Nb3VudGFpbiBWaWV3MRMwEQYDVQQKDApHb29nbGUgSW5jMRcw
FQYDVQQDDA4qLmdvb2dsZS5jby50aDCCASIwDQYJKoZIhvcNAQEBBQADggEPADCC
AQoCggEBALdGp9fQ2Ful6z+369LILc9qYQvwQk3efw4QLa6J5ynS8IaUJ7qyvkeP
EGFKD/igLJEELNd2iZK0Yo4ZMGwaqRmQbL5j6QOfDFZjTxEGseHFOtNtQlEZGeHI
A08elXaCjCKm5yRTqM4abfT2MZaesqQENS79hDdiASeO55Mynxae8l18RFs5g9pr
gjlVXx1jpN8MPxA/nvvBNQmkETkGC8m0vlMJYEroc+CjIoUu5iQVgIKz8Vq8uOcM
qZp8cQRUZ4Orri0YEQU5N/OfAnlKV44YP4yBnJxBbDI2F74hoghwEoyqUEWjw9OC
POMeW/iRlfHvWlgTdUh7AN1AHB8/A2kCAwEAAaOCAVowggFWMB0GA1UdJQQWMBQG
CCsGAQUFBwMBBggrBgEFBQcDAjAnBgNVHREEIDAegg4qLmdvb2dsZS5jby50aIIM
Z29vZ2xlLmNvLnRoMGgGCCsGAQUFBwEBBFwwWjAtBggrBgEFBQcwAoYhaHR0cDov
L3BraS5nb29nL2dzcjIvR1RTR0lBRzMuY3J0MCkGCCsGAQUFBzABhh1odHRwOi8v
b2NzcC5wa2kuZ29vZy9HVFNHSUFHMzAdBgNVHQ4EFgQUan4jxk2VwITzmWtatEuh
7Q2OprAwDAYDVR0TAQH/BAIwADAfBgNVHSMEGDAWgBR3wrhQmmd2drEtwobQg6B+
pn66SzAhBgNVHSAEGjAYMAwGCisGAQQB1nkCBQMwCAYGZ4EMAQICMDEGA1UdHwQq
MCgwJqAkoCKGIGh0dHA6Ly9jcmwucGtpLmdvb2cvR1RTR0lBRzMuY3JsMA0GCSqG
SIb3DQEBCwUAA4IBAQBBbP+rvRWMQxrFoXUmYc391tMLygLO6yfaFP9PgYIWHQCl
CZe5pRILayQuDm8w2CLTJ0qPvPBlU3aEUE8m1YyqrLr3aw0q5h6PTWXSb6sjIluP
DtHXd6FTdW7bQpvtSLqW6OWvuJemiwiRwLn+vyztdi6zWRTryjSDTAD8ud14TRHI
8mF1veXi5IzF1nTcqgGLvlDWUn0iGmNKXRXL+HkklRmFTKauKpmsgh/2YJVT+aEX
LDrEXKIjXumiUvIXNZq9/N4ZMK6Dx1wpPHB4SavVtqMV7GH1F+Uhpup+66Txzxj4
voq/1OCvdq2Q6pa/36gZCxdMGFDgXrgTXZWYWz/r
—–END CERTIFICATE—–
Yes, you’ll need to follow the instructions in this post to fix that error.
Eric: Are we looking at a short fuze? When will other (US) *.google.com servers update to the new intermediate G3 and new root GlobalSign certificates?
Most of the Chrome forum posts are from google…CountryCode sites – several/day in the Chrome forum, similar rates in external forums (e.g. UC Browser Connection not private:
http://forum.ucweb.com/search.php?mod=forum,
search for ‘Connection not private’ )
Are these rates a pre-cursor to when other servers update to G3?
There is also a catch-22 aspect: some users cannot post their failures, because their help requests are being blocked by the same failure. Is there a fail-safe, non-HSTS URL for this situation?
Eric: There was a 6/27/17 Microsoft Trusted Root Certificate Program deployment update that included the GlobalSign R2-CA root cert. Look here.
https://social.technet.microsoft.com/wiki/contents/articles/31680.microsoft-trusted-root-certificate-program-updates.aspx
Is there a way to check that the affected users recieved/have access to this update?
It’s not clear to me whether that update itself would help; the “R2” root wasn’t added, it just had some metadata altered.
OK, confirms my assumption that the GlobalSign R2-CA root cert was in the Microsoft list.
My understanding of the root cert update process is:
-client (user), when not in store, back tracks and receives root cert
-polls microsoft update service to verify cert is in list
-if OK, install in Trusted Root store (local cache)… continue
What I meant or was leading up to is:
is there a way to check that the affected users poll the list OK?
I believe the windows event is: Windows Log\Application, source CAPI2,
Event ID 7(OK), 8(fail)
ref: https://technet.microsoft.com/en-us/library/cc749331(ws.10).aspx
I have a broken Win7Pro user/tester who receives Win updates regularly (last 10/11),
who fetches the GMail root R2-CA cert, but fails the install step.
We’re trying to understand why.
Eric: I opened CR 787898 11/22 while trying to find another route for a user (SStack) who could not reach text/plain for the same reason (DST root update failed). The CR quickly moved to WontFix, as expected, as this is a user Microsoft config problem.
Along the way, rsleevi has raised concerns that manually installing a root cert may have downsides when the cert updates in the future. Could you look at the CR comments and weigh in?
ASFAIK the future risk is minimal, and this is the only recourse we have at this time. If you have any thoughts on a better solution to restoring general windows certificate health, that would be appreciated too. I have yet to find a certutil command that works.
https://bugs.chromium.org/p/chromium/issues/detail?id=787898
Per the 9/11 Google Security Blog on Symantec Distrust, Chrome 66 will distrust Symantec and partner (root) certs. Partners include GeoTrust.
Many *.google.com services use the intermediate Google Internet Authority G2 valid 5/22/17 – 12/31/18 and GeoTrust Global CA, root cert valid 5/20/2002 – 5/20/2022. Does the v66 distrust include these Google services? Examples: {productforums, myaccount, support}.google.com
Per the article, DevTools is already providing alerts for the target certs.
What do the alerts look like?
Is there a demo server, like badSSL, that will trigger the alerts?
9/11 Security Blog:
https://security.googleblog.com/2017/09/chromes-plan-to-distrust-symantec.html
I don’t think there’s a specific Symantec-deprecation test site, but you can see the warnings in Chrome’s Developer Tools console by visiting many popular sites, e.g. load https://www.1800flowers.com/
As the GeoTrust-rooted certs used by the Google sites you’re listed don’t light up the warning, my assumption is that the GeoTrust root wasn’t one of the ones that had poor validation practices and thus it’s not subject to the change.
This is great if you’re on a PC, though not thrilled about doing it on the 6 computes used in my house, but what about the 4 tablets and 3 mobile phones?
This problem rarely occurs on a single device. If you’re seeing it on multiple devices, it’s very likely that you have a different problem entirely.
It is concurring on every device used in our house. So far this is the closest I’ve come to any solution and as much as I’ve been a fan of Chrome other than searching for a new web browser I’m at a loss. Perhaps Chronium will not have the problem, though that only helps a few of them, luckily the computers most often used, and the mobile device can be left not connected to the network unless printing.
What devices do you have specifically? And you’ve installed the certificate and it resolves the problem?
I am using a HP 2000 Notebook PC with Windows 10 Home Version 1511 OS build 10586.633…
I get this error message:
Your connection is not private
Attackers might be trying to steal your information from mail.google.com (for example, passwords, messages, or credit cards). Learn more
NET::ERR_CERT_AUTHORITY_INVALID
Subject: mail.google.com
Issuer: Google Internet Authority G3
Expires on: Feb 8, 2018
Current date: Dec 5, 2017
Yes, you should try the suggestion in this blog post.
Hi, i have the same error but when I go to check certification path it is not G2 or G3 but DST root CA X3. What should I do then? when i go to chrome settings -> manage certificates i can see that http://www.google.com is in the untrusted publishers tab. maybe if I could remove google.com from there it will solve my problem, but i do not know how to do it.
Do not remove anything from Untrusted Publishers. Follow the advice in https://textslashplain.com/2017/03/30/get-help-with-https-problems/ to get the DIAGNOSTIC INFORMATION from the error page and then add it in a reply to this comment.
Hi, please help me, windows 7 64 bit, Version Chrome 63.0.3239.132 ( 64bit)
PEM encoded chain:
—–BEGIN CERTIFICATE—–
MIIEqzCCA5OgAwIBAgIIbzP+2qo1TYowDQYJKoZIhvcNAQELBQAwVDELMAkGA1UE
BhMCVVMxHjAcBgNVBAoTFUdvb2dsZSBUcnVzdCBTZXJ2aWNlczElMCMGA1UEAxMc
R29vZ2xlIEludGVybmV0IEF1dGhvcml0eSBHMzAeFw0xODAxMTYwOTUzMDRaFw0x
ODA0MTAwODQzMDBaMGkxCzAJBgNVBAYTAlVTMRMwEQYDVQQIDApDYWxpZm9ybmlh
MRYwFAYDVQQHDA1Nb3VudGFpbiBWaWV3MRMwEQYDVQQKDApHb29nbGUgSW5jMRgw
FgYDVQQDDA8qLmdvb2dsZS5jb20ucnUwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAw
ggEKAoIBAQDJc+8r4UhsoaZDoauDQN1z0ThtG6zn6vVjpQPa8ULB3OJvOE/zLxjb
74Xr0R3cLBv1HP9tZNsCYDEcIUtGsefip2U3fJGIv4j/CXgoQlA2BgpQvugqvxB1
ui0YAToh2Fhoe+ZzdyEAuPQ7NBQacNn/LCRb96DtgpqmDJm5FU9vnXPp5oQsBOfQ
1uRxB/H34zgP+UVWHuqzLY3k3ZwASq1t7s0OZ5KXZCcF/8akcFQt7V5XJLJvYV0e
WL8xGdu7LuUWLmg54Cm2U8UudbnLf6Y6OyII4+bYF8WMVlaOWK7dfPmSNMsLxvZL
sJcy8wfbdEvuioRnR/Nzfupujju5b60zAgMBAAGjggFqMIIBZjATBgNVHSUEDDAK
BggrBgEFBQcDATBBBgNVHREEOjA4gg8qLmdvb2dsZS5jb20ucnWCCyouZ29vZ2xl
LnJ1gg1nb29nbGUuY29tLnJ1gglnb29nbGUucnUwaAYIKwYBBQUHAQEEXDBaMC0G
CCsGAQUFBzAChiFodHRwOi8vcGtpLmdvb2cvZ3NyMi9HVFNHSUFHMy5jcnQwKQYI
KwYBBQUHMAGGHWh0dHA6Ly9vY3NwLnBraS5nb29nL0dUU0dJQUczMB0GA1UdDgQW
BBRXEj6L8nYMkL+7/VUGm2mEHkynIjAMBgNVHRMBAf8EAjAAMB8GA1UdIwQYMBaA
FHfCuFCaZ3Z2sS3ChtCDoH6mfrpLMCEGA1UdIAQaMBgwDAYKKwYBBAHWeQIFAzAI
BgZngQwBAgIwMQYDVR0fBCowKDAmoCSgIoYgaHR0cDovL2NybC5wa2kuZ29vZy9H
VFNHSUFHMy5jcmwwDQYJKoZIhvcNAQELBQADggEBAJsaTOWLE5nZQq4bVM+6wiqS
qXadaxwLEOvEYzOAe0CiQkVUXL08vHYcLeVYsUfQtaiJGaj/iSRdlOxK9VwUSUOp
1tqDaaprv7/nfrd4lQ4L257nUHkCham+Qq9onZrai9yU2DEFAcBsCNOjCnDPz3r7
PRw9r/Cqw2IpCy7U/MgCWF/9woL7KaEv2zJJHzWX9dnJhssuO3J4CN8NI2DN0tr0
JBwR0eSUvHDzJZWE+4nf1qmBxpNPLmak7qW3EHcXcGU9yx2++4dMhTCyMkVLXbQg
v/IHdmSnNgh8uurYt6Y4zUExornxp0AwXpneMus/EdmlhggKXXUtd0eMbbvR5as=
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIEXDCCA0SgAwIBAgINAeOpMBz8cgY4P5pTHTANBgkqhkiG9w0BAQsFADBMMSAw
HgYDVQQLExdHbG9iYWxTaWduIFJvb3QgQ0EgLSBSMjETMBEGA1UEChMKR2xvYmFs
U2lnbjETMBEGA1UEAxMKR2xvYmFsU2lnbjAeFw0xNzA2MTUwMDAwNDJaFw0yMTEy
MTUwMDAwNDJaMFQxCzAJBgNVBAYTAlVTMR4wHAYDVQQKExVHb29nbGUgVHJ1c3Qg
U2VydmljZXMxJTAjBgNVBAMTHEdvb2dsZSBJbnRlcm5ldCBBdXRob3JpdHkgRzMw
ggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDKUkvqHv/OJGuo2nIYaNVW
XQ5IWi01CXZaz6TIHLGp/lOJ+600/4hbn7vn6AAB3DVzdQOts7G5pH0rJnnOFUAK
71G4nzKMfHCGUksW/mona+Y2emJQ2N+aicwJKetPKRSIgAuPOB6Aahh8Hb2XO3h9
RUk2T0HNouB2VzxoMXlkyW7XUR5mw6JkLHnA52XDVoRTWkNty5oCINLvGmnRsJ1z
ouAqYGVQMc/7sy+/EYhALrVJEA8KbtyX+r8snwU5C1hUrwaW6MWOARa8qBpNQcWT
kaIeoYvy/sGIJEmjR0vFEwHdp1cSaWIr6/4g72n7OqXwfinu7ZYW97EfoOSQJeAz
AgMBAAGjggEzMIIBLzAOBgNVHQ8BAf8EBAMCAYYwHQYDVR0lBBYwFAYIKwYBBQUH
AwEGCCsGAQUFBwMCMBIGA1UdEwEB/wQIMAYBAf8CAQAwHQYDVR0OBBYEFHfCuFCa
Z3Z2sS3ChtCDoH6mfrpLMB8GA1UdIwQYMBaAFJviB1dnHB7AagbeWbSaLd/cGYYu
MDUGCCsGAQUFBwEBBCkwJzAlBggrBgEFBQcwAYYZaHR0cDovL29jc3AucGtpLmdv
b2cvZ3NyMjAyBgNVHR8EKzApMCegJaAjhiFodHRwOi8vY3JsLnBraS5nb29nL2dz
cjIvZ3NyMi5jcmwwPwYDVR0gBDgwNjA0BgZngQwBAgIwKjAoBggrBgEFBQcCARYc
aHR0cHM6Ly9wa2kuZ29vZy9yZXBvc2l0b3J5LzANBgkqhkiG9w0BAQsFAAOCAQEA
HLeJluRT7bvs26gyAZ8so81trUISd7O45skDUmAge1cnxhG1P2cNmSxbWsoiCt2e
ux9LSD+PAj2LIYRFHW31/6xoic1k4tbWXkDCjir37xTTNqRAMPUyFRWSdvt+nlPq
wnb8Oa2I/maSJukcxDjNSfpDh/Bd1lZNgdd/8cLdsE3+wypufJ9uXO1iQpnh9zbu
FIwsIONGl1p3A8CgxkqI/UAih3JaGOqcpcdaCIzkBaR9uYQ1X4k2Vg5APRLouzVy
7a8IVk6wuy6pm+T7HT4LY8ibS5FEZlfAFLSW8NwsVz9SBK2Vqn1N0PIMn5xA6NZV
c7o835DLAFshEWfC7TIe3g==
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIDujCCAqKgAwIBAgILBAAAAAABD4Ym5g0wDQYJKoZIhvcNAQEFBQAwTDEgMB4G
A1UECxMXR2xvYmFsU2lnbiBSb290IENBIC0gUjIxEzARBgNVBAoTCkdsb2JhbFNp
Z24xEzARBgNVBAMTCkdsb2JhbFNpZ24wHhcNMDYxMjE1MDgwMDAwWhcNMjExMjE1
MDgwMDAwWjBMMSAwHgYDVQQLExdHbG9iYWxTaWduIFJvb3QgQ0EgLSBSMjETMBEG
A1UEChMKR2xvYmFsU2lnbjETMBEGA1UEAxMKR2xvYmFsU2lnbjCCASIwDQYJKoZI
hvcNAQEBBQADggEPADCCAQoCggEBAKbPJA6+Lm8omUVCxKs+IVSbC9N/hHD6ErPL
v4dfxn+G07IwXNb9rfF73OX4YJYJkhD10FPe+3t+c4isUoh7SqbKSaZeqKeMWhG8
eoLrvozps6yWJQeXSpkqBy+0Hne/ig+1AnwblrjFuTosvNYSuetZfeLQBoZfXklq
tTleiDTsvHgMCJiEbKjNS7SgfQx5TfC4LcshytVsW33hoCmEofnTlEnLJGKRILzd
C9XZzPnqJworc5HGnRusyMvo4KD0L5CLTfuwNhv2GXqF4G3yYROIXJ/gkwpRl4pa
zq+r1feqCapgvdzZX99yqWATXgAByUr6P6TqBwMhAo6CygPCm48CAwEAAaOBnDCB
mTAOBgNVHQ8BAf8EBAMCAQYwDwYDVR0TAQH/BAUwAwEB/zAdBgNVHQ4EFgQUm+IH
V2ccHsBqBt5ZtJot39wZhi4wNgYDVR0fBC8wLTAroCmgJ4YlaHR0cDovL2NybC5n
bG9iYWxzaWduLm5ldC9yb290LXIyLmNybDAfBgNVHSMEGDAWgBSb4gdXZxwewGoG
3lm0mi3f3BmGLjANBgkqhkiG9w0BAQUFAAOCAQEAmYFThxxol4aR7OBKuEQLq4Gs
J0/WwbgcQ3izDJr86iw8bmEbTUsp9Z8FHSbBuOmDAGJFtqkIk7mpM0sYmsL4h4hO
291xNBrBVNpGP+DTKqttVCL1OmLNIG+6KYnX3ZHu01yiPqFbQfXf5WRDLenVOavS
ot+3i9DAgBkcRcAtjOj4LaR0VknFBbVPFd5uRHg5h6h+u/N5GJG79G+dwfCMNYxd
AfvDbbnvRG15RjF+Cv6pgsH/76tuIMRQyV+dTZsXjAzlAcmgQWpzU/qlULRuJQ/7
TBj0/VLZjmmx6BEP3ojY+x1J96relc8geMJgEtslQIxq/H5COEBkEveegeGTLg==
—–END CERTIFICATE—–
This appears to be a legitimate certificate. What problem are you encountering specifically? (What URL are you visiting, and what error code is shown in the page?)
Eric – Looks like some India Rail (IRCTC) users are stumbling on a failed root cert update on old Android phones (4.4.4). Any suggestions? Look here
https://productforums.google.com/forum/#!topic/chrome/Np-f9eQ3_ek
It’s a short thread. Pretty easy to digest, except the term used for reply is ‘revert’
I’m hard pressed to believe that this root cert valid from 8/1/13 is causing a problem today, but it’s hard to argue with Dharmesh’s screenshot.
IRCTC resolved the root cert issue 4/17 by changing (again) to use an older cert: DigiCert High Assurance EV Root CA issued 11/9/06
Eric: It looks like other Google services are upgrading to the Google Internet Authority G3 (GIA G3) intermediate cert, in the last few days (since 4/2). And this means the new GlobalSign Root CA-R2 root.
The Chrome Help forum is now using GIA G3, but the Google Drive forum is still GIA G2.
http://www.google.com (search) switched, first in some of the country code sites like http://www.google.com.hk and http://www.google.se, and now in the US.
Users with an uninstalled GlobalSign Root CA-R2 root cert will no longer be able to reach the forum with their Authority_Invalid problems.. a real catch-22.
Suggestions?
P.S. This Chrome Help Forum thread is a prime example. When the OP started with a http://www.google.se GIA G3 problem, the forum was still reachable via the old GIA G2. It took a couple of attempts and several posts for them to get the GlobalSign R2 root installed. The last redo instructions were yesterday 4/5 with GIA G2. Their ‘it works’ confirmation came today via GIA G3, just hours after they fixed their GS R2 problem.
https://productforums.google.com/forum/#!msg/chrome/DojLqwgDEHY/Onek99huAwAJ
> Suggestions?
I’m not really sure what you’re asking; in general, Windows installs root certificates on an on-demand basis. It’s always been the case that a user with a sufficiently broken system may be blocked from reading HTTPS Help articles; Chrome recently took a change to include more in-product help to address the scenario where the user’s got HTTPS problems and cannot reach the help center.
Thanks. I was looking for suggestions when users cannot reach the Help forum (or HTTPS Help articles). Where can I see an example of the improved Chrome in-product help, when the help center is not reachable?
Eric (Suggestions): Would it be worthwhile for Google to email all active Google Chrome users without GMail accounts to test the GlobalSign Root CA-R2 root, and if they have problems redirect to Chrome Forum or other help, before they are cutoff with the root cert change?
This is not unprecedented. When Supervised Users was deactivated abruptly Jan 2018, there was a warning email sent 1/8/18.
Gmail users will have already seen the problem, if present, already had a chance to get help and can be excluded.
Limiting the list to active Chrome users eliminates historic stale accounts.
I’m sure there are many other privacy and branding issues to be considered.
Just a suggestion.
Among other problems, Google does not have the email addresses of “all active Google Chrome users”.
Re: ‘Google does not have email addresses’ – I’d settle for the active users who signin with a Google account. I assume Google has access to the account email addresses since the email address is used for origination and subsequent signin.
Eric, many thanks for your information on this certificates problem. My elderly relative has now suddenly got this issue on her HP Pavilion G6 Notebook PC. Windows 7 Home premium 64 bit. I have tracked through the certificates and confirm that the loaded certificate is G2 and the requesting authority is now G3. Clearly, the G3 certificate has failed to load if I read your commentary correctly. My dilemma now is that I cannot locate how I load the certificate and where I obtain it from. I can go into the mmc console on my own desktop PC and it’s all there. I enter the mmc console on the laptop and all that shows is a folder called “Console root” that will not open. I would appreciate it if you could point the way around this as I don’t want to break the Windows 7 setup for obvious reasons. In the meantime I have applied the workaround using the “-ignore-certificate-errors” switch. Maybe this is as good as it gets for this machine ?? We are in Australia (Perth) if location is relevant. Many thanks.
You definitely won’t want to use –ignore-certificate-errors as this is unsafe and is applied to every site.
Have you verified that all updates from Windows Update have been installed?
Can you collect the info from https://textslashplain.com/2017/03/30/get-help-with-https-problems/ and send it to me? I’ll take a look.
FWIW, you can copy the root from one machine to another. On the working machine, click the “Secure” button in the omnibox. Click Certificates. The Windows cert viewer opens. Click the “Certification path” tab. Click the “Global Sign” root at the top of the list. Click “Details”. Click “Copy to file”. Save the .CER file. Copy the CER file to the affected machine. Open the certificate. On the General tab, click “Install Certificate”. Click “Local Machine”. Click “Place all certificates in the following store”. Click Browse. Click “Trusted Root Certification Authorities”. click Ok.
Thanks Eric for your reply. Much appreciated. In relation to Windows updates, the first thing I did was to undo the last update as I suspected this may have been the issue (it was a big update on my desktop at least with Win 10 although the problem laptop is Win 7). Anyway, next time I booted it (the laptop), it automatically re-ran the updates, so Windows updates are all up to date. The Chrome browser version is 66.0.3359.18. I did see some comment about Comodo anti virus software, which is loaded on this machine. I’ve looked for an appropriate area to disable SSL scanning, but can’t see one. As I explained earlier, this is not my machine, but am assisting an elderly relative so am not familiar with Comodo at all. Here is the error message text:
Thanks
John
ET::ERR_CERT_AUTHORITY_INVALID
Subject: tls.automattic.com
Issuer: Let’s Encrypt Authority X3
Expires on: 22 Aug 2018
Current date: 2 Jun 2018
PEM encoded chain:
—–BEGIN CERTIFICATE—–
MIIKdzCCCV+gAwIBAgISA5/KwymFBHCfGEFRaQmBmoK0MA0GCSqGSIb3DQEBCwUA
MEoxCzAJBgNVBAYTAlVTMRYwFAYDVQQKEw1MZXQncyBFbmNyeXB0MSMwIQYDVQQD
ExpMZXQncyBFbmNyeXB0IEF1dGhvcml0eSBYMzAeFw0xODA1MjMxNjUwMTZaFw0x
ODA4MjExNjUwMTZaMB0xGzAZBgNVBAMTEnRscy5hdXRvbWF0dGljLmNvbTCCASIw
DQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBALWpCRRKuucFaVsZUqEKSOdp3kif
LAoEC4cS8CXSqU1mzp/yUvCVtDyQTYulrgQKC25UF5S1t79iPKxnHhXi6IfbqR5d
xtOU2ktJZACV6cUSgrfycIPxJdaZI8L4Yq/hNkqhLSEFy2JAoYYQD6HWLYGNNSQP
DobUxO8BUNClLEJiaQQhYWSyR3zE3KurjddLT0TUfkyyeaIBo8+wub2o4y57U9P2
1WgkxuBnyvrlogDAvSiyY2mwpUc3c7fjG8O9n/qt0gSo+qSWnFs2Ap27mUIt44fL
/KSImiH2MspKxSPczzHKGXk4bRllej5JjSYWu0uZfJZL4p3NHr4dE6kr7ukCAwEA
AaOCB4Iwggd+MA4GA1UdDwEB/wQEAwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAQYI
KwYBBQUHAwIwDAYDVR0TAQH/BAIwADAdBgNVHQ4EFgQUDdTkQqOyrB9VIvDSHYD9
6yfXzEwwHwYDVR0jBBgwFoAUqEpqYwR93brm0Tm3pkVl7/Oo7KEwbwYIKwYBBQUH
AQEEYzBhMC4GCCsGAQUFBzABhiJodHRwOi8vb2NzcC5pbnQteDMubGV0c2VuY3J5
cHQub3JnMC8GCCsGAQUFBzAChiNodHRwOi8vY2VydC5pbnQteDMubGV0c2VuY3J5
cHQub3JnLzCCBIUGA1UdEQSCBHwwggR4gg90ZXh0b3J0ZXhlbC5jb22CEnRleHRv
c2J1ZGlzdGFzLmNvbYIXdGV4dG9zY29udGFtaW5hZG9zLmJsb2eCEXRleHRvc2Vu
c29sZmEuY29tghF0ZXh0b3NlcnZpZG9yLmNvbYIWdGV4dG9zdHJhbnNsYXRpb25z
LmNvbYIQdGV4dHBhdHdpdmVzLmNvbYIWdGV4dHBsb2l0YXRpb250ZWZsLmNvbYIM
dGV4dHJoZXQuY29tgg50ZXh0cm9saW5jLmNvbYISdGV4dHNsYXNocGxhaW4uY29t
gg10ZXh0c3Ryb20uY29tgg90ZXh0c3R5bGVzLmJsb2eCFnRleHR0ZWFzZXJib29r
YmxvZy5jb22CEXRleHR0aGVtZmlyc3QuY29tgh10ZXh0dWFsbHlleHBsaWNpdG1h
dGVyaWFsLmNvbYIZdGV4dHVhbGx5c3BlYWtpbmdibG9nLmNvbYIVdGV4dHVhbHNj
aG9sYXJzaGlwLmV1ghJ0ZXh0dWFsc29jaWV0eS5vcmeCEHRleHR1bmR0aW50ZS5j
b22CFXRleHR1cmFoYWlyZGVzaWduLmNvbYIQdGV4dHVyYWxjaXR5Lm5ldIIWdGV4
dHVyYWxseWluc3BpcmVkLmNvbYINdGV4dHVyZWFsLmNvbYIUdGV4dHVyZWFuZHRh
bm5pbi5jb22CEnRscy5hdXRvbWF0dGljLmNvbYITd3d3LnRleHRvcnRleGVsLmNv
bYIWd3d3LnRleHRvc2J1ZGlzdGFzLmNvbYIbd3d3LnRleHRvc2NvbnRhbWluYWRv
cy5ibG9nghV3d3cudGV4dG9zZW5zb2xmYS5jb22CFXd3dy50ZXh0b3NlcnZpZG9y
LmNvbYIad3d3LnRleHRvc3RyYW5zbGF0aW9ucy5jb22CFHd3dy50ZXh0cGF0d2l2
ZXMuY29tghp3d3cudGV4dHBsb2l0YXRpb250ZWZsLmNvbYIQd3d3LnRleHRyaGV0
LmNvbYISd3d3LnRleHRyb2xpbmMuY29tghZ3d3cudGV4dHNsYXNocGxhaW4uY29t
ghF3d3cudGV4dHN0cm9tLmNvbYITd3d3LnRleHRzdHlsZXMuYmxvZ4Iad3d3LnRl
eHR0ZWFzZXJib29rYmxvZy5jb22CFXd3dy50ZXh0dGhlbWZpcnN0LmNvbYIhd3d3
LnRleHR1YWxseWV4cGxpY2l0bWF0ZXJpYWwuY29tgh13d3cudGV4dHVhbGx5c3Bl
YWtpbmdibG9nLmNvbYIZd3d3LnRleHR1YWxzY2hvbGFyc2hpcC5ldYIWd3d3LnRl
eHR1YWxzb2NpZXR5Lm9yZ4IUd3d3LnRleHR1bmR0aW50ZS5jb22CGXd3dy50ZXh0
dXJhaGFpcmRlc2lnbi5jb22CFHd3dy50ZXh0dXJhbGNpdHkubmV0ghp3d3cudGV4
dHVyYWxseWluc3BpcmVkLmNvbYIRd3d3LnRleHR1cmVhbC5jb22CGHd3dy50ZXh0
dXJlYW5kdGFubmluLmNvbTCB/gYDVR0gBIH2MIHzMAgGBmeBDAECATCB5gYLKwYB
BAGC3xMBAQEwgdYwJgYIKwYBBQUHAgEWGmh0dHA6Ly9jcHMubGV0c2VuY3J5cHQu
b3JnMIGrBggrBgEFBQcCAjCBngyBm1RoaXMgQ2VydGlmaWNhdGUgbWF5IG9ubHkg
YmUgcmVsaWVkIHVwb24gYnkgUmVseWluZyBQYXJ0aWVzIGFuZCBvbmx5IGluIGFj
Y29yZGFuY2Ugd2l0aCB0aGUgQ2VydGlmaWNhdGUgUG9saWN5IGZvdW5kIGF0IGh0
dHBzOi8vbGV0c2VuY3J5cHQub3JnL3JlcG9zaXRvcnkvMIIBAgYKKwYBBAHWeQIE
AgSB8wSB8ADuAHUA23Sv7ssp7LH+yj5xbSzluaq7NveEcYPHXZ1PN7Yfv2QAAAFj
jh91AAAABAMARjBEAiBv3yHUPdjtyikWgemipKGIQYEb96KzHFgv+mszfTwZ7AIg
On2SYTOAYx5QncA9gqEvuJV3V6e4rtSkrwPucP3wu3oAdQApPFGWVMg5ZbqqUPxY
B9S3b79Yeily3KTDDPTlRUf0eAAAAWOOH3UgAAAEAwBGMEQCIGgUIQCdL3t6Yjk9
+y7M4K0MILTIwflVWCYk/jB6zGMbAiABwA4BE7l1ASlGD2rme860yYnaJxt7w2Jj
vHieotReEDANBgkqhkiG9w0BAQsFAAOCAQEAjkEeTigbk8UVBeEs9dXYnTSq26dB
N/Cs2YiwZeZLgsC1Sa2bX06SZqPJn6jkOlAlaMxF3iyxr9u1k/jN6D1zDVeJd8I4
EKu42ew3/rrrd/FC5GxFSGP2Qpl6/8cEvArrtmfAV4YgUEuMG95ZLXst+Tkb84io
ndR7Q6cGy7X3M+47xBL9PkUgDuR2kym1bZ1LQ07W7mybw+1IubG3Cdd2dIwmALGH
mzSfb9+sUZ8HOESobNhLqCL2MMHDID/9sftBkX28jxR4NCZ+PrqW+mG8hi3S5ycg
78g2vuKh7GZjGTwSmWKV0eHRvphhpBZUPqnMXP1B874upIM09ssdNiRgCA==
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIEkjCCA3qgAwIBAgIQCgFBQgAAAVOFc2oLheynCDANBgkqhkiG9w0BAQsFADA/
MSQwIgYDVQQKExtEaWdpdGFsIFNpZ25hdHVyZSBUcnVzdCBDby4xFzAVBgNVBAMT
DkRTVCBSb290IENBIFgzMB4XDTE2MDMxNzE2NDA0NloXDTIxMDMxNzE2NDA0Nlow
SjELMAkGA1UEBhMCVVMxFjAUBgNVBAoTDUxldCdzIEVuY3J5cHQxIzAhBgNVBAMT
GkxldCdzIEVuY3J5cHQgQXV0aG9yaXR5IFgzMIIBIjANBgkqhkiG9w0BAQEFAAOC
AQ8AMIIBCgKCAQEAnNMM8FrlLke3cl03g7NoYzDq1zUmGSXhvb418XCSL7e4S0EF
q6meNQhY7LEqxGiHC6PjdeTm86dicbp5gWAf15Gan/PQeGdxyGkOlZHP/uaZ6WA8
SMx+yk13EiSdRxta67nsHjcAHJyse6cF6s5K671B5TaYucv9bTyWaN8jKkKQDIZ0
Z8h/pZq4UmEUEz9l6YKHy9v6Dlb2honzhT+Xhq+w3Brvaw2VFn3EK6BlspkENnWA
a6xK8xuQSXgvopZPKiAlKQTGdMDQMc2PMTiVFrqoM7hD8bEfwzB/onkxEz0tNvjj
/PIzark5McWvxI0NHWQWM6r6hCm21AvA2H3DkwIDAQABo4IBfTCCAXkwEgYDVR0T
AQH/BAgwBgEB/wIBADAOBgNVHQ8BAf8EBAMCAYYwfwYIKwYBBQUHAQEEczBxMDIG
CCsGAQUFBzABhiZodHRwOi8vaXNyZy50cnVzdGlkLm9jc3AuaWRlbnRydXN0LmNv
bTA7BggrBgEFBQcwAoYvaHR0cDovL2FwcHMuaWRlbnRydXN0LmNvbS9yb290cy9k
c3Ryb290Y2F4My5wN2MwHwYDVR0jBBgwFoAUxKexpHsscfrb4UuQdf/EFWCFiRAw
VAYDVR0gBE0wSzAIBgZngQwBAgEwPwYLKwYBBAGC3xMBAQEwMDAuBggrBgEFBQcC
ARYiaHR0cDovL2Nwcy5yb290LXgxLmxldHNlbmNyeXB0Lm9yZzA8BgNVHR8ENTAz
MDGgL6AthitodHRwOi8vY3JsLmlkZW50cnVzdC5jb20vRFNUUk9PVENBWDNDUkwu
Y3JsMB0GA1UdDgQWBBSoSmpjBH3duubRObemRWXv86jsoTANBgkqhkiG9w0BAQsF
AAOCAQEA3TPXEfNjWDjdGBX7CVW+dla5cEilaUcne8IkCJLxWh9KEik3JHRRHGJo
uM2VcGfl96S8TihRzZvoroed6ti6WqEBmtzw3Wodatg+VyOeph4EYpr/1wXKtx8/
wApIvJSwtmVi4MFU5aMqrSDE6ea73Mj2tcMyo5jMd6jmeWUHK8so/joWUoHOUgwu
X4Po1QYz+3dszkDqMp4fklxBwXRsW10KXzPMTZ+sOPAveyxindmjkW8lGy+QsRlG
PfZ+G6Z6h7mjem0Y+iWlkYcV4PIWL1iwBi8saCbGS5jN2p8M+X+Q7UNKEkROb3N6
KOqkqm57TH2H3eDJAkSnh6/DNFu0Qg==
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIDSjCCAjKgAwIBAgIQRK+wgNajJ7qJMDmGLvhAazANBgkqhkiG9w0BAQUFADA/
MSQwIgYDVQQKExtEaWdpdGFsIFNpZ25hdHVyZSBUcnVzdCBDby4xFzAVBgNVBAMT
DkRTVCBSb290IENBIFgzMB4XDTAwMDkzMDIxMTIxOVoXDTIxMDkzMDE0MDExNVow
PzEkMCIGA1UEChMbRGlnaXRhbCBTaWduYXR1cmUgVHJ1c3QgQ28uMRcwFQYDVQQD
Ew5EU1QgUm9vdCBDQSBYMzCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEB
AN+v6ZdQCINXtMxiZfaQguzH0yxrMMpb7NnDfcdAwRgUi+DoM3ZJKuM/IUmTrE4O
rz5Iy2Xu/NMhD2XSKtkyj4zl93ewEnu1lcCJo6m67XMuegwGMoOifooUMM0RoOEq
OLl5CjH9UL2AZd+3UWODyOKIYepLYYHsUmu5ouJLGiifSKOeDNoJjj4XLh7dIN9b
xiqKqy69cK3FCxolkHRyxXtqqzTWMIn/5WgTe1QLyNau7Fqckh49ZLOMxt+/yUFw
7BZy1SbsOFU5Q9D8/RhcQPGX69Wam40dutolucbY38EVAjqr2m7xPi71XAicPNaD
aeQQmxkqtilX4+U9m5/wAl0CAwEAAaNCMEAwDwYDVR0TAQH/BAUwAwEB/zAOBgNV
HQ8BAf8EBAMCAQYwHQYDVR0OBBYEFMSnsaR7LHH62+FLkHX/xBVghYkQMA0GCSqG
SIb3DQEBBQUAA4IBAQCjGiybFwBcqR7uKGY3Or+Dxz9LwwmglSBd49lZRNI+DT69
ikugdB/OEIKcdBodfpga3csTS7MgROSR6cz8faXbauX+5v3gTt23ADq1cEmv8uXr
AvHRAosZy5Q6XkjEGB5YGV8eAlrwDPGxrancWYaLbumR9YbK+rlmM6pZW87ipxZz
R8srzJmwN0jP41ZL9c8PDHIyh8bwRLtTcm1D9SZImlJnt1ir/md2cXjbDaJWFBM5
JDGFoqgCWjBH4d1QB7wCCZAA62RjYJsWvIjJEubSfZGL+T0yjWW06XyxV3bqxbYo
Ob8VZRzI9neWagqNdwvYkQsEjgfbKbYK7p2CNTUQ
—–END CERTIFICATE—–
Eric – Is there a way to special case CERT_AUTHORITY_INVALID to CERT_ROOT_AUTHORITY_INVALID for the case where the certificate path is complete and the root certificate would have been OK except that it wasn’t installed in the Trusted Root store?
It’s very deceiving to walk down to the ‘Invalid certificate’, for a Connection Not Private site, look at all the certs in the cert path (in Windows) and not see any warnings. Usually this means the root was not installed in the trusted root store.
Other Chrome specific rules like Symantec_Legacy have a return code that identifies the violation. But there’s no way to explicitly see the problem of the missing trusted root install.
This is probably harder to implement than I imagine. I can see that there’s a problem of sifting out the ‘good’ roots from the ‘nasty’ ones – both of which fail for not being installed in trusted roots.
I would be happy with a utility like cert lint that would help pinpoint the problem too.
For what it’s worth, Windows shows different text on the certificate viewer for the root certificate when it isn’t in the trusted root store.
Incidentally, in case you missed it, I’m now working on Microsoft Edge.
I am using a Lenovo thinkpad with Windows 7 Family
I cannot install Chrome.
I have installed R2 GlobalSign Root Certificate directly in my Trusted Root Certification Authorities.
I visit this GIA G3-specific test page to see if the G3 root is properly trusted in my system and it’s OK.
I always get this error message:
NET::ERR_CERT_AUTHORITY_INVALID
Subject: http://www.google.com
Issuer: Google Internet Authority G3
Expires on: 13 mars 2019
Current date: 27 janv. 2019
PEM encoded chain:—–BEGIN CERTIFICATE—–
MIIDxzCCAq+gAwIBAgIIDq0DYy9e1dEwDQYJKoZIhvcNAQELBQAwVDELMAkGA1UE
BhMCVVMxHjAcBgNVBAoTFUdvb2dsZSBUcnVzdCBTZXJ2aWNlczElMCMGA1UEAxMc
R29vZ2xlIEludGVybmV0IEF1dGhvcml0eSBHMzAeFw0xODEyMTkwODE2MDBaFw0x
OTAzMTMwODE2MDBaMGgxCzAJBgNVBAYTAlVTMRMwEQYDVQQIDApDYWxpZm9ybmlh
MRYwFAYDVQQHDA1Nb3VudGFpbiBWaWV3MRMwEQYDVQQKDApHb29nbGUgTExDMRcw
FQYDVQQDDA53d3cuZ29vZ2xlLmNvbTBZMBMGByqGSM49AgEGCCqGSM49AwEHA0IA
BEv5RxuoqMukxsAtRd5D87z10pj0JZBvEw14GqwFtN979gZcgJeaUwbQ2w4VrQPe
FAnTd1SxThWor+P93J2t4MWjggFSMIIBTjATBgNVHSUEDDAKBggrBgEFBQcDATAO
BgNVHQ8BAf8EBAMCB4AwGQYDVR0RBBIwEIIOd3d3Lmdvb2dsZS5jb20waAYIKwYB
BQUHAQEEXDBaMC0GCCsGAQUFBzAChiFodHRwOi8vcGtpLmdvb2cvZ3NyMi9HVFNH
SUFHMy5jcnQwKQYIKwYBBQUHMAGGHWh0dHA6Ly9vY3NwLnBraS5nb29nL0dUU0dJ
QUczMB0GA1UdDgQWBBSgt0IIK7d/bpToVbC8gzOp6Fw/qjAMBgNVHRMBAf8EAjAA
MB8GA1UdIwQYMBaAFHfCuFCaZ3Z2sS3ChtCDoH6mfrpLMCEGA1UdIAQaMBgwDAYK
KwYBBAHWeQIFAzAIBgZngQwBAgIwMQYDVR0fBCowKDAmoCSgIoYgaHR0cDovL2Ny
bC5wa2kuZ29vZy9HVFNHSUFHMy5jcmwwDQYJKoZIhvcNAQELBQADggEBAKd6Yiud
9vFUkdoF3UnarCqa+DFK6HBz8PrPGUqxHiueeJPj/Y9MAyNGXhTXtnnhh/Ef+8Pd
zmfwDMJFF+r7+i8TKArGTK7Rl2FSQakTZejHWFFRpsnMrHGpzaABRGIZyGEZQAWs
JZqne6vu4e3g+ExhKbHIX3+W519vt5W0nXTNjM7UPTMqWfimmnRhcVb5IjJAhElo
d7Vt4Tybun81jegIeixvpVwSEX2MVg8v/iPdQtvBuDeKThtNcULWGKJLuD3TYlGN
ZjUcMIaFVTfEkZWL6bm2Ff77l7U9njFKPxToEorAAloJtepmiAVflECWYDAYyh0w
UfuSf04Rd2+/U5o=
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIEXDCCA0SgAwIBAgINAeOpMBz8cgY4P5pTHTANBgkqhkiG9w0BAQsFADBMMSAw
HgYDVQQLExdHbG9iYWxTaWduIFJvb3QgQ0EgLSBSMjETMBEGA1UEChMKR2xvYmFs
U2lnbjETMBEGA1UEAxMKR2xvYmFsU2lnbjAeFw0xNzA2MTUwMDAwNDJaFw0yMTEy
MTUwMDAwNDJaMFQxCzAJBgNVBAYTAlVTMR4wHAYDVQQKExVHb29nbGUgVHJ1c3Qg
U2VydmljZXMxJTAjBgNVBAMTHEdvb2dsZSBJbnRlcm5ldCBBdXRob3JpdHkgRzMw
ggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDKUkvqHv/OJGuo2nIYaNVW
XQ5IWi01CXZaz6TIHLGp/lOJ+600/4hbn7vn6AAB3DVzdQOts7G5pH0rJnnOFUAK
71G4nzKMfHCGUksW/mona+Y2emJQ2N+aicwJKetPKRSIgAuPOB6Aahh8Hb2XO3h9
RUk2T0HNouB2VzxoMXlkyW7XUR5mw6JkLHnA52XDVoRTWkNty5oCINLvGmnRsJ1z
ouAqYGVQMc/7sy+/EYhALrVJEA8KbtyX+r8snwU5C1hUrwaW6MWOARa8qBpNQcWT
kaIeoYvy/sGIJEmjR0vFEwHdp1cSaWIr6/4g72n7OqXwfinu7ZYW97EfoOSQJeAz
AgMBAAGjggEzMIIBLzAOBgNVHQ8BAf8EBAMCAYYwHQYDVR0lBBYwFAYIKwYBBQUH
AwEGCCsGAQUFBwMCMBIGA1UdEwEB/wQIMAYBAf8CAQAwHQYDVR0OBBYEFHfCuFCa
Z3Z2sS3ChtCDoH6mfrpLMB8GA1UdIwQYMBaAFJviB1dnHB7AagbeWbSaLd/cGYYu
MDUGCCsGAQUFBwEBBCkwJzAlBggrBgEFBQcwAYYZaHR0cDovL29jc3AucGtpLmdv
b2cvZ3NyMjAyBgNVHR8EKzApMCegJaAjhiFodHRwOi8vY3JsLnBraS5nb29nL2dz
cjIvZ3NyMi5jcmwwPwYDVR0gBDgwNjA0BgZngQwBAgIwKjAoBggrBgEFBQcCARYc
aHR0cHM6Ly9wa2kuZ29vZy9yZXBvc2l0b3J5LzANBgkqhkiG9w0BAQsFAAOCAQEA
HLeJluRT7bvs26gyAZ8so81trUISd7O45skDUmAge1cnxhG1P2cNmSxbWsoiCt2e
ux9LSD+PAj2LIYRFHW31/6xoic1k4tbWXkDCjir37xTTNqRAMPUyFRWSdvt+nlPq
wnb8Oa2I/maSJukcxDjNSfpDh/Bd1lZNgdd/8cLdsE3+wypufJ9uXO1iQpnh9zbu
FIwsIONGl1p3A8CgxkqI/UAih3JaGOqcpcdaCIzkBaR9uYQ1X4k2Vg5APRLouzVy
7a8IVk6wuy6pm+T7HT4LY8ibS5FEZlfAFLSW8NwsVz9SBK2Vqn1N0PIMn5xA6NZV
c7o835DLAFshEWfC7TIe3g==
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIDujCCAqKgAwIBAgILBAAAAAABD4Ym5g0wDQYJKoZIhvcNAQEFBQAwTDEgMB4G
A1UECxMXR2xvYmFsU2lnbiBSb290IENBIC0gUjIxEzARBgNVBAoTCkdsb2JhbFNp
Z24xEzARBgNVBAMTCkdsb2JhbFNpZ24wHhcNMDYxMjE1MDgwMDAwWhcNMjExMjE1
MDgwMDAwWjBMMSAwHgYDVQQLExdHbG9iYWxTaWduIFJvb3QgQ0EgLSBSMjETMBEG
A1UEChMKR2xvYmFsU2lnbjETMBEGA1UEAxMKR2xvYmFsU2lnbjCCASIwDQYJKoZI
hvcNAQEBBQADggEPADCCAQoCggEBAKbPJA6+Lm8omUVCxKs+IVSbC9N/hHD6ErPL
v4dfxn+G07IwXNb9rfF73OX4YJYJkhD10FPe+3t+c4isUoh7SqbKSaZeqKeMWhG8
eoLrvozps6yWJQeXSpkqBy+0Hne/ig+1AnwblrjFuTosvNYSuetZfeLQBoZfXklq
tTleiDTsvHgMCJiEbKjNS7SgfQx5TfC4LcshytVsW33hoCmEofnTlEnLJGKRILzd
C9XZzPnqJworc5HGnRusyMvo4KD0L5CLTfuwNhv2GXqF4G3yYROIXJ/gkwpRl4pa
zq+r1feqCapgvdzZX99yqWATXgAByUr6P6TqBwMhAo6CygPCm48CAwEAAaOBnDCB
mTAOBgNVHQ8BAf8EBAMCAQYwDwYDVR0TAQH/BAUwAwEB/zAdBgNVHQ4EFgQUm+IH
V2ccHsBqBt5ZtJot39wZhi4wNgYDVR0fBC8wLTAroCmgJ4YlaHR0cDovL2NybC5n
bG9iYWxzaWduLm5ldC9yb290LXIyLmNybDAfBgNVHSMEGDAWgBSb4gdXZxwewGoG
3lm0mi3f3BmGLjANBgkqhkiG9w0BAQUFAAOCAQEAmYFThxxol4aR7OBKuEQLq4Gs
J0/WwbgcQ3izDJr86iw8bmEbTUsp9Z8FHSbBuOmDAGJFtqkIk7mpM0sYmsL4h4hO
291xNBrBVNpGP+DTKqttVCL1OmLNIG+6KYnX3ZHu01yiPqFbQfXf5WRDLenVOavS
ot+3i9DAgBkcRcAtjOj4LaR0VknFBbVPFd5uRHg5h6h+u/N5GJG79G+dwfCMNYxd
AfvDbbnvRG15RjF+Cv6pgsH/76tuIMRQyV+dTZsXjAzlAcmgQWpzU/qlULRuJQ/7
TBj0/VLZjmmx6BEP3ojY+x1J96relc8geMJgEtslQIxq/H5COEBkEveegeGTLg==
—–END CERTIFICATE—–
MewTwo: For some reason, your Jan-27 post just showed up in my feed today Feb-24. If you still need help, let me know.
Eric: There’s a year-old problem with how Windows update, rebuilds the permissions on HKLM..Security Certificates>Root>ProtectedRoot for some users (consumer or institutional), that you may want to look at for Anaheim. See CR838707 for details.
NET::ERR_CERT_AUTHORITY_INVALID
Subject: http://www.youtube.com
Issuer: Cisco Umbrella Secondary SubCA hkg-SG
The network you are on is intercepting your traffic using a monster-in-the-middle filter appliance built by Cisco. You’ll need to talk to the network administrator about either removing the filtering or reconfiguring your PC to allow it.
All my browsers (Vivaldi, Chrome, Firefox, IE) are returning the same error when I try to acesse Google services like search and gmail. It is really driving me crazy. I tried everything I found on youtube and other websites but nothing works. Can you help me please?
NET::ERR_CERT_COMMON_NAME_INVALID
Subject: http://www.google.com.br
Issuer: Symantec Class 3 Secure Server CA v30.5.9.1
Expires on: 30 de mar de 2024
Current date: 11 de fev de 2020
This appears to be a fraudulent certificate, which makes me wonder whether you have malware on your computer or network that is causing this. (There’s no such CA as Symantec Class 3 Secure Server CA v30.5.9.1, for instance, and none of these certificates appear in https://crt.sh).
Do you see this error only on Google sites and services, or on all HTTPS sites?
Hi. Just Google.com. My computer has Kaspersky as antivirus and it find 0 malwares when I scan the pc.
What’s the exact URL you’re hitting when you receive this error? Feel free to DM me on Twitter (I messaged you yesterday) and we can troubleshoot together. It absolutely looks like your network is MITM’ing your connection.