As of April 30th 2018, Chrome now requires that all certificates issued by a public certificate authority be logged in multiple public Certificate Transparency (CT) logs, ensuring that anyone can audit all certificates that have been issued. (Update: Microsoft Edge 79+ also mandates CT).
CT logs allow site owners and security researchers to much more easily detect if a sloppy or compromised Certificate Authority has issued a certificate in error, because all certificates are published to a public, tamper-proof log that anyone can search. If you see a certificate for a site you own that you didn’t request, someone’s attacking you!
For instance, I own bayden.com, a site where I distribute freeware applications. I definitely want to hear about it if any CA issues a certificate for my site, because that’s a strong indication that my site’s visitors may be under attack. What’s cool is that CT also allows me to detect if someone got a certificate for a domain name that was suspiciously similar to my domain, for instance bȧyden.com.
There are some great tools to examine CT logs; my go-to is crt.sh which is simple and fast. For example, here’s the list of all of the certificates issued covering my domain.
Manual lookups are neat, but to improve security, I still have to actually pay attention to the CT logs, and who’s got time for that? Someone else’s computer, that’s who.
The folks over at Facebook Security have built an easy-to-use interface that allows you to subscribe to notifications any time a domain you care about has a new certificate issued. Just enter a hostname and decide what sorts of alerts you’d like:
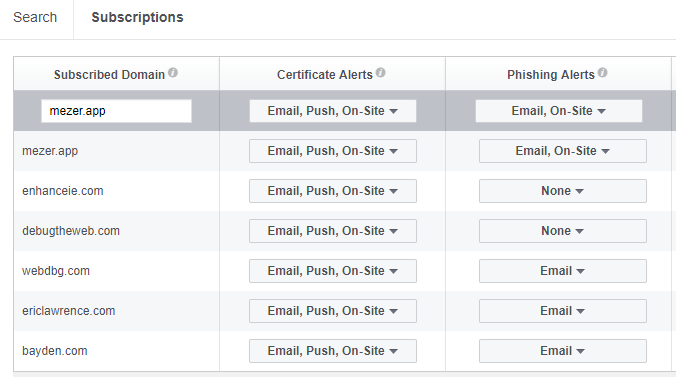
You can even connect their system into webhooks if you’re looking for something more elaborate than email, although mail works just fine for me:
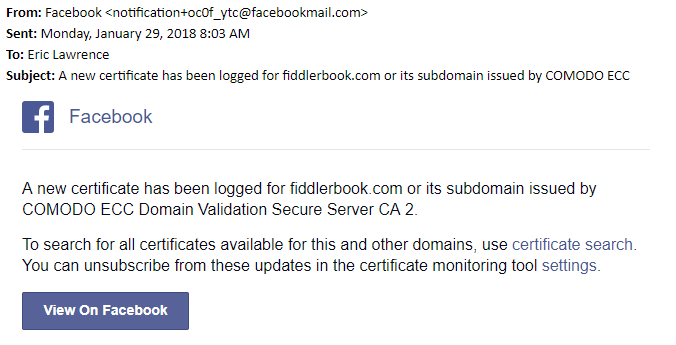
Beyond Facebook, there will likely be many other CT Monitoring services coming online over the next few years. For instance, the good folks at Hardenize have already integrated one into their broader security monitoring platform.
The future is awesome.
-Eric
PS: If you want to reduce the risk of a rogue certificate in the first place, consider opting-in to Certificate Authority Authorization, a mechanism that declares which CAs are allowed to issue certificates for your site.