In yesterday’s post, I outlined the two most successful (and stupid simple) attack techniques that you might not expect to work (and you’d be so very wrong):
- “Please give me your password.”
- “Please run this file.“
Today, let’s explore number 3: “Please give me control of your computer so I can, uh, fix it?“
In this attack, an attacker convinces you that there’s some problem with your computer, your bank account, or something else, and to fix that problem you will need to allow them access to your computer. The Security industry tends to name this Remote Monitoring and Management software scam.
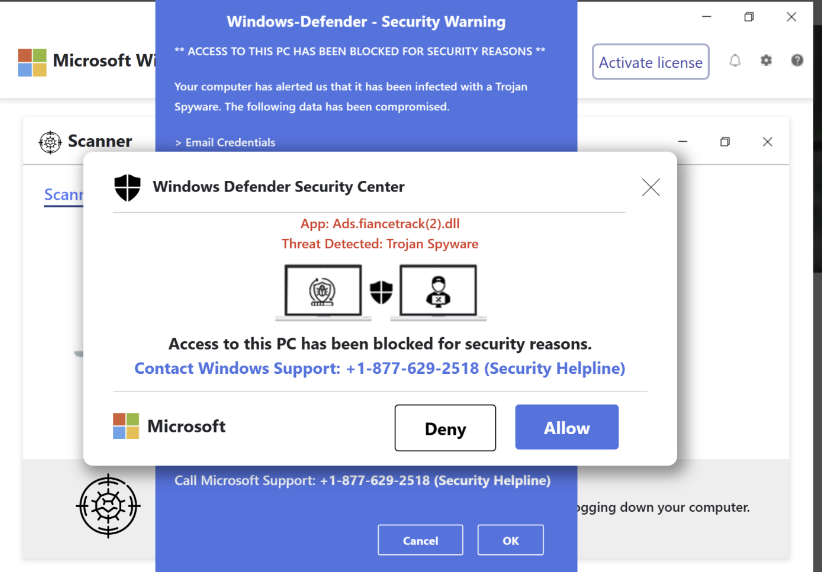
The attacker might start out by sending you SMS text messages or email telling you of a problem, or you might be tricked into calling the attacker when visiting a website takes over your entire screen and blares out a notice saying that “Microsoft” needs you to call them immediately.
Or, the attacker might sign your email address up for a ton of spammy mailing lists, then call you “from your IT department” with the pretext of needing to remotely control your PC “to fix the broken spam filter.”
Once the attacker has you on the hook, they make their move, asking for access to “fix the problem.” The attacker promises “Don’t worry! You can watch everything I’m doing.”
While sometimes the attacker ask you to download some free (and otherwise legitimate) remote control software, lately attackers have been just getting Windows victims to activate the built-in QuickAssist feature included with Windows 10+. Unfortunately, QuickAssist (and similar software) gives the soon-to-be victimized user very little indication of the tremendous risk they’re facing.
I’ve proposed an improvement:
The victim, baited hook already in their mouth and not seeing any clear alternative, figures “Well, they said they’re from my bank or Microsoft, so they are the good guys, right? And they said that I have to act right now or I’ll lose everything! I guess I’ll just watch them very closely.”
Unfortunately for the good people of the world, bad guys need very little skill to be evil while you watch. The attacker follows a script to show you various innocuous-by-scary-seeming information on your PC, lies to you about seeing a major problem that they need to fix, convinces you to push the button to hand over control, and then downloads and runs various malware tools that immediately steal all of your passwords, drain your accounts, and steal and encrypt your files[1]. If your computer has access to a network (e.g. your company), they’ll begin attacking that network using your identity.
What can you do about this scam?
Tell your friends and family that they should never allow anyone they do not personally recognize access to their PC, for any reason. They should never trust emails or SMS messages they receive to be genuine, and should verify any information they receive by calling their financial institution directly, using the contact phone number on their bank card or statement. Microsoft will never call you.
-Eric
[1] An almost completely accurate depiction of this attack can be found in the recent thriller “The Beekeeper.” Unfortunately for the good guys, Jason Statham isn’t waiting on standby to go avenge victims of this all-too-common scam.
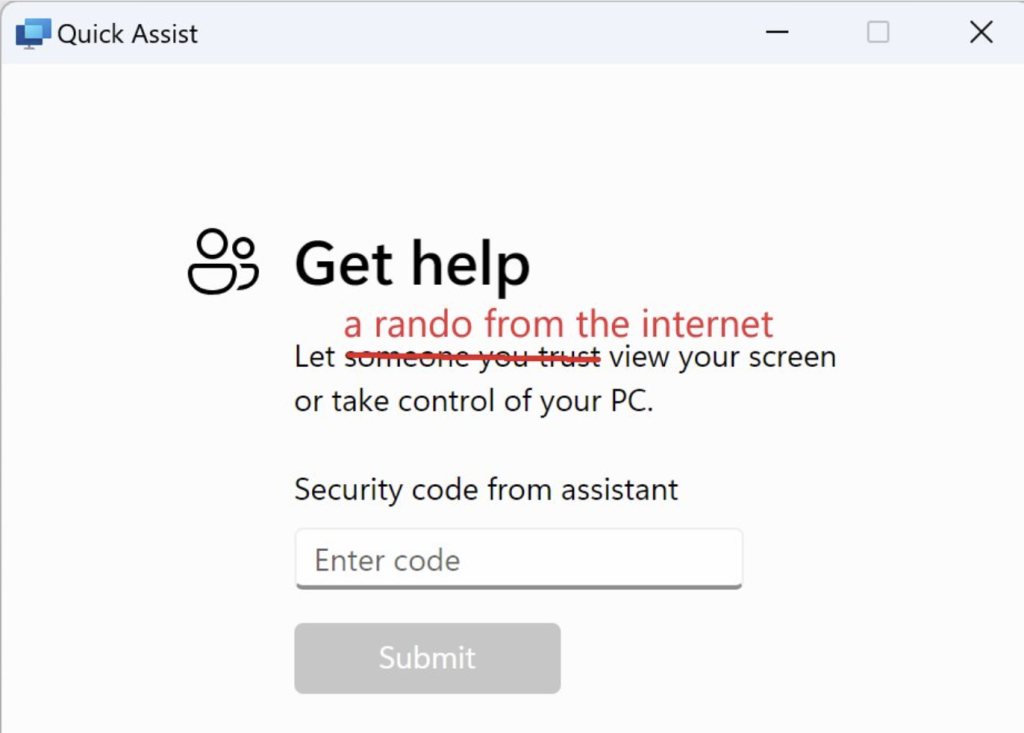
I think that’s a bit extreme… I used Quick Assist many times to help relatives that aren’t computer-savvy. Of course, when I do that I’m always on the phone guiding them through the process, they know without a doubt that it’s me, not a “rando from the internet”.