You can easily use Fiddler to evaluate what algorithms a client is using to connect to a HTTPS server in Fiddler.
First, adjust Fiddler’s configuration using Tools > Fiddler Options to enable capture of CONNECT tunnels but disable decryption:
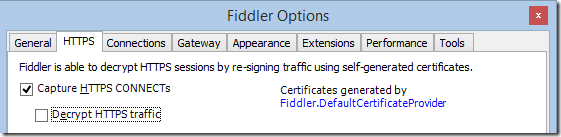
Disabling decryption is necessary because Fiddler decrypts traffic using a HTTPS man-in-the-middle technique, which means that when it’s enabled you’ll see what the client and server are using to talk to Fiddler, which could be different than what they’d use if Fiddler were not in the middle.
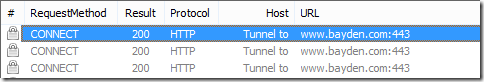
After making this change, simply load a HTTPS site inside your browser, and double-click on any of the CONNECT tunnel entries shown in Fiddler:
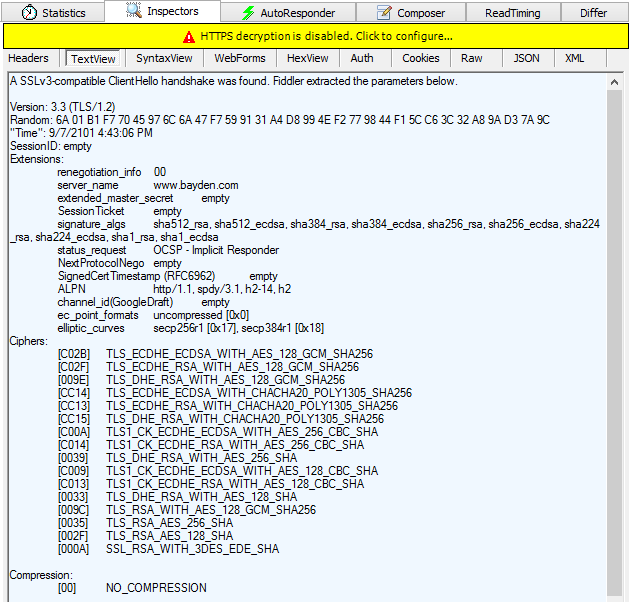
Fiddler’s TextView Request Inspector will show you a parsed view of the Client’s HTTPS handshake:
… and the TextView Response Inspector below will show the parameters chosen by the server for the connection:
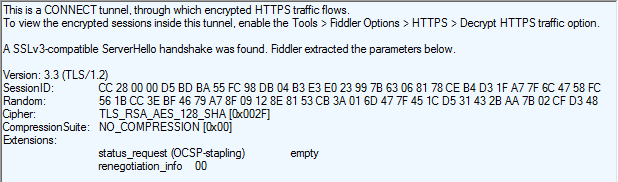
In this case, you can see that the Server agreed to a TLS/1.2 connection using RSA for key exchange and 128-bit AES as the symmetric encryption algorithm. The server ignored the ALPN extension indicating that the connection will not be using HTTP2 or SPDY for data transfers.
Fiddler will show you exactly what your client and server agreed upon. If you’re interested in exploring what other clients with other options might negotiate, the SSLLabs Server Test is a great tool. Similarly, if you’re curious about the capabilities of your browser, check out the SSLLabs Client Test.
-Eric