Sometimes, when you try to load a HTTPS address in Chrome, instead of the expected page, you get a scary warning, like this one:
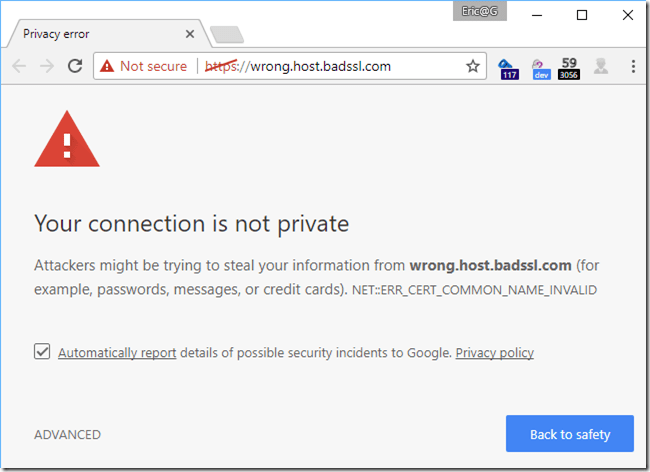
Chrome has found a problem with the security of the connection and has blocked loading the page to protect your information.
In a lot of cases, if you’re just surfing around, the easiest thing to do is just find a different page to visit. But what happens if this happens on an important site that you really need to see? You shouldn’t just “click through” the error, because this could put your device or information at risk.
In some cases, clicking the ADVANCED link might explain more about the problem. For instance, in this example, the error message says that the site is sending the wrong certificate; you might try finding a different link to the site using your favorite search engine.

Or, in this case, Chrome explains that the certificate has expired, and asks you to verify that your computer clock’s Date and Time are set correctly:

You can see the specific error code in the middle of the text:
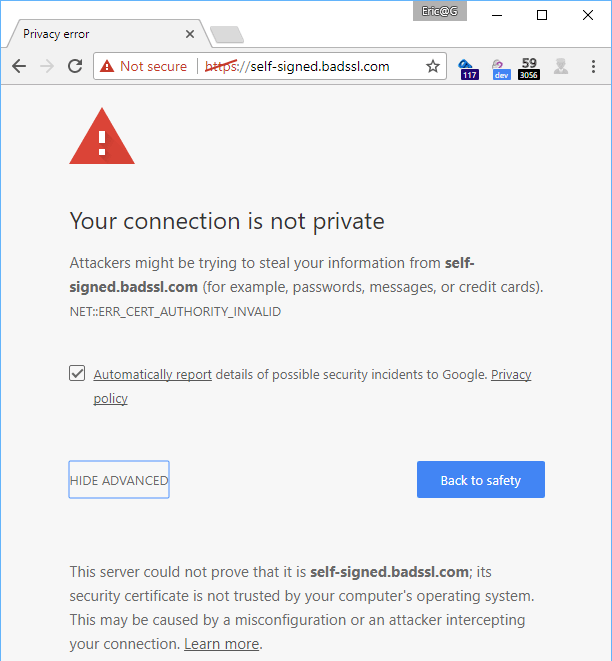
Some types of errors are a bit more confusing. For instance, NET::ERR_CERT_AUTHORITY_INVALID means that the site’s certificate didn’t come from a company that your computer is configured to trust.
Google Internet Authority G3?
If the root certificate is from Google Internet Authority G3, see this article.
Errors Everywhere?
What happens if you start encountering errors like this on every HTTPS page that you visit, even major sites like https://google.com?
In such cases, this often means that you have some software on your device or network that is interfering with your secure connections. Sometimes this software is well-meaning (e.g. anti-virus software, ad-blockers, parental control filters), and sometimes it’s malicious (adware, malware, etc). But even buggy well-meaning software can break your secure connections.
If you know what software is intercepting your traffic (e.g. your antivirus) consider updating it or contacting the vendor.
Getting Help
If you don’t know what to do, you may be able to get help in the Chrome Help Forum. When you ask for help, please include the following information:
- The error code (e.g. NET::ERR_CERT_AUTHORITY_INVALID).
- To help the right people find your issue, consider adding this to the title of your posting.
- What version of Chrome you’re using. Visit chrome://version in your browser to see the version number
- The type of device and network (e.g. “I’m using a laptop on wifi on my school’s network.”)
- The error diagnostic information.
You can get diagnostic information by clicking or tapping directly on the text of the error code: ![]() . When you do so, a bunch of new text will appear in the page:
. When you do so, a bunch of new text will appear in the page:
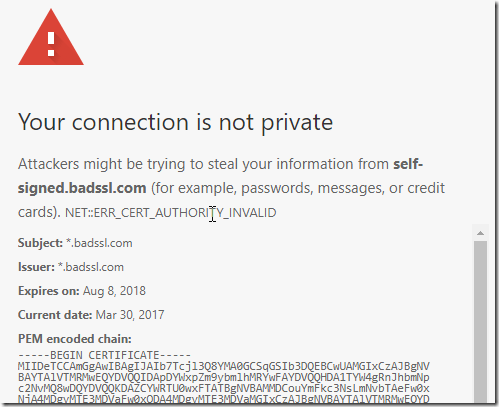
You should select all of the text:
…then hit CTRL+C (or Command ⌘+C on Mac) to copy the text to your clipboard. You can then paste the text into your post. The “PEM encoded chain” information will allow engineers to see exactly what certificate the server sent to your computer, which might shed light on what specifically is interfering with your secure connections.
With any luck, we’ll be able to help you figure out how to surf securely again in no time!
-Eric
NET::ERR_CERT_WEAK_SIGNATURE_ALGORITHM
Subject: *.google.com.sa
Issuer: MS-NMSecurity
Expires on: Jul 26, 2017
Current date: May 17, 2017
PEM encoded chain:
—–BEGIN CERTIFICATE—–
MIICgTCCAeqgAwIBAgIJAN/VkBC2ibcEMA0GCSqGSIb3DQEBBQUAMG0xFjAUBgNV
BAoTDU1TLU5NU2VjdXJpdHkxEDAOBgNVBAcTB015IFRvd24xHDAaBgNVBAgTE1N0
YXRlIG9yIFByb3ZpZGVuY2UxCzAJBgNVBAYTAlVTMRYwFAYDVQQDEw1NUy1OTVNl
Y3VyaXR5MB4XDTE3MDUwMzA4NTg0M1oXDTE3MDcyNjA4NDIwMFowaTELMAkGA1UE
BhMCVVMxEzARBgNVBAgTCkNhbGlmb3JuaWExFjAUBgNVBAcTDU1vdW50YWluIFZp
ZXcxEzARBgNVBAoTCkdvb2dsZSBJbmMxGDAWBgNVBAMUDyouZ29vZ2xlLmNvbS5z
YTCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEA2gQy8K+HCeMA/+NM2V+PBIzw
CqU14ZHxFZ/MNjhtfTkyFuK06pt4v+RtcmHS85gAj32UjNKN/ULLmmhyQQ8JmGQq
xa5l+7Q6lC583Lw/Wwwt/kGignNbi+FPafxvg817bYE7T8sX9rougYRn5KZG7+EI
uoHQMb8O3w1WHvTV82kCAwEAAaMtMCswKQYDVR0RBCIwIIIPKi5nb29nbGUuY29t
LnNhgg1nb29nbGUuY29tLnNhMA0GCSqGSIb3DQEBBQUAA4GBAJpm4xBYnjbuvckc
d/BYRtFcMdP38zxntyihootwxAJV7eHRiwD01dUqDy4qZvsj8Wip5eLUk5eKkvDt
KiAPjhIhsHMBPYCnPMmX4k5X6Xkwst+1ATV65tW1EiIHGRhLH81WwRInqqnMwmCQ
qLPTyEMC2F5oCUikekjzn0TMpUxi
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIDKzCCApSgAwIBAgIJAIWeqUgVaj9xMA0GCSqGSIb3DQEBBQUAMG0xFjAUBgNV
BAoTDU1TLU5NU2VjdXJpdHkxEDAOBgNVBAcTB015IFRvd24xHDAaBgNVBAgTE1N0
YXRlIG9yIFByb3ZpZGVuY2UxCzAJBgNVBAYTAlVTMRYwFAYDVQQDEw1NUy1OTVNl
Y3VyaXR5MB4XDTE0MDIyNjE0MzQ0OVoXDTM0MDIyMTE0MzQ0OVowbTEWMBQGA1UE
ChMNTVMtTk1TZWN1cml0eTEQMA4GA1UEBxMHTXkgVG93bjEcMBoGA1UECBMTU3Rh
dGUgb3IgUHJvdmlkZW5jZTELMAkGA1UEBhMCVVMxFjAUBgNVBAMTDU1TLU5NU2Vj
dXJpdHkwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAKE31vM1/RfDSIvFfs/Q
FUSFx33suY04CEb7lJzSVXw+SaVe0gNqr39UPY83EPWjETqiKdchmDpN+aXbdWQP
Y5C3UQxyy2mRRR3SqWpDFqLhrs9Igrm/i02liJHkBm0EQUf0ybAI6+Q889bibluw
OZV8bqEoubA5GCoJFD6wUBhNAgMBAAGjgdIwgc8wDAYDVR0TBAUwAwEB/zAdBgNV
HQ4EFgQUBut04LCsUqaWjCR7sLjtCQWVg2gwgZ8GA1UdIwSBlzCBlIAUBut04LCs
UqaWjCR7sLjtCQWVg2ihcaRvMG0xFjAUBgNVBAoTDU1TLU5NU2VjdXJpdHkxEDAO
BgNVBAcTB015IFRvd24xHDAaBgNVBAgTE1N0YXRlIG9yIFByb3ZpZGVuY2UxCzAJ
BgNVBAYTAlVTMRYwFAYDVQQDEw1NUy1OTVNlY3VyaXR5ggkAhZ6pSBVqP3EwDQYJ
KoZIhvcNAQEFBQADgYEAJeqOcPiKzeS1Lu5XnPB2PqDS5D3V2Kx9OjXog5uG2krh
bdJbGL0cPLVj+cUN5uGcTKY0T3Zk+6GoH1/pXs4TCbsopRoWYcIk0wW1dG3dMyhv
KXGSS1dVXDW92NXTx/t/0U+Afphwz7LBy4tQOF+ZYaStdjVANrLk5bLaX5h0c/g=
—–END CERTIFICATE—–
This error message indicates that you have some software on your PC (using the name “MS-NMSecurity”) that is intercepting your HTTPS traffic. This is not known or common security software, and other users who have hit this have indicated the problem was removed after running an antivirus scanner that found malware.
This is my “problem”, please help. :)
NET::ERR_CERT_COMMON_NAME_INVALID
Subject: http://www.google.com
Issuer: GeoTrust_Global_CA
Expires on: 31.10.2026.
Current date: 29.05.2017.
PEM encoded chain:
—–BEGIN CERTIFICATE—–
MIIDBzCCAnCgAwIBAgIQ7QkSHjufwodGzre/niKGmDANBgkqhkiG9w0BAQsFADBp
MSUwIwYDVQQLExxJc3N1ZWQgYnkgR2VvVHJ1c3QgR2xvYmFsIENBMREwDwYDVQQK
EwhHZW9UcnVzdDEtMCsGA1UEAx4kAEcAZQBvAFQAcgB1AHMAdABfAEcAbABvAGIA
YQBsAF8AQwBBMB4XDTE1MTAzMTIzMDAwMFoXDTI2MTAzMTIyNTk1OVowUzElMCMG
A1UECxMcSXNzdWVkIGJ5IEdlb1RydXN0IEdsb2JhbCBDQTERMA8GA1UEChMIR2Vv
VHJ1c3QxFzAVBgNVBAMTDnd3dy5nb29nbGUuY29tMIGfMA0GCSqGSIb3DQEBAQUA
A4GNADCBiQKBgQCJprRorCAyfffNTTyM1FIUE0ahJWnVRlf8WZ1mHrhfcrVf48yk
QoEY1diJqs23/ZE5CRy+L23GL9hNajOYeUbt6V8mXYmbb+GqP5pEuIHfuIbysMt2
eUmdEMbY7snsT8sGImvHSjErCOK1Kue6Au4zfeuRS0vws8uube+ZS0eKHQIDAQAB
o4HFMIHCMAwGA1UdEwEB/wQCMAAwEwYDVR0lBAwwCgYIKwYBBQUHAwEwgZwGA1Ud
AQSBlDCBkYAQLFpmW4EFPFlKDnBcEFbgO6FrMGkxJTAjBgNVBAsTHElzc3VlZCBi
eSBHZW9UcnVzdCBHbG9iYWwgQ0ExETAPBgNVBAoTCEdlb1RydXN0MS0wKwYDVQQD
HiQARwBlAG8AVAByAHUAcwB0AF8ARwBsAG8AYgBhAGwAXwBDAEGCEPl/IlwlI1qv
TRlzsH9cKgAwDQYJKoZIhvcNAQELBQADgYEAbfreCLfP8VGoTRRFMMPmTzTYt0fj
0AVT88YXz9AfJQC5SYuYgKNLlX9vlQRYYTfP99XMkxk+dn5Vtmghh7IZWv22cYH0
9wEPmVw0CzX42BygQ1YmuoxPqkl3Cgk0wQb4EpeBniEVf+nquCcN/0AxvOguCk2U
6lGVqLS9ttrdtJk=
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIDIzCCAoygAwIBAgIQ+X8iXCUjWq9NGXOwf1wqADANBgkqhkiG9w0BAQsFADBp
MSUwIwYDVQQLExxJc3N1ZWQgYnkgR2VvVHJ1c3QgR2xvYmFsIENBMREwDwYDVQQK
EwhHZW9UcnVzdDEtMCsGA1UEAx4kAEcAZQBvAFQAcgB1AHMAdABfAEcAbABvAGIA
YQBsAF8AQwBBMB4XDTE1MTAzMTIzMDAwMFoXDTI2MTAzMTIyNTk1OVowaTElMCMG
A1UECxMcSXNzdWVkIGJ5IEdlb1RydXN0IEdsb2JhbCBDQTERMA8GA1UEChMIR2Vv
VHJ1c3QxLTArBgNVBAMeJABHAGUAbwBUAHIAdQBzAHQAXwBHAGwAbwBiAGEAbABf
AEMAQTCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEAowmQcIPBYFHxI/iNhZ5x
tjK1fIOqVNXTBLFyJS8AS34fKQ3aslP3iJmXMgDa7eagD9MPtlELqCkq6YNnqfcD
S0zh+B0T+kfx8gFHO54DfCI4PwsO8yle5sas3NfRvVOGrMZsZyX1Bkzf9/3Fg2CV
tsTG5GvPVscQ0/y45HSJUgcCAwEAAaOByzCByDASBgNVHRMBAf8ECDAGAQH/AgEB
MBMGA1UdJQQMMAoGCCsGAQUFBwMBMIGcBgNVHQEEgZQwgZGAECxaZluBBTxZSg5w
XBBW4DuhazBpMSUwIwYDVQQLExxJc3N1ZWQgYnkgR2VvVHJ1c3QgR2xvYmFsIENB
MREwDwYDVQQKEwhHZW9UcnVzdDEtMCsGA1UEAx4kAEcAZQBvAFQAcgB1AHMAdABf
AEcAbABvAGIAYQBsAF8AQwBBghD5fyJcJSNar00Zc7B/XCoAMA0GCSqGSIb3DQEB
CwUAA4GBAB6zg7v86ESBcpQaDsbrnXEmO/Lw4AUbyIXV/ajDM8KOegbj+dcLjtno
ea76BkKCxz0Ls/fkHwYn0Cvwxv7ndQDpLD3y7c8V/AjYm+ZLT3sZ4Mh7nyoY1pP2
mZeMAxzuJXAooao7AVFfwjSOV10cCH/ErV7DMV0SS76NcmtVBHAr
—–END CERTIFICATE—–
SLADJA– This looks like an attack to me. The certificate you’ve shared is valid for 11 years, meaning that it’s clearly fake. “GeoTrust Global CA” is a legitimate certificate authority, but your certificate comes from “GeoTrust_Global_CA” (note the underscores instead of spaces) which implies to me that this is a fake root certificate that is trying to evade your detection. No legitimate software would do this. Because you’re getting NET::ERR_CERT_COMMON_NAME_INVALID instead of an error about the root certificate not being trusted, this implies to me that malware has altered the certificate store of your computer to trust this fake root certificate. If that’s the case, bad guys can see all of your network traffic, even that which takes place over HTTPS.
You should scan your computer for malware and if you’re not confident that it has been removed, I would probably reinstall the operating system to be sure it was clean.
Subject: *.google.com
Issuer: Superfish, Inc.
Expires on: Aug 30, 2017
Current date: Jun 20, 2017
Superfish is a piece of adware that is installed on your system. It has a severe security vulnerability that will compromise all of your HTTPS browsing in all browsers (not just Chrome) and thus it should be removed immediately. Lenovo makes a tool for cleaning up Superfish @ https://support.lenovo.com/us/en/product_security/superfish_uninstall
You Sir. You are an absolute legend. Thank you so much :)
NET::ERR_CERTIFICATE_TRANSPARENCY_REQUIRED
Subject: http://www.amazon.com
Issuer: Symantec Class 3 Secure Server CA – G4
Expires on: Nov 11, 2017
Current date: Jun 20, 2017
You should only see this if you are running a very outdated version of Chrome. Please try updating and of that doesn’t help, share the version number from the chrome://version page.
Eric: Where can I find tools for inspecting the PEM encoded certs? I’ve been hand copying them into .cer files and viewing them from Windows. This works but is cumbersome. Can you (or someone you know) e-me or post some better tools? SSL Labs?
I usually do the same copy-to-cer approach, but https://lapo.it/asn1js/ is also quite nice.
PEM encoded chain:
—–BEGIN CERTIFICATE—–
MIIDSDCCAjCgAwIBAgIEXsPpaDANBgkqhkiG9w0BAQsFADBAMQ4wDAYDVQQKDAVD
aXNjbzEuMCwGA1UEAwwlQ2lzY28gVW1icmVsbGEgU2Vjb25kYXJ5IFN1YkNBIGhr
Zy1TRzAeFw0yMDA1MTcxNjE0NTJaFw0yMDA1MjIxNjE0NTJaMGwxCzAJBgNVBAYT
AlVTMRMwEQYDVQQIDApDYWxpZm9ybmlhMRYwFAYDVQQHDA1TYW4gRnJhbmNpc2Nv
MRYwFAYDVQQKDA1PcGVuRE5TLCBJbmMuMRgwFgYDVQQDDA93d3cueW91dHViZS5j
b20wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCZzldXw8cIcm3/Mei/
XsULh6AGEbZQ3I2pHDUlhPJrM5I+yEmAlviCJXbfeAVTBgqkYUdUDefT7RWtEMzk
pk8Q9+/k9gf3ThgwR8MQ4kzakay3a/WckzsmDSGBnZpdg/SUVRMyE3ygbeTNRzqd
H3tqZJjNeipjdiwo7YOaIbpoWerieTms2iv+ognjbXkgIK81j46dGIkgfikUwfZs
mhYqZW1Vhx/CRn/rrl1fkOsDjA37A7IZ98G9GhGOMgpQU/u9XxsqBQbZSkj2C2pB
CYtCFOpIChb9N8/IWWugeT0QhKtpQCsIiRDf8gDbIOa//cp52Zsf+ODyoJTq50dj
vNSxAgMBAAGjHjAcMBoGA1UdEQQTMBGCD3d3dy55b3V0dWJlLmNvbTANBgkqhkiG
9w0BAQsFAAOCAQEAhlUzWdFG5aVoAfIdWnU0xjpWbQlK1Zq8svZoTUEyBHgd7Suh
wvTyI2VjZ/bfK59OPYoz/X207taDkFiXHicADS9V4RW3EpLDprxDIIAzcQkIFzka
WRYOg3GsRmWucPN11OBV2WFI59DbZV746ar5AdYlgESQKvWMR17BUhPBdkF3plQ4
a6QVo8l9m0X2nbanR27u8rg6xN/MGDNQDU85SnauLJ4mn0gQ92JtyRDtn7iH9Kkq
fVtFbHDjPpQ32MBfsiiOH3H48qnAICoqWBd0JFzNEO6+fQac6AVy3MWICKKapc+S
quivWHHM3+FlCSWl2NqgpiezsEwIqr36h48dnA==
—–END CERTIFICATE—–
Your network is intercepting your traffic with a Cisco network interception device. You’ll either need to use another network, or work with the IT department of your school or workplace to trust the root certificate the device uses.
Using Chrome version 59.0.3071.109. I’m using a desktop at work, operating on windows 10, using wi-fi. Happens on virtually every single web page I try and has been going on for a month.
NET::ERR_CERT_WEAK_SIGNATURE_ALGORITHM
Subject: *.clinton-county.org
Issuer: Lavasoft Limited
Expires on: Apr 1, 2018
LavaSoft is a company that makes software that interferes with HTTPS traffic (see https://www.kb.cert.org/vuls/id/BLUU-9TWT2Y). To resolve the problems you are having reaching HTTPS sites, you should remove the software that uses LavaSoft certificates. This software likely goes by a number of names (e.g. “Ad-Aware Web Companion”) and should be listed in the Add/Remove Programs application of your system’s control panel.
Thank you! That fixed the problem.
this is my problem please help……………
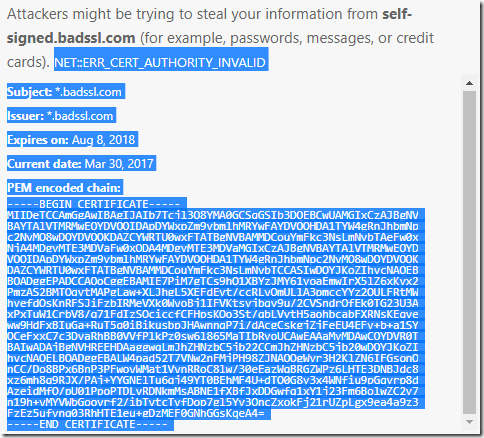
Attackers might be trying to steal your information from http://www.google.co.in (for example, passwords, messages or credit cards). NET::ERR_CERT_WEAK_SIGNATURE_ALGORITHM
Subject: *.google.com
Issuer: Google Internet Authority G2
Expires on: 13 Sep 2017
Current date: 28 Jun 2017
PEM encoded chain:
—–BEGIN CERTIFICATE—–
MIIHijCCBnKgAwIBAgIII/5O0SkE+dEwDQYJKoZIhvcNAQELBQAwSTELMAkGA1UE
BhMCVVMxEzARBgNVBAoTCkdvb2dsZSBJbmMxJTAjBgNVBAMTHEdvb2dsZSBJbnRl
cm5ldCBBdXRob3JpdHkgRzIwHhcNMTcwNjIxMTM1MjAwWhcNMTcwOTEzMTM1MjAw
WjBmMQswCQYDVQQGEwJVUzETMBEGA1UECAwKQ2FsaWZvcm5pYTEWMBQGA1UEBwwN
TW91bnRhaW4gVmlldzETMBEGA1UECgwKR29vZ2xlIEluYzEVMBMGA1UEAwwMKi5n
b29nbGUuY29tMFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAEAfmAbmGJ/B5sfpnE
6Jk3wIQ+tqLjKs0nz8NidhFicNRzy37DZzpIZo9W+yRfNfhUKkF2V0YBJDtCVlDo
1A3sA6OCBSIwggUeMB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjALBgNV
HQ8EBAMCB4AwggPhBgNVHREEggPYMIID1IIMKi5nb29nbGUuY29tgg0qLmFuZHJv
aWQuY29tghYqLmFwcGVuZ2luZS5nb29nbGUuY29tghIqLmNsb3VkLmdvb2dsZS5j
b22CFCouZGI4MzM5NTMuZ29vZ2xlLmNuggYqLmcuY2+CDiouZ2NwLmd2dDIuY29t
ghYqLmdvb2dsZS1hbmFseXRpY3MuY29tggsqLmdvb2dsZS5jYYILKi5nb29nbGUu
Y2yCDiouZ29vZ2xlLmNvLmlugg4qLmdvb2dsZS5jby5qcIIOKi5nb29nbGUuY28u
dWuCDyouZ29vZ2xlLmNvbS5hcoIPKi5nb29nbGUuY29tLmF1gg8qLmdvb2dsZS5j
b20uYnKCDyouZ29vZ2xlLmNvbS5jb4IPKi5nb29nbGUuY29tLm14gg8qLmdvb2ds
ZS5jb20udHKCDyouZ29vZ2xlLmNvbS52boILKi5nb29nbGUuZGWCCyouZ29vZ2xl
LmVzggsqLmdvb2dsZS5mcoILKi5nb29nbGUuaHWCCyouZ29vZ2xlLml0ggsqLmdv
b2dsZS5ubIILKi5nb29nbGUucGyCCyouZ29vZ2xlLnB0ghIqLmdvb2dsZWFkYXBp
cy5jb22CDyouZ29vZ2xlYXBpcy5jboIUKi5nb29nbGVjb21tZXJjZS5jb22CESou
Z29vZ2xldmlkZW8uY29tggwqLmdzdGF0aWMuY26CDSouZ3N0YXRpYy5jb22CCiou
Z3Z0MS5jb22CCiouZ3Z0Mi5jb22CFCoubWV0cmljLmdzdGF0aWMuY29tggwqLnVy
Y2hpbi5jb22CECoudXJsLmdvb2dsZS5jb22CFioueW91dHViZS1ub2Nvb2tpZS5j
b22CDSoueW91dHViZS5jb22CFioueW91dHViZWVkdWNhdGlvbi5jb22CByoueXQu
YmWCCyoueXRpbWcuY29tghphbmRyb2lkLmNsaWVudHMuZ29vZ2xlLmNvbYILYW5k
cm9pZC5jb22CG2RldmVsb3Blci5hbmRyb2lkLmdvb2dsZS5jboIcZGV2ZWxvcGVy
cy5hbmRyb2lkLmdvb2dsZS5jboIEZy5jb4IGZ29vLmdsghRnb29nbGUtYW5hbHl0
aWNzLmNvbYIKZ29vZ2xlLmNvbYISZ29vZ2xlY29tbWVyY2UuY29tghhzb3VyY2Uu
YW5kcm9pZC5nb29nbGUuY26CCnVyY2hpbi5jb22CCnd3dy5nb28uZ2yCCHlvdXR1
LmJlggt5b3V0dWJlLmNvbYIUeW91dHViZWVkdWNhdGlvbi5jb22CBXl0LmJlMGgG
CCsGAQUFBwEBBFwwWjArBggrBgEFBQcwAoYfaHR0cDovL3BraS5nb29nbGUuY29t
L0dJQUcyLmNydDArBggrBgEFBQcwAYYfaHR0cDovL2NsaWVudHMxLmdvb2dsZS5j
b20vb2NzcDAdBgNVHQ4EFgQU0zPQmWIDc0P8/bjZ/9XxsZO3yBwwDAYDVR0TAQH/
BAIwADAfBgNVHSMEGDAWgBRK3QYWG7z2aLV29YG2u2IaulqBLzAhBgNVHSAEGjAY
MAwGCisGAQQB1nkCBQEwCAYGZ4EMAQICMDAGA1UdHwQpMCcwJaAjoCGGH2h0dHA6
Ly9wa2kuZ29vZ2xlLmNvbS9HSUFHMi5jcmwwDQYJKoZIhvcNAQELBQADggEBADHI
I/SBZRgV+8AZQapirQX2JIGcvkwgl7+cNabXk8O53eaQVfX+dXNKbTC4pgozG2/Q
3XdHeSbdcEnvhMB9A+EMcC94WQ/v0PoYUd2kFgV7sKAjVcAhNXXjcpZh/UpQBiql
ekrxrOr0ulIxibjxagodhyUGcCalGe7gNrQZ2LFVr6eeJsUXeis2MhExaPemmYan
PtBsGog4EcSYq+3iLf1rpmJZ48ENoCAEn7TSn89Zi5shHYROWTPhuqaI1aWxEZ92
86c4FgQQRR8RKheNfLX5nkJ/AznN+S43TnyfMGmB6cp1mCac2L/UT0u1yx/6lDn7
vARZGK6oEDGXvgbU0Wc=
—–END CERTIFICATE—–
This shows that the server is sending the correct certificate (see https://crt.sh/?id=158683073), but your operating system is building up a trust chain back to a weak root instead of the proper root. This is most commonly seen on Linux systems where the system software is not up-to-date. Please install the Linux updates to resolve this issue.
Thanks a lot its working after updating all install software/lib in my linux system
One more question….
How to update chrome stable version in linux, i have tried so many command but not working .currently in my system chrome Version 48.0.2564.116.
how to update to new version?????
Typically, I believe this is something that your OS package manager will handle. If not, have you tried the Chrome download page?
yes, i tried with chrome download page but it unsuccessful with error “incompatible with this linux system”.
Kumar: FYI: 48.0.2564.116 was released 2/18/16. This predates the UI rework known as Material Design. You’re going to see quite a change at the user level. There have been some significant security additions too. You might want a backup incase the big leap forward doesn’t go smoothly at first.
Kumar: Head over to the Chrome Help Forum https://productforums.google.com/forum/#!forum/chrome with details of your variant of Linux, the update commands and errors and some one will followup with you there.
I don’t have enough details to respond here. Better to pick up the v48 update failure on a serparate thread, in the right arena…
later, Larry
Gogita is having problems with finding software for “Issuer: DO_NOT_TRUST_FiddlerRoot”. Any suggestions where to look?
Forum thread here: https://productforums.google.com/forum/#!topic/chrome/Swgp-L_vn9M
This is a fresh, reformat HD, Win7 and Chrome install.
See her 7/23 post, items 2-9. Looks likes she’s looking in the right places, just not seeing the problem.
Gogita solved the Chrome Connection not private – Issuer: DO_NOT_TRUST_FiddlerRoot, bu doing a Win7 Internet Explorer reset and machine restart. Voila.. She posted the PEM blocks for Fiddler, prior to the reset. It’s the usual bogus 2 cert chain that dead ends at Fiddler. She also mentions the problem only affects google.com and gmail.com; facebook.com is OK.
Do you have any insight as to how the Internet Explorer reset made Chrome healthy? The reset disables the IE add-ons, but we don’t know that there were any. It’s just as likely the Chrome failure was caused by a bad Win7 reload, that finally got healed as a side-effect of the IE reset.
Most likely, when Internet Explorer was reset, it cleared the proxy settings that were pointing the browsers to the malicious proxy on the local PC that was using the FiddlerCore certificates.
PEM encoded chain:
—–BEGIN CERTIFICATE—–
MIIENzCCAx+gAwIBAgIQSjWBeRZ0jdJ4inGLNZFzWzANBgkqhkiG9w0BAQsFADAY
MRYwFAYDVQQDEw0xNzIuMTYuMTEwLjI5MB4XDTE3MDUxNjAwMDAwMFoXDTE4MDYy
MjEyMDAwMFowaTELMAkGA1UEBhMCVVMxEzARBgNVBAgTCkNhbGlmb3JuaWExEzAR
BgNVBAcTCk1lbmxvIFBhcmsxFzAVBgNVBAoTDkZhY2Vib29rLCBJbmMuMRcwFQYD
VQQDDA4qLmZhY2Vib29rLmNvbTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoC
ggEBAMn/e/EDXVmmZgtj5RZ8jX1Z0psbBc6BO0JPVbCAY9vmN5OBEgmBbWGQude0
Oz/oABplSM8CHZ86N63y4EzhX+95C7VCpqdhW6mJ2FZGI+FTYd5+mnoUJC5L0wag
WuBE5niS3z89kAxkHUba8+Uf267uO934KqBTUDni9n5wqX5X/li0S5owwc0Ar25g
IuNXL4Ag2m9vD1KFmeLR/yF371IOQEBuYIM8WKQ4mFKHup3peE83hq0ug9XJxjAL
eJf0wdvKhJ6Sm313lW8G692ZO8Rd9dPq10GQevm/bM1LqZsq2SVYhVAxo9afrPSM
S8FUV+hjBnVA/SQpByUW30uIQr8CAwEAAaOCASowggEmMB0GA1UdDgQWBBS4e9hh
Wi5v4Mh9Zb0eQeIdA84lijCBxwYDVR0RBIG/MIG8gg4qLmZhY2Vib29rLmNvbYIO
Ki54eC5mYmNkbi5uZXSCDioueHouZmJjZG4ubmV0ggxmYWNlYm9vay5jb22CCyou
ZmJzYnguY29tgg4qLnh5LmZiY2RuLm5ldIIOKi5mYWNlYm9vay5uZXSCDyoubWVz
c2VuZ2VyLmNvbYIIKi5mYi5jb22CBmZiLmNvbYILKi5mYmNkbi5uZXSCECoubS5m
YWNlYm9vay5jb22CDW1lc3Nlbmdlci5jb20wDgYDVR0PAQH/BAQDAgWgMB0GA1Ud
JQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjAMBgNVHRMBAf8EAjAAMA0GCSqGSIb3
DQEBCwUAA4IBAQCc+NOpWR3ZWqenZ49ql1FHlsNe9j2/1bKA3BbuFliWj4bfrPKC
pS/T5U6aG1Ul4j8aNjiFePObCYfPXon7zpC0hbXIMw7SJ2zNLtoyGBjWpbdOrNMu
MhP7ejEkmKgyggWQgxnyiOD4LFZbzUgziYUl+3uDeUOJgiwqBvV4BguxznwEb3ZB
W1/WxkglBST5YvdlJWFAJAlf3LA7HxNY9qfKWYrFywcYcZlCsNa2UcNoPpGs41Mv
pGpxglWVcEcI2LUUqLgRfHLXvXauHTbR5jWZ353DPiZ86aNh5/hxZfnumvhXBOD8
C88K+sjI1Dvv16a0kP5eCFqIMXzmlYFlhJwb
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIC0DCCAbigAwIBAgIJAKOG3Pf+UDCaMA0GCSqGSIb3DQEBCwUAMBgxFjAUBgNV
BAMTDTE3Mi4xNi4xMTAuMjkwHhcNMTYwNzI1MjA1OTQ2WhcNMTcwNzI1MjA1OTQ2
WjAYMRYwFAYDVQQDEw0xNzIuMTYuMTEwLjI5MIIBIjANBgkqhkiG9w0BAQEFAAOC
AQ8AMIIBCgKCAQEAzglKK33cfOvqwe+B6czYLRxxvVHS4z/xrsFyyl037tZiYrGC
fCi5D2rGzJPCmIe4eCTZPR4FItdltVVo6LxEmgA1zULCDoCRRYj3IOtsbgwchQmU
FMScqjklY00rC6/dg9avvt/YkQxAj7QWbbHjbX7+OJLffyOX9YNW48vR/aQonMAX
812bzCw+DINh+PtzGRrcDzRPHwhVaQgOteCMo1cus6KLpR1thTaKDhl6hTjpCoTD
CLchh6dBk7aDPxDDP7hu6yH1uNdnUFa0pakf7JiGSJqs3c7Sdbu+qbGEdV/wgQ2U
PLSso1i04RXDLbHWY6pp7QZvZKiw7K0HhgKqOwIDAQABox0wGzAMBgNVHRMEBTAD
AQH/MAsGA1UdDwQEAwICBDANBgkqhkiG9w0BAQsFAAOCAQEAVtj2bBJ75m/yV70y
9kmiM/4aU0C98smi7DyEBBcmMK8tbM2brbhfWVxV8vuFIeCaI1M0uCUkWQTLS6IN
N/z8EfU6OKQib8RI1Xjw3TLD66iHFuHJHFIwWaYHSE3Tmt4Reey04Y6xHbkWhdt6
KGu0wRzI64Wya3tCQoTErAnu10ELmE6Ad//SQ72fZzeubGIoABVuH6gGQ/YqnQr1
NBq8SJY0rvvAU8szPwwVmmyjJi2XT+SXkb+PwvJwn0GmRIMe/lY9kz5YpY0yosRm
BNnbfgmO0x0C1+Xnq6kHgneCCGOhub+U2mS+wbJfpe0P2m0deTrd1zJZRIVX1JKF
2rbZnQ==
—–END CERTIFICATE—–
Workingman: This invalid certificate doesn’t even pretend to be from a valid certificate authority; it claims to be from “172.16.110.29”, which is a private IP address. This suggests that the network is either under (broken) administrative control or hostile (under attack). Based on your email address, I wonder whether this is a school PC running on a network where HTTPS interception software is deliberately installed for content-filtering purposes? If so, you’ll need to talk to the network administrator about installing the proper certificate.
That Ip address is not even in my subnet or vlan. I ended up reloading the machine ( not due to that issue) and still have the same issue, There does not appear anyone else having this issue. I checked DHCP records and there is not a machine with that address in the last 2 weeks. My machine has a static assigned IP. Here is a log from the new reload. Here we love behind Palo Alto firewall /webfilter.
PEM encoded chain:
—–BEGIN CERTIFICATE—–
MIIENzCCAx+gAwIBAgIQRUwrit6J5zB4inGLNZFzWzANBgkqhkiG9w0BAQsFADAY
MRYwFAYDVQQDEw0xNzIuMTYuMTEwLjI5MB4XDTE3MDUxNjAwMDAwMFoXDTE4MDYy
MjEyMDAwMFowaTELMAkGA1UEBhMCVVMxEzARBgNVBAgTCkNhbGlmb3JuaWExEzAR
BgNVBAcTCk1lbmxvIFBhcmsxFzAVBgNVBAoTDkZhY2Vib29rLCBJbmMuMRcwFQYD
VQQDDA4qLmZhY2Vib29rLmNvbTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoC
ggEBAOspqgab9QMG+j5mYxU8Bhfus0ipAg6AgrdRVADvhDMLyCF03jyTcVxUbMzI
Tc66bVM25VhJj7uNPHcBo1pKpXsD6JfU/nG8/9bnQ7o1EdCuz5w3RH1K4l4fXTOg
ViG4qJ5dDDRwhc+yF1Q4/GXfeVt9R4bMzhv7xxAfWHGQuIrZgu/Yehwvbo3Jy5U/
QxMjpvhQ+X5jPr+KCa6b2Jbr5XviY1ZKKtHqaXKKtiOrKw54hOAY5uabyMYgI+/O
qbWb2Fy9eqQbY+hTPHfmjsJr6dbyTR+puSBbvJaa9hNxqZJINxA0yUWWUQUClilI
BqMcFieGOgjH9E2AHkWO5akl9+sCAwEAAaOCASowggEmMB0GA1UdDgQWBBS4e9hh
Wi5v4Mh9Zb0eQeIdA84lijCBxwYDVR0RBIG/MIG8gg4qLmZhY2Vib29rLmNvbYIO
Ki54eC5mYmNkbi5uZXSCDioueHouZmJjZG4ubmV0ggxmYWNlYm9vay5jb22CCyou
ZmJzYnguY29tgg4qLnh5LmZiY2RuLm5ldIIOKi5mYWNlYm9vay5uZXSCDyoubWVz
c2VuZ2VyLmNvbYIIKi5mYi5jb22CBmZiLmNvbYILKi5mYmNkbi5uZXSCECoubS5m
YWNlYm9vay5jb22CDW1lc3Nlbmdlci5jb20wDgYDVR0PAQH/BAQDAgWgMB0GA1Ud
JQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjAMBgNVHRMBAf8EAjAAMA0GCSqGSIb3
DQEBCwUAA4IBAQCUzd8qHD2YIN7wWCLe4SFzC7s6pBeBoQBC6BnQUUNX981MscAd
8neOVba+XqFHgdFeCc+muWahCry+eU9O+Wbjd56BSZXYIItHLIpjp5+TfOZSEPNr
zquT0YSFTqHuUt/4XM+3tS5Drb6syWBVPoT2GVtgiuDLEhwnFBvcYKVKZzvDNaWo
LFP1c4b/4IjGttKyTnGd6yYs/6oPIUhQDGnPWt2LE9FnLTkol8YJbomoUpfMxbrO
Zs1hN2PlsuviSkWJOWmPSaOwEjKQ8PiA1/gatrhQT9csWoNzIaioHLpXNTavVPmI
yQplghkZzRopbKcS5TI3+mwPlYpfvuQSqrHT
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIC0DCCAbigAwIBAgIJAKOG3Pf+UDCaMA0GCSqGSIb3DQEBCwUAMBgxFjAUBgNV
BAMTDTE3Mi4xNi4xMTAuMjkwHhcNMTYwNzI1MjA1OTQ2WhcNMTcwNzI1MjA1OTQ2
WjAYMRYwFAYDVQQDEw0xNzIuMTYuMTEwLjI5MIIBIjANBgkqhkiG9w0BAQEFAAOC
AQ8AMIIBCgKCAQEAzglKK33cfOvqwe+B6czYLRxxvVHS4z/xrsFyyl037tZiYrGC
fCi5D2rGzJPCmIe4eCTZPR4FItdltVVo6LxEmgA1zULCDoCRRYj3IOtsbgwchQmU
FMScqjklY00rC6/dg9avvt/YkQxAj7QWbbHjbX7+OJLffyOX9YNW48vR/aQonMAX
812bzCw+DINh+PtzGRrcDzRPHwhVaQgOteCMo1cus6KLpR1thTaKDhl6hTjpCoTD
CLchh6dBk7aDPxDDP7hu6yH1uNdnUFa0pakf7JiGSJqs3c7Sdbu+qbGEdV/wgQ2U
PLSso1i04RXDLbHWY6pp7QZvZKiw7K0HhgKqOwIDAQABox0wGzAMBgNVHRMEBTAD
AQH/MAsGA1UdDwQEAwICBDANBgkqhkiG9w0BAQsFAAOCAQEAVtj2bBJ75m/yV70y
9kmiM/4aU0C98smi7DyEBBcmMK8tbM2brbhfWVxV8vuFIeCaI1M0uCUkWQTLS6IN
N/z8EfU6OKQib8RI1Xjw3TLD66iHFuHJHFIwWaYHSE3Tmt4Reey04Y6xHbkWhdt6
KGu0wRzI64Wya3tCQoTErAnu10ELmE6Ad//SQ72fZzeubGIoABVuH6gGQ/YqnQr1
NBq8SJY0rvvAU8szPwwVmmyjJi2XT+SXkb+PwvJwn0GmRIMe/lY9kz5YpY0yosRm
BNnbfgmO0x0C1+Xnq6kHgneCCGOhub+U2mS+wbJfpe0P2m0deTrd1zJZRIVX1JKF
2rbZnQ==
—–END CERTIFICATE—–
The “172.16.110.29” string isn’t bound to anything, they could make it say anything they want. I’m not sure exactly what “love behind Palo Alto firewall” means, but yes, firewalls are a common source of interception certificates. If other users on the network aren’t having problems, it suggests that their PCs have been configured to trust the interception certificate, or their computers’ traffic is not being intercepted. You should speak to the network administrator.
And ‘behind Palo Alto firewall /webfilter’ – could be the source of the authentication problem.
Just caught this at the bottom of your last post.
Re: 172.16.*.* : is a reserved address block, used by many millions of independently operated networks, which might be as small as a single computer connected to a home gateway, and are automatically configured in hundreds of millions of devices. They are only intended for use within a private context and traffic that needs to cross the Internet will need to use a different, unique address.
NET::ERR_CERT_AUTHORITY_INVALID
Subject: chrome.google.com
Issuer: Sophos SSL CA_C230764K629H441
Expires on: 30 sept. 2020
Current date: 17 août 2017
PEM encoded chain:
—–BEGIN CERTIFICATE—–
MIIEUTCCAzmgAwIBAgIPAW5sLQtGzP498ITIdCxbMA0GCSqGSIb3DQEBCwUAMIGN
MQswCQYDVQQGEwJHQjEUMBIGA1UECAwLT3hmb3Jkc2hpcmUxDzANBgNVBAoMBlNv
cGhvczEMMAoGA1UECwwDTlNHMSYwJAYDVQQDDB1Tb3Bob3MgU1NMIENBX0MyMzA3
NjRLNjI5SDQ0MTEhMB8GCSqGSIb3DQEJARYSc3VwcG9ydEBzb3Bob3MuY29tMB4X
DTE3MDgxMDEyMzUxMVoXDTIwMDkzMDEyMzUxMVowHDEaMBgGA1UEAwwRY2hyb21l
Lmdvb2dsZS5jb20wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDa+hpm
fHYNdVfwa5bqLpShlwkELHgLYPlzVmH4NyaG3pE+x7FaGetVar3QBejO9TCh3l9W
LxEU398mWzRyuspVY1s+zab6/OtRV+cnhoduMafEZM7RHRUy7Jlv0hTMsnYyJEUC
55YwlV4xraBI68RHvOgqc8whDHbiW9MZG6a0uvyXvkmEv0ZxV+0i+b9BVojuj1tt
v9niGYFIqsB0Yxw4o4n0EE2hBUdDjVm2zQOZ9W9CQJXad0WVj4rAUk7/2ztW6RJg
EmK2fIw35Wk6nsqBHGoC5IVhGuTkwJMHhFSq+rC54i8ZQr4Ge87nTe3t5UVO+M6Y
MVGCaDRuHBbE1y8nAgMBAAGjggEcMIIBGDAMBgNVHRMBAf8EAjAAMIG6BgNVHSME
gbIwga+AFOZtO1r7aJZ6pAbQyNMetVBE5nisoYGTpIGQMIGNMQswCQYDVQQGEwJH
QjEUMBIGA1UECAwLT3hmb3Jkc2hpcmUxDzANBgNVBAoMBlNvcGhvczEMMAoGA1UE
CwwDTlNHMSYwJAYDVQQDDB1Tb3Bob3MgU1NMIENBX0MyMzA3NjRLNjI5SDQ0MTEh
MB8GCSqGSIb3DQEJARYSc3VwcG9ydEBzb3Bob3MuY29tggEBMC0GCWCGSAGG+EIB
DQQgFh5HZW5lcmF0ZWQgYnkgU29waG9zIEhUVFAgUHJveHkwHAYDVR0RBBUwE4IR
Y2hyb21lLmdvb2dsZS5jb20wDQYJKoZIhvcNAQELBQADggEBAJznXOGPfBvwsZOj
w8pVee81DPGJhqiKDF7wk/HJmcd/NoP8CVjvZZknw4EY0poNYcxp+WcQ33ElnxcM
mLrMimgRAwIYC5fG3CI3f7J9+VDItoLGgWxScbT7F4WLHFaCwddKXT1A4Meefdau
Kakkxq3AV3UQRMvWO5FETBXaYuWO1auPNXPTi2MsWCj+SMu32dTwRJrzkCVpLbt+
UlfpHndIYYc3Gjyj5f1o0lTG132GwydUtQbinl7US13Tq64lFFZO3ZGk7d8RebAf
nKyMd6/GF3R9VEUy63fiEqsTZTGOiXWu1STiLZa3/HRmPu6yQy6zBrok/yDDA2fl
VbnSmWs=
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIEiTCCA3GgAwIBAgIBATANBgkqhkiG9w0BAQsFADCBjTELMAkGA1UEBhMCR0Ix
FDASBgNVBAgMC094Zm9yZHNoaXJlMQ8wDQYDVQQKDAZTb3Bob3MxDDAKBgNVBAsM
A05TRzEmMCQGA1UEAwwdU29waG9zIFNTTCBDQV9DMjMwNzY0SzYyOUg0NDExITAf
BgkqhkiG9w0BCQEWEnN1cHBvcnRAc29waG9zLmNvbTAiGA8yMDE1MDgwMTAwMDAw
MFoYDzIwMzYxMjMxMjM1OTU5WjCBjTELMAkGA1UEBhMCR0IxFDASBgNVBAgMC094
Zm9yZHNoaXJlMQ8wDQYDVQQKDAZTb3Bob3MxDDAKBgNVBAsMA05TRzEmMCQGA1UE
AwwdU29waG9zIFNTTCBDQV9DMjMwNzY0SzYyOUg0NDExITAfBgkqhkiG9w0BCQEW
EnN1cHBvcnRAc29waG9zLmNvbTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoC
ggEBANr6GmZ8dg11V/BrluoulKGXCQQseAtg+XNWYfg3JobekT7HsVoZ61VqvdAF
6M71MKHeX1YvERTf3yZbNHK6ylVjWz7Npvr861FX5yeGh24xp8RkztEdFTLsmW/S
FMyydjIkRQLnljCVXjGtoEjrxEe86CpzzCEMduJb0xkbprS6/Je+SYS/RnFX7SL5
v0FWiO6PW22/2eIZgUiqwHRjHDijifQQTaEFR0ONWbbNA5n1b0JAldp3RZWPisBS
Tv/bO1bpEmASYrZ8jDflaTqeyoEcagLkhWEa5OTAkweEVKr6sLniLxlCvgZ7zudN
7e3lRU74zpgxUYJoNG4cFsTXLycCAwEAAaOB7TCB6jAdBgNVHQ4EFgQU5m07Wvto
lnqkBtDI0x61UETmeKwwgboGA1UdIwSBsjCBr4AU5m07WvtolnqkBtDI0x61UETm
eKyhgZOkgZAwgY0xCzAJBgNVBAYTAkdCMRQwEgYDVQQIDAtPeGZvcmRzaGlyZTEP
MA0GA1UECgwGU29waG9zMQwwCgYDVQQLDANOU0cxJjAkBgNVBAMMHVNvcGhvcyBT
U0wgQ0FfQzIzMDc2NEs2MjlINDQxMSEwHwYJKoZIhvcNAQkBFhJzdXBwb3J0QHNv
cGhvcy5jb22CAQEwDAYDVR0TBAUwAwEB/zANBgkqhkiG9w0BAQsFAAOCAQEAC2QH
hRBSGqq8RSdy7i/ad0Fwt1iec+hFqQaYp7Tt52j8dqd4qQVa2UCfxffLRrIHbw6F
gTa5/kRG1k3/WIx2QM957whbTZHcRnyVFZrdFH69s4ji3oV/PXQAJG1m3kGckI3/
gXP55QN6fYup5uxDWoEQuIvpORxbDIAmL7ezq5c44nyxSHGzTvoCtUUBakip28nx
zXj4UbhWEmrzmatuKcFnjw0zlX5w1XVrsooeUez0OoR+vWy4EhXLa1PFeXPHBt7G
fPfqpkfvcFsmnr6QWgYawjiN1PmpkV2Zjf/Ts+xHo3xQglDtkwxdsf2TKLN1Qmzv
lRz7LIrI0z5mJ2B36w==
—–END CERTIFICATE—–
This issue is caused by a Sophos security product, either a local security product installed on your PC or a network-based device running Sophos content-filtering. If you have Sophos installed, you’ll either need to uninstall it or reinstall it. If you are on a managed network with a Sophos security product filtering at the network level, you’ll need to talk to the network administrator about installing the necessary certificate on your PC.
Thank you very much, I’ll ask our IT guys. :)
Iam getting the below error and not able to access any websites on my browser.
Attackers might be trying to steal your information from http://www.bing.com (for example, passwords, messages, or credit cards). Learn more
NET::ERR_CERT_AUTHORITY_INVALID
Subject: Daniel
Issuer: Daniel
Expires on: Sep 7, 2006
Current date: Aug 26, 2017
PEM encoded chain:
—–BEGIN CERTIFICATE—–
MIIDgzCCAuygAwIBAgIBADANBgkqhkiG9w0BAQQFADCBjjELMAkGA1UEBhMCVUEx
EjAQBgNVBAgTCUNhbGlmb25pYTEPMA0GA1UEBxMGSXJ2aW5lMREwDwYDVQQKEwhC
cm9hZGNvbTESMBAGA1UECxMJQnJvYWRiYW5kMQ8wDQYDVQQDEwZEYW5pZWwxIjAg
BgkqhkiG9w0BCQEWE2tpZGluZ0Bicm9hZGNvbS5jb20wHhcNMDYwODA3MjMzMTIx
WhcNMDYwOTA2MjMzMTIxWjCBjjELMAkGA1UEBhMCVUExEjAQBgNVBAgTCUNhbGlm
b25pYTEPMA0GA1UEBxMGSXJ2aW5lMREwDwYDVQQKEwhCcm9hZGNvbTESMBAGA1UE
CxMJQnJvYWRiYW5kMQ8wDQYDVQQDEwZEYW5pZWwxIjAgBgkqhkiG9w0BCQEWE2tp
ZGluZ0Bicm9hZGNvbS5jb20wgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAOoE
anmsp8b0bUKiI7KeSEK0r6jUvKmP/DoPw2bMH8ufU3NrMrUxiqTWYw1hf21T9oZ/
75V1N4KPHE8XXuMLgAaIhBS1ynj2hrzqrK7+uVp+tV7Txwg8w/XoMRacMRLVk94W
eCHwC574sIq54EX0Ah6GmO4D045J4xiT595wB7ztAgMBAAGjge4wgeswHQYDVR0O
BBYEFDTJsJlw8ckQu3dWh5SGlXAQ03ECMIG7BgNVHSMEgbMwgbCAFDTJsJlw8ckQ
u3dWh5SGlXAQ03ECoYGUpIGRMIGOMQswCQYDVQQGEwJVQTESMBAGA1UECBMJQ2Fs
aWZvbmlhMQ8wDQYDVQQHEwZJcnZpbmUxETAPBgNVBAoTCEJyb2FkY29tMRIwEAYD
VQQLEwlCcm9hZGJhbmQxDzANBgNVBAMTBkRhbmllbDEiMCAGCSqGSIb3DQEJARYT
a2lkaW5nQGJyb2FkY29tLmNvbYIBADAMBgNVHRMEBTADAQH/MA0GCSqGSIb3DQEB
BAUAA4GBALLOjmpWnkYw6YZb6pdJroI5kqe91hGF5ggThizb7yWJiOA2rcu1V7Nh
3P+P5T0tfhtkK836/BxTNoKwrqReTA0foDiwePVZoZGShQJSjACLORlephI5bOoN
a3niYZzczetzE886qH55f2puX4Ghflrm3YGvP8qBq/QDdyCpzlTp
—–END CERTIFICATE—–
NET::ERR_CERT_AUTHORITY_INVALID
This started yesterday and now I can’t access Google or my Gmail. Any help in fixing this issue would be greatly appreciated.
Thanks…
Attackers might be trying to steal your information from http://www.google.com (for example, passwords, messages, or credit cards). Learn more
NET::ERR_CERT_AUTHORITY_INVALID
Subject: http://www.google.com
Issuer: Google Internet Authority G3
Expires on: Nov 24, 2017
Current date: Sep 8, 2017
PEM encoded chain:
—–BEGIN CERTIFICATE—–
MIIEjDCCA3SgAwIBAgIILmsD4AVXNOswDQYJKoZIhvcNAQELBQAwVDELMAkGA1UE
BhMCVVMxHjAcBgNVBAoTFUdvb2dsZSBUcnVzdCBTZXJ2aWNlczElMCMGA1UEAxMc
R29vZ2xlIEludGVybmV0IEF1dGhvcml0eSBHMzAeFw0xNzA5MDExMTA4NTVaFw0x
NzExMjQwOTQyMDBaMGgxCzAJBgNVBAYTAlVTMRMwEQYDVQQIDApDYWxpZm9ybmlh
MRYwFAYDVQQHDA1Nb3VudGFpbiBWaWV3MRMwEQYDVQQKDApHb29nbGUgSW5jMRcw
FQYDVQQDDA53d3cuZ29vZ2xlLmNvbTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCC
AQoCggEBAJv7/JwGtdDrjO3dxeDUh+uogbcgIXEde86Kz7kgTepUJMnd7m6ttQj0
OTCK120SqKmDuSLpqjytpWgKbl+aiLtqV8Y0hEkp++Qj3tcBJZ15CceT6ezEGlWh
xo/LB3ISZbyvkIl50l/aVa3F/wVIS/7STYQHJWakjXmqP5UVCxWbNWr5RvXGlZis
EVbmofHBoVcjb4NdUxGtPCurfe5KjL/ipfQVaqPYGf5SV8+nOAhEmjYVOvSK6ihj
Z461aOxDCuP6+nhl90w9aKcjfu6d1JKiuqEYfBUfHzHNc08u7e2uyHxE852sQJo7
m0h5IUJR8TNvoAZgP2Ch5KvZFnJsEBsCAwEAAaOCAUwwggFIMB0GA1UdJQQWMBQG
CCsGAQUFBwMBBggrBgEFBQcDAjAZBgNVHREEEjAQgg53d3cuZ29vZ2xlLmNvbTBo
BggrBgEFBQcBAQRcMFowLQYIKwYBBQUHMAKGIWh0dHA6Ly9wa2kuZ29vZy9nc3Iy
L0dUU0dJQUczLmNydDApBggrBgEFBQcwAYYdaHR0cDovL29jc3AucGtpLmdvb2cv
R1RTR0lBRzMwHQYDVR0OBBYEFGmFXEf+fETC9vNzokyb+62H5VgoMAwGA1UdEwEB
/wQCMAAwHwYDVR0jBBgwFoAUd8K4UJpndnaxLcKG0IOgfqZ+ukswIQYDVR0gBBow
GDAMBgorBgEEAdZ5AgUDMAgGBmeBDAECAjAxBgNVHR8EKjAoMCagJKAihiBodHRw
Oi8vY3JsLnBraS5nb29nL0dUU0dJQUczLmNybDANBgkqhkiG9w0BAQsFAAOCAQEA
VHk095Iic+lF83SkS2fiwTdSG7N7PAnB8QBu+Ao0XFIfNXBqchKq9bJb9vGd/inA
sgN50lEdjmuFNlcBGE+fJs+4Zw/r0ENI7oHoRCQux5X0okWXI/Q0ieCXSJbhXHOV
3pTL3qDLYyr1dAo4wtDxHH3sNYoZo+puuIk3DA5yZ7w9Ld8ddrnytgZKgkQhxj0P
/dlTyBTdpCSEh3P/jsZEtdxw1yKrefJqMlwP8ZK3lPF/d6JJ+NXeCa2aKEFIr9F+
KneaoZK9idUSpv0pYRXKQKaTMUMgHFtWVMiBqN0BU9y8loMx+fzMDUftgSE8+dR9
xyEKQTai3n161CUxkwfhTQ==
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIEXDCCA0SgAwIBAgINAeOpMBz8cgY4P5pTHTANBgkqhkiG9w0BAQsFADBMMSAw
HgYDVQQLExdHbG9iYWxTaWduIFJvb3QgQ0EgLSBSMjETMBEGA1UEChMKR2xvYmFs
U2lnbjETMBEGA1UEAxMKR2xvYmFsU2lnbjAeFw0xNzA2MTUwMDAwNDJaFw0yMTEy
MTUwMDAwNDJaMFQxCzAJBgNVBAYTAlVTMR4wHAYDVQQKExVHb29nbGUgVHJ1c3Qg
U2VydmljZXMxJTAjBgNVBAMTHEdvb2dsZSBJbnRlcm5ldCBBdXRob3JpdHkgRzMw
ggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDKUkvqHv/OJGuo2nIYaNVW
XQ5IWi01CXZaz6TIHLGp/lOJ+600/4hbn7vn6AAB3DVzdQOts7G5pH0rJnnOFUAK
71G4nzKMfHCGUksW/mona+Y2emJQ2N+aicwJKetPKRSIgAuPOB6Aahh8Hb2XO3h9
RUk2T0HNouB2VzxoMXlkyW7XUR5mw6JkLHnA52XDVoRTWkNty5oCINLvGmnRsJ1z
ouAqYGVQMc/7sy+/EYhALrVJEA8KbtyX+r8snwU5C1hUrwaW6MWOARa8qBpNQcWT
kaIeoYvy/sGIJEmjR0vFEwHdp1cSaWIr6/4g72n7OqXwfinu7ZYW97EfoOSQJeAz
AgMBAAGjggEzMIIBLzAOBgNVHQ8BAf8EBAMCAYYwHQYDVR0lBBYwFAYIKwYBBQUH
AwEGCCsGAQUFBwMCMBIGA1UdEwEB/wQIMAYBAf8CAQAwHQYDVR0OBBYEFHfCuFCa
Z3Z2sS3ChtCDoH6mfrpLMB8GA1UdIwQYMBaAFJviB1dnHB7AagbeWbSaLd/cGYYu
MDUGCCsGAQUFBwEBBCkwJzAlBggrBgEFBQcwAYYZaHR0cDovL29jc3AucGtpLmdv
b2cvZ3NyMjAyBgNVHR8EKzApMCegJaAjhiFodHRwOi8vY3JsLnBraS5nb29nL2dz
cjIvZ3NyMi5jcmwwPwYDVR0gBDgwNjA0BgZngQwBAgIwKjAoBggrBgEFBQcCARYc
aHR0cHM6Ly9wa2kuZ29vZy9yZXBvc2l0b3J5LzANBgkqhkiG9w0BAQsFAAOCAQEA
HLeJluRT7bvs26gyAZ8so81trUISd7O45skDUmAge1cnxhG1P2cNmSxbWsoiCt2e
ux9LSD+PAj2LIYRFHW31/6xoic1k4tbWXkDCjir37xTTNqRAMPUyFRWSdvt+nlPq
wnb8Oa2I/maSJukcxDjNSfpDh/Bd1lZNgdd/8cLdsE3+wypufJ9uXO1iQpnh9zbu
FIwsIONGl1p3A8CgxkqI/UAih3JaGOqcpcdaCIzkBaR9uYQ1X4k2Vg5APRLouzVy
7a8IVk6wuy6pm+T7HT4LY8ibS5FEZlfAFLSW8NwsVz9SBK2Vqn1N0PIMn5xA6NZV
c7o835DLAFshEWfC7TIe3g==
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIDujCCAqKgAwIBAgILBAAAAAABD4Ym5g0wDQYJKoZIhvcNAQEFBQAwTDEgMB4G
A1UECxMXR2xvYmFsU2lnbiBSb290IENBIC0gUjIxEzARBgNVBAoTCkdsb2JhbFNp
Z24xEzARBgNVBAMTCkdsb2JhbFNpZ24wHhcNMDYxMjE1MDgwMDAwWhcNMjExMjE1
MDgwMDAwWjBMMSAwHgYDVQQLExdHbG9iYWxTaWduIFJvb3QgQ0EgLSBSMjETMBEG
A1UEChMKR2xvYmFsU2lnbjETMBEGA1UEAxMKR2xvYmFsU2lnbjCCASIwDQYJKoZI
hvcNAQEBBQADggEPADCCAQoCggEBAKbPJA6+Lm8omUVCxKs+IVSbC9N/hHD6ErPL
v4dfxn+G07IwXNb9rfF73OX4YJYJkhD10FPe+3t+c4isUoh7SqbKSaZeqKeMWhG8
eoLrvozps6yWJQeXSpkqBy+0Hne/ig+1AnwblrjFuTosvNYSuetZfeLQBoZfXklq
tTleiDTsvHgMCJiEbKjNS7SgfQx5TfC4LcshytVsW33hoCmEofnTlEnLJGKRILzd
C9XZzPnqJworc5HGnRusyMvo4KD0L5CLTfuwNhv2GXqF4G3yYROIXJ/gkwpRl4pa
zq+r1feqCapgvdzZX99yqWATXgAByUr6P6TqBwMhAo6CygPCm48CAwEAAaOBnDCB
mTAOBgNVHQ8BAf8EBAMCAQYwDwYDVR0TAQH/BAUwAwEB/zAdBgNVHQ4EFgQUm+IH
V2ccHsBqBt5ZtJot39wZhi4wNgYDVR0fBC8wLTAroCmgJ4YlaHR0cDovL2NybC5n
bG9iYWxzaWduLm5ldC9yb290LXIyLmNybDAfBgNVHSMEGDAWgBSb4gdXZxwewGoG
3lm0mi3f3BmGLjANBgkqhkiG9w0BAQUFAAOCAQEAmYFThxxol4aR7OBKuEQLq4Gs
J0/WwbgcQ3izDJr86iw8bmEbTUsp9Z8FHSbBuOmDAGJFtqkIk7mpM0sYmsL4h4hO
291xNBrBVNpGP+DTKqttVCL1OmLNIG+6KYnX3ZHu01yiPqFbQfXf5WRDLenVOavS
ot+3i9DAgBkcRcAtjOj4LaR0VknFBbVPFd5uRHg5h6h+u/N5GJG79G+dwfCMNYxd
AfvDbbnvRG15RjF+Cv6pgsH/76tuIMRQyV+dTZsXjAzlAcmgQWpzU/qlULRuJQ/7
TBj0/VLZjmmx6BEP3ojY+x1J96relc8geMJgEtslQIxq/H5COEBkEveegeGTLg==
—–END CERTIFICATE—–
Jeff– Which version of which Operating System are you using? Do you have any third party security software installed, especially anything like “Comodo Internet Security Essentials”?
OS is Windows 7 Professional with Symantecs Endpoint protection
Hrm. This is a bit surprising. Do you have any pending updates from WindowsUpdate? Are you on a home machine, or one managed by a corporate network administrator?
Chrome Version 61.0.3163.100 (Official Build) (64-bit) on Ubuntu 16.04 trying to open facebook.com, http://www.facebook.com, http//facebook.com & https//facebook.com
—–BEGIN CERTIFICATE—–
MIIH5DCCBsygAwIBAgIQDACZt9eJyfZmJjF+vOp8HDANBgkqhkiG9w0BAQsFADBw
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3
d3cuZGlnaWNlcnQuY29tMS8wLQYDVQQDEyZEaWdpQ2VydCBTSEEyIEhpZ2ggQXNz
dXJhbmNlIFNlcnZlciBDQTAeFw0xNjEyMDkwMDAwMDBaFw0xODAxMjUxMjAwMDBa
MGkxCzAJBgNVBAYTAlVTMRMwEQYDVQQIEwpDYWxpZm9ybmlhMRMwEQYDVQQHEwpN
ZW5sbyBQYXJrMRcwFQYDVQQKEw5GYWNlYm9vaywgSW5jLjEXMBUGA1UEAwwOKi5m
YWNlYm9vay5jb20wWTATBgcqhkjOPQIBBggqhkjOPQMBBwNCAASg8YyvpzmIaFsT
Vg4VFbSnRe8bx+WFPCsE1GWKMTEi6qOS7WSdumWB47YSdtizC0Xx/wooFJxP3HOp
s0ktoHbTo4IFSjCCBUYwHwYDVR0jBBgwFoAUUWj/kK8CB3U8zNllZGKiErhZcjsw
HQYDVR0OBBYEFMuYKIyhcufiMqmaPfINoYFWoRqLMIHHBgNVHREEgb8wgbyCDiou
ZmFjZWJvb2suY29tgg4qLmZhY2Vib29rLm5ldIIIKi5mYi5jb22CCyouZmJjZG4u
bmV0ggsqLmZic2J4LmNvbYIQKi5tLmZhY2Vib29rLmNvbYIPKi5tZXNzZW5nZXIu
Y29tgg4qLnh4LmZiY2RuLm5ldIIOKi54eS5mYmNkbi5uZXSCDioueHouZmJjZG4u
bmV0ggxmYWNlYm9vay5jb22CBmZiLmNvbYINbWVzc2VuZ2VyLmNvbTAOBgNVHQ8B
Af8EBAMCB4AwHQYDVR0lBBYwFAYIKwYBBQUHAwEGCCsGAQUFBwMCMHUGA1UdHwRu
MGwwNKAyoDCGLmh0dHA6Ly9jcmwzLmRpZ2ljZXJ0LmNvbS9zaGEyLWhhLXNlcnZl
ci1nNS5jcmwwNKAyoDCGLmh0dHA6Ly9jcmw0LmRpZ2ljZXJ0LmNvbS9zaGEyLWhh
LXNlcnZlci1nNS5jcmwwTAYDVR0gBEUwQzA3BglghkgBhv1sAQEwKjAoBggrBgEF
BQcCARYcaHR0cHM6Ly93d3cuZGlnaWNlcnQuY29tL0NQUzAIBgZngQwBAgIwgYMG
CCsGAQUFBwEBBHcwdTAkBggrBgEFBQcwAYYYaHR0cDovL29jc3AuZGlnaWNlcnQu
Y29tME0GCCsGAQUFBzAChkFodHRwOi8vY2FjZXJ0cy5kaWdpY2VydC5jb20vRGln
aUNlcnRTSEEySGlnaEFzc3VyYW5jZVNlcnZlckNBLmNydDAMBgNVHRMBAf8EAjAA
MIICsAYKKwYBBAHWeQIEAgSCAqAEggKcApoAdgCkuQmQtBhYFIe7E6LMZ3AKPDWY
BPkb37jjd80OyA3cEAAAAVjl02IEAAAEAwBHMEUCIQDvWFsUeqWE/xwIYcXPvbb5
ExzfHBZTNwfnUf4RPO/lBgIgdOGmr0j7+u8/S+7tfFw71ZEjqpwJELl/sEFuQdPn
pwQBLwCsO5rtf6lnR1cVnm19V1Zy+dmBAJQem97/7KExO3V4LQAAAVjl02IoAAAE
AQEAYvnMV+BfP3Wrk4yFQE/Zx5WsjSabYOpLj1Tj5xFaoVoHdGqLCf/Hi+Vv0IRy
ePKFBCSW0+3eA589+WnCDMwcJlBYeZV8MlvHFZg3a66Uhx/OAvoetb0mCtUpnmIE
UwLX/eMNEvjg2qTH3/33ysCo2l25+/EcR8upF+2KIcmnk5WwaJzfq7cFPQc4Cvcz
mTHasJi/jmVaIaJ9HC50g3dx584TQX26lDLddF/Li4uEbJ7TSopnTzjQdWBtWbMF
h3bcfhFCKaqK2kIJV3bgup5HibEnZ2LPm6lekY072ZFCGM4QYc4ukqzou2JWCRmG
o0dMHJhnvQXpnIQGwATqCD4Q1AB2AFYUBpov18Ls0/XhvUSyPsdGdrm8mRFcwO+U
mFXWidDdAAABWOXTYrkAAAQDAEcwRQIgGhXXbwUO5bD4Ts/Q0gqZwUS2vl/A4Hem
k7ovxl82v9oCIQCbtkflDXbcunY4MAQCbKlnesPGc/nftA84xDhJpxFHWQB3AO5L
vbd1zmC64UJpH6vhnmajD35fsHLYgwDEe4l6qP3LAAABWOXTZBEAAAQDAEgwRgIh
AKubngQoa5Iak8eCOrffH7Xx3AP1NMb5pFw35nt2VSeRAiEA47Kq1UQcDXIEsV+W
nuPd9LM5kpdeu0+TiHKtTLRQr0swDQYJKoZIhvcNAQELBQADggEBADrNSsoonbj1
YGjwy9t9wP9+kZBwrNMO2n5N5fQNhGawkEAX+lXlzgm3TqYlTNi6sCFbPBAErim3
aMVlWuOlctgnjtAdmdWZ4qEONrBLHPGgukDJ3Uen/EC/gwK6KdBCb4Ttp6MMPY1c
hb/ciTLi3QUUU4h4OJWqUjvccBCDs/LydNjKWZZTxLJmxRSmfpyCU3uU2XHHMNlo
8UTIlqZsOtdqhg7/Q/cvMDHDkcI/tqelmg0MD2H9KpcmAvVkwgjn+BVpv5HELl+0
EP0UhYknI1B6LBecJuj7jI26eXZdX35CYkpI/SZA9KK+OYKHh6vCxKqnRZ9ZQUOj
XnIWKQeV5Hg=
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIEsTCCA5mgAwIBAgIQBOHnpNxc8vNtwCtCuF0VnzANBgkqhkiG9w0BAQsFADBs
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3
d3cuZGlnaWNlcnQuY29tMSswKQYDVQQDEyJEaWdpQ2VydCBIaWdoIEFzc3VyYW5j
ZSBFViBSb290IENBMB4XDTEzMTAyMjEyMDAwMFoXDTI4MTAyMjEyMDAwMFowcDEL
MAkGA1UEBhMCVVMxFTATBgNVBAoTDERpZ2lDZXJ0IEluYzEZMBcGA1UECxMQd3d3
LmRpZ2ljZXJ0LmNvbTEvMC0GA1UEAxMmRGlnaUNlcnQgU0hBMiBIaWdoIEFzc3Vy
YW5jZSBTZXJ2ZXIgQ0EwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQC2
4C/CJAbIbQRf1+8KZAayfSImZRauQkCbztyfn3YHPsMwVYcZuU+UDlqUH1VWtMIC
Kq/QmO4LQNfE0DtyyBSe75CxEamu0si4QzrZCwvV1ZX1QK/IHe1NnF9Xt4ZQaJn1
itrSxwUfqJfJ3KSxgoQtxq2lnMcZgqaFD15EWCo3j/018QsIJzJa9buLnqS9UdAn
4t07QjOjBSjEuyjMmqwrIw14xnvmXnG3Sj4I+4G3FhahnSMSTeXXkgisdaScus0X
sh5ENWV/UyU50RwKmmMbGZJ0aAo3wsJSSMs5WqK24V3B3aAguCGikyZvFEohQcft
bZvySC/zA/WiaJJTL17jAgMBAAGjggFJMIIBRTASBgNVHRMBAf8ECDAGAQH/AgEA
MA4GA1UdDwEB/wQEAwIBhjAdBgNVHSUEFjAUBggrBgEFBQcDAQYIKwYBBQUHAwIw
NAYIKwYBBQUHAQEEKDAmMCQGCCsGAQUFBzABhhhodHRwOi8vb2NzcC5kaWdpY2Vy
dC5jb20wSwYDVR0fBEQwQjBAoD6gPIY6aHR0cDovL2NybDQuZGlnaWNlcnQuY29t
L0RpZ2lDZXJ0SGlnaEFzc3VyYW5jZUVWUm9vdENBLmNybDA9BgNVHSAENjA0MDIG
BFUdIAAwKjAoBggrBgEFBQcCARYcaHR0cHM6Ly93d3cuZGlnaWNlcnQuY29tL0NQ
UzAdBgNVHQ4EFgQUUWj/kK8CB3U8zNllZGKiErhZcjswHwYDVR0jBBgwFoAUsT7D
aQP4v0cB1JgmGggC72NkK8MwDQYJKoZIhvcNAQELBQADggEBABiKlYkD5m3fXPwd
aOpKj4PWUS+Na0QWnqxj9dJubISZi6qBcYRb7TROsLd5kinMLYBq8I4g4Xmk/gNH
E+r1hspZcX30BJZr01lYPf7TMSVcGDiEo+afgv2MW5gxTs14nhr9hctJqvIni5ly
/D6q1UEL2tU2ob8cbkdJf17ZSHwD2f2LSaCYJkJA69aSEaRkCldUxPUd1gJea6zu
xICaEnL6VpPX/78whQYwvwt/Tv9XBZ0k7YXDK/umdaisLRbvfXknsuvCnQsH6qqF
0wGjIChBWUMo0oHjqvbsezt3tkBigAVBRQHvFwY+3sAzm2fTYS5yh+Rp/BIAV0Ae
cPUeybQ=
—–END CERTIFICATE—–
This is Facebook’s certificate. You need to include the error code text from above the certificate info for me to provide more guidance on what you should try next.
I hope this is what you’re after . . .
NET::ERR_CERT_AUTHORITY_INVALID
Subject: *.facebook.com
Issuer: DigiCert SHA2 High Assurance Server CA
Expires on: 25 Jan 2018
Current date: 29 Sep 2017
Yes, the NET::ERR_CERT_AUTHORITY_INVALID text is the important bit. This suggests that your OS configuration is not set to properly trust the “DigiCert High Assurance EV Root CA”. Your first step should be to install all available security updates available. If that doesn’t help, the next step would be to try manually updating your certificates (see e.g. http://manpages.ubuntu.com/manpages/zesty/man8/update-ca-certificates.8.html )
Alas, that didn’t do it. All the updates have been run. I ran “sudo update-ca-certificates” and got . . .
Updating certificates in /etc/ssl/certs…
0 added, 0 removed; done.
Running hooks in /etc/ca-certificates/update.d…
Still “Privacy error”. Do I assume that I have to follow this up with Mr & Mrs Ubuntu? If so, why does Firefox work?
Firefox uses its own trusted certificate stores (it does not delegate to the operating system).
If you open chrome://settings/certificates and click the Authorities tab, then scroll down to “org-DigiCert Inc” is there an entry for “DigiCert High Assurance EV Root CA” present? If so, click the dot-dot-dot on the right and choose “Edit”. Are all three checkboxes ticked?
Aha! “Trust this certificate for identifying websites” was not ticked.
It would be wonderful if this advice were attached to the original error message. Were it so, you might not have so much work to do, Eric.
This is a great service. Thank you very much.
Pete: In your orig 9/28 post, you included only 2 cert blocks. There are usually 3. The two you attached are for facebook and it’s issuer DigiCert SHA2 High Assurance Server CA. Both are good. The missing 3rd one is for the issuer to the Server CA cert and is the one referenced by Eric’s last post: “DigiCert High Assurance EV Root CA” The problem may be with the Root CA.
These are my somewhat date and unverified notes on updating libnss in Ubuntu. I don’t think this applies because your problem is only with this one FB cert (at least as reported so far).. Sorry if this is just spam..
Add a line to the sources.list file
sudo vim /etc/apt/sources.list, add:
deb http://security.ubuntu.com/ubuntu trusty-security main
Then run
sudo apt-get update
sudo apt-get upgrade libnss3 (some use: apt-get install libnss3-1d)
Check what you have
sudo spkg-query –list | grep libnss (which may update many packages)
Restart chrome
There were only two certificates. I also had the same problem with corporate Citrix logon page.
Both were fixed by Eric’s fix.
You may be able to shed some light on this: Was the problem with Chrome’s or Ubuntu’s?
Thank you for your advice.
This is very unusual; I’ve never heard of anyone ever having the trust bit unset for a root unexpectedly. I don’t know whether there’s something somewhere in the Ubuntu configuration that can control this, or if it’s only editable through the chrome://settings UI.
Yes, and it was a brand new Ubuntu installation. Thank you again.
Eric: I hope Snoopy’s smiling today. Our two replies of similar content (mine’s just below) have the same timestamp, down to the minute.
Pete: Nice learning exercise. If you had posted the 3rd (Root CA) PEM block with your original post, we might have gotten here quicker too. Was the 3rd block not displayed when you clicked the NET::ERR tag? I often forget to scroll down and grab all the text..
Thank you again, Larry. Check my answer to your post above.
Pete: Re: Only 2 certs and Chrome vs Ubuntu
Chrome uses OS services (Windows, Linux, Mac) for some things. In this case, chrome’s using the OS network stack for transport and the OS certificate management services for authentication. The authentication cert path typically has 3 layers: site cert->Server CA cert->Root CA cert. The problem was the DigiCert Root CA (CertAuthority) cert, with a missing the ‘OK for web site auth’ flag in the OS cert DB. When you go through chrome://settings/certificates, you’re using the chrome GUI to update the underlying OS cert store (? /var/db/crls/ ?).
I can only speculate why the web-site auth flag was not set. Linux/Ubuntu chrome is a well used configuration. It works well for nearly everyone. There must have been something unique in your config history, possibly related to other browsers, security or a setup glitch, that disabled or never set this flag.
Re: Only 2 certs – displayed with the NET::ERR label: When you went to facebook, the cert path authentication flowed from the facebook cert to it’s issuer: DigiCert….Server CA, but was shortstopped from completing the path to a Root CA by the missing ‘OK for use as web-site ID’ flag. At this point, the chrome authentication failed, displayed the NET::ERR_CERT_AUTHORITY_INVALID error, but only had 2 certs (PEM blocks) to present. The undisplayed root cert was another clue about the underlying failure.
Sorry for my responses being out-of-order. I see a question on my email, do some research, compose a reply and often miss the most recent traffic before I hit send..
Larry, you’ve gone to a lot of work on my issue. Thank you so much. Now happy!
Hi!
Pls help!
—–BEGIN CERTIFICATE—–
MIIFsTCCBJmgAwIBAgIDBv3gMA0GCSqGSIb3DQEBCwUAMEcxCzAJBgNVBAYTAlVT
MRYwFAYDVQQKEw1HZW9UcnVzdCBJbmMuMSAwHgYDVQQDExdSYXBpZFNTTCBTSEEy
NTYgQ0EgLSBHMzAeFw0xNTA5MTYwMDMzMDJaFw0xNzA5MTgwNDAzNDVaMIGbMRMw
EQYDVQQLEwpHVDU4MDczMzAyMTEwLwYDVQQLEyhTZWUgd3d3LnJhcGlkc3NsLmNv
bS9yZXNvdXJjZXMvY3BzIChjKTE1MS8wLQYDVQQLEyZEb21haW4gQ29udHJvbCBW
YWxpZGF0ZWQgLSBSYXBpZFNTTChSKTEgMB4GA1UEAxMXc2VhcmNoLmRuc2FkdmFu
dGFnZS5jb20wggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCwktbK5LPl
uxgTMNXpsrnP/FeT474yEim1KqdD/jsQFYIAZKVSbxU2oMqRqWqTSWVGbrOfNGcO
Wm8wt8ZsW74RBDPnmta7TSCmXqMKWYSUOrBSCz9+WKZhubLjLKmfm89sxeoH793b
OABGhdc/DK+fbZC2wnINx7oSV3WrVrq6QlcenOlqlLOiO/ec5CKWy7SEk0ahm0Xj
xwrj2iY/Z3hhcMe7M0g0i7Vy+y6tEak+sMmfCZaq0VYlmQbbCaMjltgXLkJvNYPI
rt/K8ttC5EZuTeVWTeWnY02LIUZT4qsvZQmgwnCQzlumY3gXabH5qgEUGy6NuB2/
lDD9wm+OAO8FH72DwNggfiJWtPnqd8R4oqNrXhoHzl7RPpr6s4siQv7ql4PbCSbY
N/iraMPqJksl+Zi6gjnk1u2MGa6c93lhiea8tTeZgDZV3vpw+IuQC5YW+/ZYlz8V
Np1kkUIl4kp/HptDUTsrA83xNXQ6WuYEzJ/fSHwTg33i559tMIVVwJx5OBRkXC9k
+kvUiWzyEuhUXO6l9tECebrV5YT2wPMc1RZvcxbyWlxqal7KKIzsxKtKYF0FqZ/c
IF2amCHTbS3k+8Rdwl0SOGfFeSdSO4N7MoyGlBAg5GSjC9F96pxkLNZR1BYJauZD
pm/OsouqSYOez1BlMwF//dzyDI/gu3+JXwIDAQABo4IBTzCCAUswHwYDVR0jBBgw
FoAUw5zz/NNGCDS7zkZ/oHxb8+IIy1kwVwYIKwYBBQUHAQEESzBJMB8GCCsGAQUF
BzABhhNodHRwOi8vZ3Yuc3ltY2QuY29tMCYGCCsGAQUFBzAChhpodHRwOi8vZ3Yu
c3ltY2IuY29tL2d2LmNydDAOBgNVHQ8BAf8EBAMCBaAwHQYDVR0lBBYwFAYIKwYB
BQUHAwEGCCsGAQUFBwMCMCIGA1UdEQQbMBmCF3NlYXJjaC5kbnNhZHZhbnRhZ2Uu
Y29tMCsGA1UdHwQkMCIwIKAeoByGGmh0dHA6Ly9ndi5zeW1jYi5jb20vZ3YuY3Js
MAwGA1UdEwEB/wQCMAAwQQYDVR0gBDowODA2BgZngQwBAgEwLDAqBggrBgEFBQcC
ARYeaHR0cHM6Ly93d3cucmFwaWRzc2wuY29tL2xlZ2FsMA0GCSqGSIb3DQEBCwUA
A4IBAQCsluwg3oAwyL6opH9Hjopmc1Ufb12ByI+DG+TglevvvDn/UNa5oxjTo87V
EWqCKrYvzB9AUT62KVtlu8B+J01eo4vLunhZLGxxQW25VMrwmWPF03rAwDNPsP0L
/S5+VmxeCvvXUu/2Hy/K36/xjsezALgKZgigPeyb2gTciXl7PlybDIpM2vDtklBr
nW4JB8j9jb+L8S6sK9JHPv6V++wFvWCR/b82wdaBakgqXmu4Pw/NzolckM9Zkd2f
vD2XalV31iAWQ3hLtBHv/b9zI4C/Y1N3zvp6E1FGCBG2DTWqbS+7iyrlipQ7Ly6U
bER4APY1wPEt+CQcRF/AMyCN/bmS
—–END CERTIFICATE—–
Thanks
This is a certificate for the domain search.dnsadvantage.com which expired on September 17th, 2017. That site does not appear to be available over HTTPS, but “search.dnsadvantage.com” appears to be the name of a virus/malware/adware package that you’ll need to remove from your PC.
i am also similar kind of issue can you please help me on this
NET::ERR_CERT_COMMON_NAME_INVALID
Subject: *.tailorman.com
Issuer: Amazon
Expires on: Oct 1, 2018
Current date: Oct 16, 2017
PEM encoded chain:
—–BEGIN CERTIFICATE—–
MIIEUjCCAzqgAwIBAgIQBB8c9xS17e1YEIUTdXYA0jANBgkqhkiG9w0BAQsFADBG
MQswCQYDVQQGEwJVUzEPMA0GA1UEChMGQW1hem9uMRUwEwYDVQQLEwxTZXJ2ZXIg
Q0EgMUIxDzANBgNVBAMTBkFtYXpvbjAeFw0xNzA5MDEwMDAwMDBaFw0xODEwMDEx
MjAwMDBaMBoxGDAWBgNVBAMMDyoudGFpbG9ybWFuLmNvbTCCASIwDQYJKoZIhvcN
AQEBBQADggEPADCCAQoCggEBAMNkRK3e15OzAwW7LqB65X2a8FQI5C8RdoxuoZ/z
3fbhtam//TykZcVx6cTyZsmzopKdWVzDDYDT24yogpKtZ6F/dfj17lWXmVIg5h23
6NNjHPHJJ2JVODyNOH0JGnkfLa1aPRHB7qI29WScB/WwP8N6sJkT4KIFEKaHl86I
hCOo6nO+WK9dFXAWxZ0VQZsNcC7vbPI+CLWDPmQB6YQc2txHiXW0dFtTFMRSm82N
8j4IoZ0mNJL8RFtHKHPlOudJD91wUC6V3xa1KN6BpbHfbOTA1hzPN7wXracwg4Hd
qxyE9/2UT+rTPWNfY9yDtMGsqQ5davCR/APlYLE7+B5O2pkCAwEAAaOCAWYwggFi
MB8GA1UdIwQYMBaAFFmkZgZSoHuVkjyjlAcnlnRb+T3QMB0GA1UdDgQWBBT/H3e2
c71VwwluLvNyowwNq3etrzAaBgNVHREEEzARgg8qLnRhaWxvcm1hbi5jb20wDgYD
VR0PAQH/BAQDAgWgMB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjA7BgNV
HR8ENDAyMDCgLqAshipodHRwOi8vY3JsLnNjYTFiLmFtYXpvbnRydXN0LmNvbS9z
Y2ExYi5jcmwwEwYDVR0gBAwwCjAIBgZngQwBAgEwdQYIKwYBBQUHAQEEaTBnMC0G
CCsGAQUFBzABhiFodHRwOi8vb2NzcC5zY2ExYi5hbWF6b250cnVzdC5jb20wNgYI
KwYBBQUHMAKGKmh0dHA6Ly9jcnQuc2NhMWIuYW1hem9udHJ1c3QuY29tL3NjYTFi
LmNydDAMBgNVHRMBAf8EAjAAMA0GCSqGSIb3DQEBCwUAA4IBAQArSJh6Qv6Hsx4s
4j6qn/B4BlVysry6yxF2a/0oIKP6KUbeO+ogvDQgL4qoTPk4REcBtCdEuUmU3uVg
OmVDazwzScCXmn0f+uCQHO/uA8eK8WnpMDNPb+jwmaJXguEkRO7694wh4AWYs9in
xX6e3JMux5BW/H/6gxsXXqFpdUHc3eQLGJKnxM8FhgsRtt2Cul4Ne1CMPVMy1NTm
5M11UO4jnQiFYnVPJPEEGRxvqeFclZpvtrlMveoLjlwbHz6CxJrPbtFjYVS6SnAh
2KSSsfsPorSIrE7Hf5exB97gaKElP+fxFxHq3XbaVAyHYtRKSkqz1KjMqhEOwes6
ZczNMOhR
—–END CERTIFICATE—–
What’s the URL of the site you’re trying to load?
this one i have using
tailorman.com
but the thing is, when i am typing the url on browser it is working fine, like tailorman.com or http://www.tailorman.com working fine.
but when redirecting happen i am facing this issue,
like in hangouts , skype or mail when i am click this url this issue is happens.
can you please help me on this
The tailorman server is misconfigured– they are sending a certificate for *.tailorman.com but this does not match “tailorman.com” because the “*.” must match some other text. That’s why https://www.tailorman.com works while https://tailorman.com does not. The website itself must fix this problem.
NET::ERR_CERT_AUTHORITY_INVALID
Subject: mail.google.com
Issuer: Bitdefender Personal CA.Net-Defender
Expires on: 29 déc. 2017
Current date: 18 oct. 2017
@alimargal: The problem is that your “Bitdefender Personal Defender” antivirus program is misconfigured. You will either need to disable its HTTPS inspection feature, reinstall that software, or remove that software.
Hi I’m getting this when trying to access GMail.com
NET::ERR_CERT_AUTHORITY_INVALID
Subject: gmail.com
Issuer: Google Internet Authority G3
Expires on: Jan 2, 2018
Current date: Oct 19, 2017
PEM encoded chain:
—–BEGIN CERTIFICATE—–
MIIEjzCCA3egAwIBAgIIYHg7BLnLREswDQYJKoZIhvcNAQELBQAwVDELMAkGA1UE
BhMCVVMxHjAcBgNVBAoTFUdvb2dsZSBUcnVzdCBTZXJ2aWNlczElMCMGA1UEAxMc
R29vZ2xlIEludGVybmV0IEF1dGhvcml0eSBHMzAeFw0xNzEwMTAxNDQ3MjFaFw0x
ODAxMDIxNDA3MDBaMGMxCzAJBgNVBAYTAlVTMRMwEQYDVQQIDApDYWxpZm9ybmlh
MRYwFAYDVQQHDA1Nb3VudGFpbiBWaWV3MRMwEQYDVQQKDApHb29nbGUgSW5jMRIw
EAYDVQQDDAlnbWFpbC5jb20wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIB
AQDJw/ajOu4fJrG6pQ4T6v20b7VqUBQBF6jnh/PZrND0figDxRssYDSujEZBa6ga
ZYPrV1qaP/ElsWFgCKB63TXxBeltbU2ACx6UuEiTbG/RM/qAg28OV0HyQun0c6oA
SttBkix2AiRtj1csZF3fEbPDUQJXEbelBYhNzYsqC0gncAdzBLaqxOwIvyDwUcYY
aNkITpxPV0yot6VjC4GWZZ3AjUSHyMeaCCzlKOy5xvRUtmx2hxR9bzZTOgSdjn4+
u2K3oXSM+TYmPUD5CrYi/7wdb62H6Yp+aTZxx/9XW98IhfjtIq7OYtxJabSlvfAJ
nRyLSXEz8F1IG+Ng/gHB3Pu7AgMBAAGjggFUMIIBUDAdBgNVHSUEFjAUBggrBgEF
BQcDAQYIKwYBBQUHAwIwIQYDVR0RBBowGIIJZ21haWwuY29tggsqLmdtYWlsLmNv
bTBoBggrBgEFBQcBAQRcMFowLQYIKwYBBQUHMAKGIWh0dHA6Ly9wa2kuZ29vZy9n
c3IyL0dUU0dJQUczLmNydDApBggrBgEFBQcwAYYdaHR0cDovL29jc3AucGtpLmdv
b2cvR1RTR0lBRzMwHQYDVR0OBBYEFG1qAOqmqKuLb/JFKoptn7LXaCDmMAwGA1Ud
EwEB/wQCMAAwHwYDVR0jBBgwFoAUd8K4UJpndnaxLcKG0IOgfqZ+ukswIQYDVR0g
BBowGDAMBgorBgEEAdZ5AgUDMAgGBmeBDAECAjAxBgNVHR8EKjAoMCagJKAihiBo
dHRwOi8vY3JsLnBraS5nb29nL0dUU0dJQUczLmNybDANBgkqhkiG9w0BAQsFAAOC
AQEArCXDmWIqLHHrfaVQ5XjHcYPaAp+5hVvs56dOf2zFU81dQanjlthGATLoiJH3
JU7F+8+0HDO6+WklgPjmcLaDJZ8nHOrRNlwfZJvAQipZuP1m0WFzvdEvZ22tFnJ6
xwcWjA2N2ua5iP18mQoO5ETMsMi/4K9k3EMGLiyymcX6og/xyULKlFfw8xeXwSwN
nfOdAZe7HQ0JEHeyBe8BNzTQySGXIXbhii/MVMqkSAQ7r8cNPYEZMEEZXbGL5pwr
Fy4CWsbhfH4HJ7pkya3M+9Mwbk20JDhkJlTANnDqUm22f5/4wR3HPnMasPpUpyCy
VqGJeINBf9zAComW57MipYw3/Q==
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIEXDCCA0SgAwIBAgINAeOpMBz8cgY4P5pTHTANBgkqhkiG9w0BAQsFADBMMSAw
HgYDVQQLExdHbG9iYWxTaWduIFJvb3QgQ0EgLSBSMjETMBEGA1UEChMKR2xvYmFs
U2lnbjETMBEGA1UEAxMKR2xvYmFsU2lnbjAeFw0xNzA2MTUwMDAwNDJaFw0yMTEy
MTUwMDAwNDJaMFQxCzAJBgNVBAYTAlVTMR4wHAYDVQQKExVHb29nbGUgVHJ1c3Qg
U2VydmljZXMxJTAjBgNVBAMTHEdvb2dsZSBJbnRlcm5ldCBBdXRob3JpdHkgRzMw
ggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDKUkvqHv/OJGuo2nIYaNVW
XQ5IWi01CXZaz6TIHLGp/lOJ+600/4hbn7vn6AAB3DVzdQOts7G5pH0rJnnOFUAK
71G4nzKMfHCGUksW/mona+Y2emJQ2N+aicwJKetPKRSIgAuPOB6Aahh8Hb2XO3h9
RUk2T0HNouB2VzxoMXlkyW7XUR5mw6JkLHnA52XDVoRTWkNty5oCINLvGmnRsJ1z
ouAqYGVQMc/7sy+/EYhALrVJEA8KbtyX+r8snwU5C1hUrwaW6MWOARa8qBpNQcWT
kaIeoYvy/sGIJEmjR0vFEwHdp1cSaWIr6/4g72n7OqXwfinu7ZYW97EfoOSQJeAz
AgMBAAGjggEzMIIBLzAOBgNVHQ8BAf8EBAMCAYYwHQYDVR0lBBYwFAYIKwYBBQUH
AwEGCCsGAQUFBwMCMBIGA1UdEwEB/wQIMAYBAf8CAQAwHQYDVR0OBBYEFHfCuFCa
Z3Z2sS3ChtCDoH6mfrpLMB8GA1UdIwQYMBaAFJviB1dnHB7AagbeWbSaLd/cGYYu
MDUGCCsGAQUFBwEBBCkwJzAlBggrBgEFBQcwAYYZaHR0cDovL29jc3AucGtpLmdv
b2cvZ3NyMjAyBgNVHR8EKzApMCegJaAjhiFodHRwOi8vY3JsLnBraS5nb29nL2dz
cjIvZ3NyMi5jcmwwPwYDVR0gBDgwNjA0BgZngQwBAgIwKjAoBggrBgEFBQcCARYc
aHR0cHM6Ly9wa2kuZ29vZy9yZXBvc2l0b3J5LzANBgkqhkiG9w0BAQsFAAOCAQEA
HLeJluRT7bvs26gyAZ8so81trUISd7O45skDUmAge1cnxhG1P2cNmSxbWsoiCt2e
ux9LSD+PAj2LIYRFHW31/6xoic1k4tbWXkDCjir37xTTNqRAMPUyFRWSdvt+nlPq
wnb8Oa2I/maSJukcxDjNSfpDh/Bd1lZNgdd/8cLdsE3+wypufJ9uXO1iQpnh9zbu
FIwsIONGl1p3A8CgxkqI/UAih3JaGOqcpcdaCIzkBaR9uYQ1X4k2Vg5APRLouzVy
7a8IVk6wuy6pm+T7HT4LY8ibS5FEZlfAFLSW8NwsVz9SBK2Vqn1N0PIMn5xA6NZV
c7o835DLAFshEWfC7TIe3g==
—–END CERTIFICATE—–
T. Shirer: Can you tell me more about the PC in question? This appears to be Google’s new Certificate, which should be trusted by your system automatically. However, this trust process could be interfered with in a number of ways– Is this system running any non-standard security software (e.g. especially Comodo Internet Security) or managed by a Corporate IT department? What OS is it running?
Oops: The intermediate Google Internet Authority – G3 and it’s GlobalSign root cert are both RSA 2048b. Only the mail.google.com cert can be either ECC 256 or RSA 2048
@ERICLAW
can you please Help me, How can I solve this issue,
i need to do any changes in certificate, means certificate pointing or need to do any changes on Apache ?
for this https://tailorman.com
The problem is with the certificate on tailorman.com; its SubjectAltNames include only “*.tailorman.com” but that does not match “tailorman.com” with nothing in front of it. The Certificate Authority should have provided you with a certificate that contains two SubjectAltName fields, both
*.tailorman.comandtailorman.com. The CA (Amazon in this case) should be asked for a new certificate.I”m sorry I may have pasted the Cert from my computer that does not have the problem. This is from a Windows 10 PC with latest build 1703, that can’t use Chrome. It is managed by Corporate IT using BitDefender AV.
Subject: mail.google.com
Issuer: Google Internet Authority G3
Expires on: Jan 2, 2018
Current date: Oct 20, 2017
PEM encoded chain:
—–BEGIN CERTIFICATE—–
MIID4jCCAsqgAwIBAgIIfssVcE7D+3MwDQYJKoZIhvcNAQELBQAwVDELMAkGA1UE
BhMCVVMxHjAcBgNVBAoTFUdvb2dsZSBUcnVzdCBTZXJ2aWNlczElMCMGA1UEAxMc
R29vZ2xlIEludGVybmV0IEF1dGhvcml0eSBHMzAeFw0xNzEwMTAxNTE2MDdaFw0x
ODAxMDIxNDA4MDBaMGkxCzAJBgNVBAYTAlVTMRMwEQYDVQQIDApDYWxpZm9ybmlh
MRYwFAYDVQQHDA1Nb3VudGFpbiBWaWV3MRMwEQYDVQQKDApHb29nbGUgSW5jMRgw
FgYDVQQDDA9tYWlsLmdvb2dsZS5jb20wWTATBgcqhkjOPQIBBggqhkjOPQMBBwNC
AASyX1gg0SkaScPV52f6uoPEU+Gq6PNz/vud0OYw1HlEG/j5/vATf+SX+H5QnJL+
NfENKwJsL6giWavU4OaFp//wo4IBbDCCAWgwHQYDVR0lBBYwFAYIKwYBBQUHAwEG
CCsGAQUFBwMCMAsGA1UdDwQEAwIHgDAsBgNVHREEJTAjgg9tYWlsLmdvb2dsZS5j
b22CEGluYm94Lmdvb2dsZS5jb20waAYIKwYBBQUHAQEEXDBaMC0GCCsGAQUFBzAC
hiFodHRwOi8vcGtpLmdvb2cvZ3NyMi9HVFNHSUFHMy5jcnQwKQYIKwYBBQUHMAGG
HWh0dHA6Ly9vY3NwLnBraS5nb29nL0dUU0dJQUczMB0GA1UdDgQWBBTJlv3c3e4x
jQRJ9fTYrPHbsTT1gDAMBgNVHRMBAf8EAjAAMB8GA1UdIwQYMBaAFHfCuFCaZ3Z2
sS3ChtCDoH6mfrpLMCEGA1UdIAQaMBgwDAYKKwYBBAHWeQIFAzAIBgZngQwBAgIw
MQYDVR0fBCowKDAmoCSgIoYgaHR0cDovL2NybC5wa2kuZ29vZy9HVFNHSUFHMy5j
cmwwDQYJKoZIhvcNAQELBQADggEBAAE5f1xiatYBm6cWNGRfEnI0PKkIOs0Q7mpb
6L907RIwQZJ8+oU23EoYsiq2BzietPwz+M3hzrN5OtjLNsN8sy0fHR3pISTETTfS
6o+lYBx4wi+I9hIeRZl2uJRz4BskYWnU4uUs6JbNQl6Ziq/4spm88zBHJtQgqovd
qdWcKrVsrMQlhyPiof2nWmuqVOLNA6xDCii4/pT9QIVMAMERPybKyy82vHtcYSSr
39DOY4WsE0nRln/JwjiHwVbw/ICtn8AmpZlfPIbXAmKqdMg4Qsy6tWOgu447jg1g
Y7KI+qXoVECzkSMi0Fm/McFP5uzS9t7CJM8i3tiCkxw0A+V9mqA=
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIEXDCCA0SgAwIBAgINAeOpMBz8cgY4P5pTHTANBgkqhkiG9w0BAQsFADBMMSAw
HgYDVQQLExdHbG9iYWxTaWduIFJvb3QgQ0EgLSBSMjETMBEGA1UEChMKR2xvYmFs
U2lnbjETMBEGA1UEAxMKR2xvYmFsU2lnbjAeFw0xNzA2MTUwMDAwNDJaFw0yMTEy
MTUwMDAwNDJaMFQxCzAJBgNVBAYTAlVTMR4wHAYDVQQKExVHb29nbGUgVHJ1c3Qg
U2VydmljZXMxJTAjBgNVBAMTHEdvb2dsZSBJbnRlcm5ldCBBdXRob3JpdHkgRzMw
ggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDKUkvqHv/OJGuo2nIYaNVW
XQ5IWi01CXZaz6TIHLGp/lOJ+600/4hbn7vn6AAB3DVzdQOts7G5pH0rJnnOFUAK
71G4nzKMfHCGUksW/mona+Y2emJQ2N+aicwJKetPKRSIgAuPOB6Aahh8Hb2XO3h9
RUk2T0HNouB2VzxoMXlkyW7XUR5mw6JkLHnA52XDVoRTWkNty5oCINLvGmnRsJ1z
ouAqYGVQMc/7sy+/EYhALrVJEA8KbtyX+r8snwU5C1hUrwaW6MWOARa8qBpNQcWT
kaIeoYvy/sGIJEmjR0vFEwHdp1cSaWIr6/4g72n7OqXwfinu7ZYW97EfoOSQJeAz
AgMBAAGjggEzMIIBLzAOBgNVHQ8BAf8EBAMCAYYwHQYDVR0lBBYwFAYIKwYBBQUH
AwEGCCsGAQUFBwMCMBIGA1UdEwEB/wQIMAYBAf8CAQAwHQYDVR0OBBYEFHfCuFCa
Z3Z2sS3ChtCDoH6mfrpLMB8GA1UdIwQYMBaAFJviB1dnHB7AagbeWbSaLd/cGYYu
MDUGCCsGAQUFBwEBBCkwJzAlBggrBgEFBQcwAYYZaHR0cDovL29jc3AucGtpLmdv
b2cvZ3NyMjAyBgNVHR8EKzApMCegJaAjhiFodHRwOi8vY3JsLnBraS5nb29nL2dz
cjIvZ3NyMi5jcmwwPwYDVR0gBDgwNjA0BgZngQwBAgIwKjAoBggrBgEFBQcCARYc
aHR0cHM6Ly9wa2kuZ29vZy9yZXBvc2l0b3J5LzANBgkqhkiG9w0BAQsFAAOCAQEA
HLeJluRT7bvs26gyAZ8so81trUISd7O45skDUmAge1cnxhG1P2cNmSxbWsoiCt2e
ux9LSD+PAj2LIYRFHW31/6xoic1k4tbWXkDCjir37xTTNqRAMPUyFRWSdvt+nlPq
wnb8Oa2I/maSJukcxDjNSfpDh/Bd1lZNgdd/8cLdsE3+wypufJ9uXO1iQpnh9zbu
FIwsIONGl1p3A8CgxkqI/UAih3JaGOqcpcdaCIzkBaR9uYQ1X4k2Vg5APRLouzVy
7a8IVk6wuy6pm+T7HT4LY8ibS5FEZlfAFLSW8NwsVz9SBK2Vqn1N0PIMn5xA6NZV
c7o835DLAFshEWfC7TIe3g==
—–END CERTIFICATE—–
Please see https://textslashplain.com/2017/10/23/google-internet-authority-g3/ for possible remediation steps.
Please help! I’m using a personal laptop, i use microsoft security essentials for AV protection, and i’ve tried everything!! this has only started in the last couple of days, it affects both chrome and IE so i’m assuming it’s the computer rather than the site itself?
NET::ERR_CERT_AUTHORITY_INVALID
Subject: *.google.ie
Issuer: Google Internet Authority G3
Expires on: Jan 2, 2018
Current date: Oct 22, 2017
PEM encoded chain:
—–BEGIN CERTIFICATE—–
MIIEkTCCA3mgAwIBAgIIFntrMT9eyiswDQYJKoZIhvcNAQELBQAwVDELMAkGA1UE
BhMCVVMxHjAcBgNVBAoTFUdvb2dsZSBUcnVzdCBTZXJ2aWNlczElMCMGA1UEAxMc
R29vZ2xlIEludGVybmV0IEF1dGhvcml0eSBHMzAeFw0xNzEwMTAxNTE1NTNaFw0x
ODAxMDIxNDA4MDBaMGUxCzAJBgNVBAYTAlVTMRMwEQYDVQQIDApDYWxpZm9ybmlh
MRYwFAYDVQQHDA1Nb3VudGFpbiBWaWV3MRMwEQYDVQQKDApHb29nbGUgSW5jMRQw
EgYDVQQDDAsqLmdvb2dsZS5pZTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoC
ggEBAJqx68FiWXFUec1WhRx8mrUcgw94k1nNx6V62ONo0D/g7zjJ0tCcrgaAlxfY
zoNiMpl1hGGI0b+wwquYebEpuddwNL4uN/Gc3DdnOhy5UoOrtg9Ggj9dGuG8tKA4
7nNvO0W0rF0iRJFSi5EVpovz/P0qARjcz/ij4vGZT6fFimZAotGuSpQgmZ0loMrc
E7+dp+5WwFrzYVkzGblmcZOlWVCnA5KublUV5SHnkZgT/sXB9L3pDXTsg7XA2ah8
9igcpd7IJkpiEltDw9+k5quH12gpWzFlOelGsRXKPLzj0i984ywzdFIONvQkokxx
nYYypzhFg+2X3Uo4NsFfNHRByPMCAwEAAaOCAVQwggFQMB0GA1UdJQQWMBQGCCsG
AQUFBwMBBggrBgEFBQcDAjAhBgNVHREEGjAYggsqLmdvb2dsZS5pZYIJZ29vZ2xl
LmllMGgGCCsGAQUFBwEBBFwwWjAtBggrBgEFBQcwAoYhaHR0cDovL3BraS5nb29n
L2dzcjIvR1RTR0lBRzMuY3J0MCkGCCsGAQUFBzABhh1odHRwOi8vb2NzcC5wa2ku
Z29vZy9HVFNHSUFHMzAdBgNVHQ4EFgQUmzd/4R7+7v4sE7BSpCYkiQu7xnowDAYD
VR0TAQH/BAIwADAfBgNVHSMEGDAWgBR3wrhQmmd2drEtwobQg6B+pn66SzAhBgNV
HSAEGjAYMAwGCisGAQQB1nkCBQMwCAYGZ4EMAQICMDEGA1UdHwQqMCgwJqAkoCKG
IGh0dHA6Ly9jcmwucGtpLmdvb2cvR1RTR0lBRzMuY3JsMA0GCSqGSIb3DQEBCwUA
A4IBAQCSVdc4X6GKFXs66ds1WRQW69W9DeMqaiXUGor2OhZ5rxcBVOlsgYkYctnP
2P0hH+uQIXOJ8Gm1eVCqi8zNbQPkhA+V3nloeGW4X0XRQtoMJDrdUoDQZn7xatY4
BXOSPDoMlWQrPo1biXGLCiDhlg+c3u06ChnDRUquzb8b6eRVBbvk8ERSup17rFeY
G7Zo4cvHWVQRHRebp28Qz9q8OrhGxzjMTTHe0ykGIQRdEGYGFtDbjch9wFaXSvHH
4UG0zKOLJJ+n9/MmOeqvhqrGl8B/zZuW0xp47AAfoqQDum/CsrM5Nx7unebzcli7
fAJOEzXEZNBgwljdC8JlQA59j1P6
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIEXDCCA0SgAwIBAgINAeOpMBz8cgY4P5pTHTANBgkqhkiG9w0BAQsFADBMMSAw
HgYDVQQLExdHbG9iYWxTaWduIFJvb3QgQ0EgLSBSMjETMBEGA1UEChMKR2xvYmFs
U2lnbjETMBEGA1UEAxMKR2xvYmFsU2lnbjAeFw0xNzA2MTUwMDAwNDJaFw0yMTEy
MTUwMDAwNDJaMFQxCzAJBgNVBAYTAlVTMR4wHAYDVQQKExVHb29nbGUgVHJ1c3Qg
U2VydmljZXMxJTAjBgNVBAMTHEdvb2dsZSBJbnRlcm5ldCBBdXRob3JpdHkgRzMw
ggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDKUkvqHv/OJGuo2nIYaNVW
XQ5IWi01CXZaz6TIHLGp/lOJ+600/4hbn7vn6AAB3DVzdQOts7G5pH0rJnnOFUAK
71G4nzKMfHCGUksW/mona+Y2emJQ2N+aicwJKetPKRSIgAuPOB6Aahh8Hb2XO3h9
RUk2T0HNouB2VzxoMXlkyW7XUR5mw6JkLHnA52XDVoRTWkNty5oCINLvGmnRsJ1z
ouAqYGVQMc/7sy+/EYhALrVJEA8KbtyX+r8snwU5C1hUrwaW6MWOARa8qBpNQcWT
kaIeoYvy/sGIJEmjR0vFEwHdp1cSaWIr6/4g72n7OqXwfinu7ZYW97EfoOSQJeAz
AgMBAAGjggEzMIIBLzAOBgNVHQ8BAf8EBAMCAYYwHQYDVR0lBBYwFAYIKwYBBQUH
AwEGCCsGAQUFBwMCMBIGA1UdEwEB/wQIMAYBAf8CAQAwHQYDVR0OBBYEFHfCuFCa
Z3Z2sS3ChtCDoH6mfrpLMB8GA1UdIwQYMBaAFJviB1dnHB7AagbeWbSaLd/cGYYu
MDUGCCsGAQUFBwEBBCkwJzAlBggrBgEFBQcwAYYZaHR0cDovL29jc3AucGtpLmdv
b2cvZ3NyMjAyBgNVHR8EKzApMCegJaAjhiFodHRwOi8vY3JsLnBraS5nb29nL2dz
cjIvZ3NyMi5jcmwwPwYDVR0gBDgwNjA0BgZngQwBAgIwKjAoBggrBgEFBQcCARYc
aHR0cHM6Ly9wa2kuZ29vZy9yZXBvc2l0b3J5LzANBgkqhkiG9w0BAQsFAAOCAQEA
HLeJluRT7bvs26gyAZ8so81trUISd7O45skDUmAge1cnxhG1P2cNmSxbWsoiCt2e
ux9LSD+PAj2LIYRFHW31/6xoic1k4tbWXkDCjir37xTTNqRAMPUyFRWSdvt+nlPq
wnb8Oa2I/maSJukcxDjNSfpDh/Bd1lZNgdd/8cLdsE3+wypufJ9uXO1iQpnh9zbu
FIwsIONGl1p3A8CgxkqI/UAih3JaGOqcpcdaCIzkBaR9uYQ1X4k2Vg5APRLouzVy
7a8IVk6wuy6pm+T7HT4LY8ibS5FEZlfAFLSW8NwsVz9SBK2Vqn1N0PIMn5xA6NZV
c7o835DLAFshEWfC7TIe3g==
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIDujCCAqKgAwIBAgILBAAAAAABD4Ym5g0wDQYJKoZIhvcNAQEFBQAwTDEgMB4G
A1UECxMXR2xvYmFsU2lnbiBSb290IENBIC0gUjIxEzARBgNVBAoTCkdsb2JhbFNp
Z24xEzARBgNVBAMTCkdsb2JhbFNpZ24wHhcNMDYxMjE1MDgwMDAwWhcNMjExMjE1
MDgwMDAwWjBMMSAwHgYDVQQLExdHbG9iYWxTaWduIFJvb3QgQ0EgLSBSMjETMBEG
A1UEChMKR2xvYmFsU2lnbjETMBEGA1UEAxMKR2xvYmFsU2lnbjCCASIwDQYJKoZI
hvcNAQEBBQADggEPADCCAQoCggEBAKbPJA6+Lm8omUVCxKs+IVSbC9N/hHD6ErPL
v4dfxn+G07IwXNb9rfF73OX4YJYJkhD10FPe+3t+c4isUoh7SqbKSaZeqKeMWhG8
eoLrvozps6yWJQeXSpkqBy+0Hne/ig+1AnwblrjFuTosvNYSuetZfeLQBoZfXklq
tTleiDTsvHgMCJiEbKjNS7SgfQx5TfC4LcshytVsW33hoCmEofnTlEnLJGKRILzd
C9XZzPnqJworc5HGnRusyMvo4KD0L5CLTfuwNhv2GXqF4G3yYROIXJ/gkwpRl4pa
zq+r1feqCapgvdzZX99yqWATXgAByUr6P6TqBwMhAo6CygPCm48CAwEAAaOBnDCB
mTAOBgNVHQ8BAf8EBAMCAQYwDwYDVR0TAQH/BAUwAwEB/zAdBgNVHQ4EFgQUm+IH
V2ccHsBqBt5ZtJot39wZhi4wNgYDVR0fBC8wLTAroCmgJ4YlaHR0cDovL2NybC5n
bG9iYWxzaWduLm5ldC9yb290LXIyLmNybDAfBgNVHSMEGDAWgBSb4gdXZxwewGoG
3lm0mi3f3BmGLjANBgkqhkiG9w0BAQUFAAOCAQEAmYFThxxol4aR7OBKuEQLq4Gs
J0/WwbgcQ3izDJr86iw8bmEbTUsp9Z8FHSbBuOmDAGJFtqkIk7mpM0sYmsL4h4hO
291xNBrBVNpGP+DTKqttVCL1OmLNIG+6KYnX3ZHu01yiPqFbQfXf5WRDLenVOavS
ot+3i9DAgBkcRcAtjOj4LaR0VknFBbVPFd5uRHg5h6h+u/N5GJG79G+dwfCMNYxd
AfvDbbnvRG15RjF+Cv6pgsH/76tuIMRQyV+dTZsXjAzlAcmgQWpzU/qlULRuJQ/7
TBj0/VLZjmmx6BEP3ojY+x1J96relc8geMJgEtslQIxq/H5COEBkEveegeGTLg==
—–END CERTIFICATE—–
[Comment via email reply to Niall 10/22 10:24am PST email notification] @Eric has the GMail root cert update failure been resolved? Do we know why it’s failing for some users? Obviously it’s working for most users.. butIt’s failed for Win7 (Suhano, Lucia) and Win10 (Shirer #2) Any specific questions I should forward to users?
No, we don’t know specifically why a small number of users are not seeing root certificates updated as expected. New post here: https://textslashplain.com/2017/10/23/google-internet-authority-g3/
NET::ERR_CERT_COMMON_NAME_INVALID
Subject: *.invanto.com
Issuer: Amazon
Expires on: Oct 8, 2018
Current date: Oct 27, 2017
PEM encoded chain: …
On what URL did you encounter this error? The certificate itself looks okay…
This has been going on for nearly 2 days now, this only happens when I try to use certain websites –
youtube, twitter, and tumblr and some miscellaneous sites eg the ones I used to try and troubleshoot this problem. I use a mac and my chrome is up to date. Please help if you can!!
Subject: search.dnsadvantage.com
Issuer: RapidSSL SHA256 CA – G3
Expires on: Sep 18, 2017
Current date: Oct 28, 2017
PEM encoded chain: …
Your computer is infected by a piece of malware called “DNSAdvantage”. You’ll need to obtain a antivirus/malware removal tool to clean out the infection in order to restore proper function.
NET::ERR_CERT_AUTHORITY_INVALID
Subject: mail.google.com
Issuer: Google Internet Authority G3
Expires on: 2018. 1. 9.
Current date: 2017. 10. 28.
PEM encoded chain: …
You’ll need to follow the instructions in https://textslashplain.com/2017/10/23/google-internet-authority-g3/ to get the right intermediate certificate installed. (This should be happening automatically if Windows is properly configured, but various problems in Windows could cause it to fail…)
Please help error as follows
The error code – NET::ERR_CERT_AUTHORITY_INVALID
Version of Chrome
49.0.2623.112 (32-bit)
The type of device and network- laptop on wifi on HOME network
The error diagnostic information.
Subject: http://www.google.co.uk
Issuer: Google Internet Authority G3
Expires on: 9 Jan 2018
Current date: 28 Oct 2017
PEM encoded chain: …
Chrome 49 is extremely outdated and is not safe to use to browse the Internet. If you have this problem with the latest version of Chrome, you’ll need to follow the instructions in https://textslashplain.com/2017/10/23/google-internet-authority-g3/ to get the right intermediate certificate installed. (This should be happening automatically if Windows is properly configured, but various problems in Windows could cause it to fail…)
Attackers might be trying to steal your information from mail.google.com (for example, passwords, messages, or credit cards). Learn more
NET::ERR_CERT_AUTHORITY_INVALID
Subject: mail.google.com
Issuer: Google Internet Authority G3
Expires on: Jan 9, 2018
Current date: Oct 30, 2017
PEM encoded chain: …
You’ll need to follow the instructions in https://textslashplain.com/2017/10/23/google-internet-authority-g3/ to get the right intermediate certificate installed. (This should be happening automatically if Windows is properly configured, but various problems in Windows could cause it to fail…)
NET::ERR_CERT_AUTHORITY_INVALID
Subject: good.gsr2demo.pki.goog
Issuer: Google Internet Authority G3
Expires on: 10.09.2018.
Current date: 30.10.2017.
PEM encoded chain: …
You’ll need to follow the instructions in https://textslashplain.com/2017/10/23/google-internet-authority-g3/ to get the right intermediate certificate installed. (This should be happening automatically if Windows is properly configured, but various problems in Windows could cause it to fail…)
Bob – v49 is 18 months old. Chrome has become more secure since then.
That said, I recognize that some users do not want to or cannot upgrade.
You can try the fix in https://textslashplain.com/2017/10/23/google-internet-authority-g3
to install a new root certificate.
If you do, let us know how it goes.
Larry
(yet another Chrome enthusiast)
Tnx, after installation of a new certificate google.com is working. This is interesting, it only happens on https://www.google.com page, on other web sites i can surf normally.
Attackers might be trying to steal your information from mail.google.com (for example, passwords, messages, or credit cards). NET::ERR_SSL_PINNED_KEY_NOT_IN_CERT_CHAIN
Subject: mail.google.com
Issuer: Google Internet Authority G3
Expires on: Jan 16, 2018
Current date: Nov 1, 2017
PEM encoded chain: —–BEGIN CERTIFICATE—–
MIID4jCCAsqgAwIBAgIICqSP8H+5TP0wDQYJKoZIhvcNAQELBQAwVDELMAkGA1UE
BhMCVVMxHjAcBgNVBAoTFUdvb2dsZSBUcnVzdCBTZXJ2aWNlczElMCMGA1UEAxMc
R29vZ2xlIEludGVybmV0IEF1dGhvcml0eSBHMzAeFw0xNzEwMjQwOTQ0NTZaFw0x
ODAxMTYwODQwMDBaMGkxCzAJBgNVBAYTAlVTMRMwEQYDVQQIDApDYWxpZm9ybmlh
MRYwFAYDVQQHDA1Nb3VudGFpbiBWaWV3MRMwEQYDVQQKDApHb29nbGUgSW5jMRgw
FgYDVQQDDA9tYWlsLmdvb2dsZS5jb20wWTATBgcqhkjOPQIBBggqhkjOPQMBBwNC
AAQ8Mx4A6wInBLpyUoCa67Exu3qfhhU72ceYFX+CCI+XchRlzcSsjYaMlL0bUVza
0MZKG2gYqIwDqjufG7UT2fFio4IBbDCCAWgwHQYDVR0lBBYwFAYIKwYBBQUHAwEG
CCsGAQUFBwMCMAsGA1UdDwQEAwIHgDAsBgNVHREEJTAjgg9tYWlsLmdvb2dsZS5j
b22CEGluYm94Lmdvb2dsZS5jb20waAYIKwYBBQUHAQEEXDBaMC0GCCsGAQUFBzAC
hiFodHRwOi8vcGtpLmdvb2cvZ3NyMi9HVFNHSUFHMy5jcnQwKQYIKwYBBQUHMAGG
HWh0dHA6Ly9vY3NwLnBraS5nb29nL0dUU0dJQUczMB0GA1UdDgQWBBTziwTNz9Ns
U+7fWfa4W5oCss31JDAMBgNVHRMBAf8EAjAAMB8GA1UdIwQYMBaAFHfCuFCaZ3Z2
sS3ChtCDoH6mfrpLMCEGA1UdIAQaMBgwDAYKKwYBBAHWeQIFAzAIBgZngQwBAgIw
MQYDVR0fBCowKDAmoCSgIoYgaHR0cDovL2NybC5wa2kuZ29vZy9HVFNHSUFHMy5j
cmwwDQYJKoZIhvcNAQELBQADggEBAAE5Mtq5HLirRoAlf/zvrZhpIFs1ZdrtIIv+
dXQ1SyiqLdDPY9/AxvC853ZnnhJV10rsfAzXIYYLeU5/Z6Kv+RWLXEufL8VTcIce
CjaiN98x19EbsgVrlRRzTIBfXpX5MWgbQFaSlDsmjXoGDrnT/TlOqN4r6GBf3JJm
VizFLQqe4R2xhwrhHu4rHKGB8KeTJl5fMalYELJlomm6EKZQBFKkA8P011G/VoHk
SmVEq5hkCzzOcTtncnLdBkTbhDcwFH6EmfLwt1CnQmxi6aGs72WNKP/3iT6XDT2u
YhQEhbCNIo5qzQ4vrXw2XlE9dNOnRgWI5e/38GtlTUIJ+JtJ+Ts=
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIEXDCCA0SgAwIBAgINAeOpMBz8cgY4P5pTHTANBgkqhkiG9w0BAQsFADBMMSAw
HgYDVQQLExdHbG9iYWxTaWduIFJvb3QgQ0EgLSBSMjETMBEGA1UEChMKR2xvYmFs
U2lnbjETMBEGA1UEAxMKR2xvYmFsU2lnbjAeFw0xNzA2MTUwMDAwNDJaFw0yMTEy
MTUwMDAwNDJaMFQxCzAJBgNVBAYTAlVTMR4wHAYDVQQKExVHb29nbGUgVHJ1c3Qg
U2VydmljZXMxJTAjBgNVBAMTHEdvb2dsZSBJbnRlcm5ldCBBdXRob3JpdHkgRzMw
ggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDKUkvqHv/OJGuo2nIYaNVW
XQ5IWi01CXZaz6TIHLGp/lOJ+600/4hbn7vn6AAB3DVzdQOts7G5pH0rJnnOFUAK
71G4nzKMfHCGUksW/mona+Y2emJQ2N+aicwJKetPKRSIgAuPOB6Aahh8Hb2XO3h9
RUk2T0HNouB2VzxoMXlkyW7XUR5mw6JkLHnA52XDVoRTWkNty5oCINLvGmnRsJ1z
ouAqYGVQMc/7sy+/EYhALrVJEA8KbtyX+r8snwU5C1hUrwaW6MWOARa8qBpNQcWT
kaIeoYvy/sGIJEmjR0vFEwHdp1cSaWIr6/4g72n7OqXwfinu7ZYW97EfoOSQJeAz
AgMBAAGjggEzMIIBLzAOBgNVHQ8BAf8EBAMCAYYwHQYDVR0lBBYwFAYIKwYBBQUH
AwEGCCsGAQUFBwMCMBIGA1UdEwEB/wQIMAYBAf8CAQAwHQYDVR0OBBYEFHfCuFCa
Z3Z2sS3ChtCDoH6mfrpLMB8GA1UdIwQYMBaAFJviB1dnHB7AagbeWbSaLd/cGYYu
MDUGCCsGAQUFBwEBBCkwJzAlBggrBgEFBQcwAYYZaHR0cDovL29jc3AucGtpLmdv
b2cvZ3NyMjAyBgNVHR8EKzApMCegJaAjhiFodHRwOi8vY3JsLnBraS5nb29nL2dz
cjIvZ3NyMi5jcmwwPwYDVR0gBDgwNjA0BgZngQwBAgIwKjAoBggrBgEFBQcCARYc
aHR0cHM6Ly9wa2kuZ29vZy9yZXBvc2l0b3J5LzANBgkqhkiG9w0BAQsFAAOCAQEA
HLeJluRT7bvs26gyAZ8so81trUISd7O45skDUmAge1cnxhG1P2cNmSxbWsoiCt2e
ux9LSD+PAj2LIYRFHW31/6xoic1k4tbWXkDCjir37xTTNqRAMPUyFRWSdvt+nlPq
wnb8Oa2I/maSJukcxDjNSfpDh/Bd1lZNgdd/8cLdsE3+wypufJ9uXO1iQpnh9zbu
FIwsIONGl1p3A8CgxkqI/UAih3JaGOqcpcdaCIzkBaR9uYQ1X4k2Vg5APRLouzVy
7a8IVk6wuy6pm+T7HT4LY8ibS5FEZlfAFLSW8NwsVz9SBK2Vqn1N0PIMn5xA6NZV
c7o835DLAFshEWfC7TIe3g==
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIDujCCAqKgAwIBAgILBAAAAAABD4Ym5g0wDQYJKoZIhvcNAQEFBQAwTDEgMB4G
A1UECxMXR2xvYmFsU2lnbiBSb290IENBIC0gUjIxEzARBgNVBAoTCkdsb2JhbFNp
Z24xEzARBgNVBAMTCkdsb2JhbFNpZ24wHhcNMDYxMjE1MDgwMDAwWhcNMjExMjE1
MDgwMDAwWjBMMSAwHgYDVQQLExdHbG9iYWxTaWduIFJvb3QgQ0EgLSBSMjETMBEG
A1UEChMKR2xvYmFsU2lnbjETMBEGA1UEAxMKR2xvYmFsU2lnbjCCASIwDQYJKoZI
hvcNAQEBBQADggEPADCCAQoCggEBAKbPJA6+Lm8omUVCxKs+IVSbC9N/hHD6ErPL
v4dfxn+G07IwXNb9rfF73OX4YJYJkhD10FPe+3t+c4isUoh7SqbKSaZeqKeMWhG8
eoLrvozps6yWJQeXSpkqBy+0Hne/ig+1AnwblrjFuTosvNYSuetZfeLQBoZfXklq
tTleiDTsvHgMCJiEbKjNS7SgfQx5TfC4LcshytVsW33hoCmEofnTlEnLJGKRILzd
C9XZzPnqJworc5HGnRusyMvo4KD0L5CLTfuwNhv2GXqF4G3yYROIXJ/gkwpRl4pa
zq+r1feqCapgvdzZX99yqWATXgAByUr6P6TqBwMhAo6CygPCm48CAwEAAaOBnDCB
mTAOBgNVHQ8BAf8EBAMCAQYwDwYDVR0TAQH/BAUwAwEB/zAdBgNVHQ4EFgQUm+IH
V2ccHsBqBt5ZtJot39wZhi4wNgYDVR0fBC8wLTAroCmgJ4YlaHR0cDovL2NybC5n
bG9iYWxzaWduLm5ldC9yb290LXIyLmNybDAfBgNVHSMEGDAWgBSb4gdXZxwewGoG
3lm0mi3f3BmGLjANBgkqhkiG9w0BAQUFAAOCAQEAmYFThxxol4aR7OBKuEQLq4Gs
J0/WwbgcQ3izDJr86iw8bmEbTUsp9Z8FHSbBuOmDAGJFtqkIk7mpM0sYmsL4h4hO
291xNBrBVNpGP+DTKqttVCL1OmLNIG+6KYnX3ZHu01yiPqFbQfXf5WRDLenVOavS
ot+3i9DAgBkcRcAtjOj4LaR0VknFBbVPFd5uRHg5h6h+u/N5GJG79G+dwfCMNYxd
AfvDbbnvRG15RjF+Cv6pgsH/76tuIMRQyV+dTZsXjAzlAcmgQWpzU/qlULRuJQ/7
TBj0/VLZjmmx6BEP3ojY+x1J96relc8geMJgEtslQIxq/H5COEBkEveegeGTLg==
—–END CERTIFICATE—–
Automatically report details of possible security incidents to Google. Privacy policy
Would I be correct in guessing that you’re using some ancient version of Chrome (e.g. Chrome 49)?
NET::ERR_CERT_AUTHORITY_INVALID
Subject: *.google.co.kr
Issuer: Google Internet Authority G3
Expires on: 2018. 1. 16.
Current date: 2017. 11. 2.
PEM encoded chain:
—–BEGIN CERTIFICATE—–
MIIEsjCCA5qgAwIBAgIIQr7N+INJrIgwDQYJKoZIhvcNAQELBQAwVDELMAkGA1UE
BhMCVVMxHjAcBgNVBAoTFUdvb2dsZSBUcnVzdCBTZXJ2aWNlczElMCMGA1UEAxMc
R29vZ2xlIEludGVybmV0IEF1dGhvcml0eSBHMzAeFw0xNzEwMjQwOTQyNThaFw0x
ODAxMTYwODQwMDBaMGgxCzAJBgNVBAYTAlVTMRMwEQYDVQQIDApDYWxpZm9ybmlh
MRYwFAYDVQQHDA1Nb3VudGFpbiBWaWV3MRMwEQYDVQQKDApHb29nbGUgSW5jMRcw
FQYDVQQDDA4qLmdvb2dsZS5jby5rcjCCASIwDQYJKoZIhvcNAQEBBQADggEPADCC
AQoCggEBAOGiFJadBJUkDlmg3lgt12b4Pok8TyXOp7MOrOQa4PBdiCtZhYBrKjkF
imrLO01A1A4BUifCESy6p7Pymi75AX3Ud/6Vi729QAMRvfNz6s4iAzsOImiNlJRv
DvkhGUMMUNXXutN/jbQ8yowWQCfNWy/1AlFmojUwmI/CLLQFQsfdA4aDDE8ucDNZ
4GfdRiyEeMDL1Hxg3anwqDloRjeew9c/T4wYz2v+9vBQcoPvlmHj3dBEJmFlRq/B
e10T/GY0/iMJC762N/YjfQZ7MF126tP1MH0z6VfySNpqET+HwTQnThGPhD/Xr9KV
UuWL+McYfEICFluy3IKir+jV6yKy7HsCAwEAAaOCAXIwggFuMB0GA1UdJQQWMBQG
CCsGAQUFBwMBBggrBgEFBQcDAjA/BgNVHREEODA2gg4qLmdvb2dsZS5jby5rcoIL
Ki5nb29nbGUua3KCDGdvb2dsZS5jby5rcoIJZ29vZ2xlLmtyMGgGCCsGAQUFBwEB
BFwwWjAtBggrBgEFBQcwAoYhaHR0cDovL3BraS5nb29nL2dzcjIvR1RTR0lBRzMu
Y3J0MCkGCCsGAQUFBzABhh1odHRwOi8vb2NzcC5wa2kuZ29vZy9HVFNHSUFHMzAd
BgNVHQ4EFgQUFs88Q1Up4NCavogCqjDAWHTiS1UwDAYDVR0TAQH/BAIwADAfBgNV
HSMEGDAWgBR3wrhQmmd2drEtwobQg6B+pn66SzAhBgNVHSAEGjAYMAwGCisGAQQB
1nkCBQMwCAYGZ4EMAQICMDEGA1UdHwQqMCgwJqAkoCKGIGh0dHA6Ly9jcmwucGtp
Lmdvb2cvR1RTR0lBRzMuY3JsMA0GCSqGSIb3DQEBCwUAA4IBAQClna0VtJjqwzRf
aGBzC2XbkYuEw/O1LVrggETsiwSqhDSNiQnuwpCPaMB8D93rVRn6Amolh/Wt/Lhr
h4GaPCJAGGryQVsL0hjT/RsVq3lMv7Q5ELFMAv8uU4Ugvz4u3yUGYiKLEUqNOhbp
t44qs1WP5dOjmHb9X48CKKp41fW4KF56wM3fJbxhtcHOHFVBYZS3EHCtVkeNITpj
jnq7vKJ6ymTU5uFBCVXJNoNkSdGSCNAmNm+qVUYvcAG+U5Kg3qFH9YHiBOGa2ld3
50eUXawhyDdIlpsTY/TY0e1X2vYXKfC/JFt5CNMirAxAuiUyir9bF/wz5Bz+Hhae
aIkSlPwk
—–END CERTIFICATE—–
Please see https://textslashplain.com/2017/10/23/google-internet-authority-g3/ for steps to resolve this issue.
Eric:
A common source of the SSL_PINNED_KEY failures is another (Chromium based?) browser: UC Browser. I am trying to pool the Chrome Forum posts here:
https://productforums.google.com/forum/#!topic/chrome/tMMdiEv-UOk
I’ve posted to the UC Browser forum here, with ref back to the G3 blog article:
http://forum.ucweb.com/forum.php?mod=viewthread&tid=1151143
That’s interesting, insofar as the Chromium code compiles out certificate pins when not compiled as an official “Chrome” desktop build. So if UC Browser is really putting it back, that’s on them…
UC Browser is another spinoff of Chromium (from Taobao, Chinese, built on M55).
Their BB/forum is not very responsive. >15 cases reported since 10/1.
I think 1 Chrome forum user fixed the SSL_PINNED error by installing the R2-CA root,
but I would have to check
BTW. Since I signed in to text/plain with a wordpress account, I have not been getting email notifications of your replies…
Attackers might be trying to steal your information from mail.google.com (for example, passwords, messages, or credit cards). Learn more
NET::ERR_CERT_AUTHORITY_INVALID
Subject: mail.google.com
Issuer: Google Internet Authority G3
Expires on: Jan 16, 2018
Current date: Nov 6, 2017
PEM encoded chain:
—–BEGIN CERTIFICATE—–
MIID4jCCAsqgAwIBAgIICqSP8H+5TP0wDQYJKoZIhvcNAQELBQAwVDELMAkGA1UE
BhMCVVMxHjAcBgNVBAoTFUdvb2dsZSBUcnVzdCBTZXJ2aWNlczElMCMGA1UEAxMc
R29vZ2xlIEludGVybmV0IEF1dGhvcml0eSBHMzAeFw0xNzEwMjQwOTQ0NTZaFw0x
ODAxMTYwODQwMDBaMGkxCzAJBgNVBAYTAlVTMRMwEQYDVQQIDApDYWxpZm9ybmlh
MRYwFAYDVQQHDA1Nb3VudGFpbiBWaWV3MRMwEQYDVQQKDApHb29nbGUgSW5jMRgw
FgYDVQQDDA9tYWlsLmdvb2dsZS5jb20wWTATBgcqhkjOPQIBBggqhkjOPQMBBwNC
AAQ8Mx4A6wInBLpyUoCa67Exu3qfhhU72ceYFX+CCI+XchRlzcSsjYaMlL0bUVza
0MZKG2gYqIwDqjufG7UT2fFio4IBbDCCAWgwHQYDVR0lBBYwFAYIKwYBBQUHAwEG
CCsGAQUFBwMCMAsGA1UdDwQEAwIHgDAsBgNVHREEJTAjgg9tYWlsLmdvb2dsZS5j
b22CEGluYm94Lmdvb2dsZS5jb20waAYIKwYBBQUHAQEEXDBaMC0GCCsGAQUFBzAC
hiFodHRwOi8vcGtpLmdvb2cvZ3NyMi9HVFNHSUFHMy5jcnQwKQYIKwYBBQUHMAGG
HWh0dHA6Ly9vY3NwLnBraS5nb29nL0dUU0dJQUczMB0GA1UdDgQWBBTziwTNz9Ns
U+7fWfa4W5oCss31JDAMBgNVHRMBAf8EAjAAMB8GA1UdIwQYMBaAFHfCuFCaZ3Z2
sS3ChtCDoH6mfrpLMCEGA1UdIAQaMBgwDAYKKwYBBAHWeQIFAzAIBgZngQwBAgIw
MQYDVR0fBCowKDAmoCSgIoYgaHR0cDovL2NybC5wa2kuZ29vZy9HVFNHSUFHMy5j
cmwwDQYJKoZIhvcNAQELBQADggEBAAE5Mtq5HLirRoAlf/zvrZhpIFs1ZdrtIIv+
dXQ1SyiqLdDPY9/AxvC853ZnnhJV10rsfAzXIYYLeU5/Z6Kv+RWLXEufL8VTcIce
CjaiN98x19EbsgVrlRRzTIBfXpX5MWgbQFaSlDsmjXoGDrnT/TlOqN4r6GBf3JJm
VizFLQqe4R2xhwrhHu4rHKGB8KeTJl5fMalYELJlomm6EKZQBFKkA8P011G/VoHk
SmVEq5hkCzzOcTtncnLdBkTbhDcwFH6EmfLwt1CnQmxi6aGs72WNKP/3iT6XDT2u
YhQEhbCNIo5qzQ4vrXw2XlE9dNOnRgWI5e/38GtlTUIJ+JtJ+Ts=
—–END CERTIFICATE—–
Please see https://textslashplain.com/2017/10/23/google-internet-authority-g3/
NET::ERR_CERT_AUTHORITY_INVALID
Subject: *.google.co.kr
Issuer: Google Internet Authority G3
Expires on: 2018. 1. 24.
Current date: 2017. 11. 8.
Subject: gmail.com
Issuer: Google Internet Authority G3
Expires on: Jan 24, 2018
Current date: Nov 13, 2017
Please see https://textslashplain.com/2017/10/23/google-internet-authority-g3/
Eric et All – LQQks like the ‘Get Help with HTTPS..’ article needs another tweak, to shortstop the Authority G3 case and redirect to the Authority G3 article. Something like…
When you click the NET::ERR_… failure tag and the Issuer is: Google Internet Authority G3
there is likely a problem with the PC auto-update process. For this special case, see https://textslashplain.com/2017/10/23/google-internet-authority-g3/
NET::ERR_CERT_AUTHORITY_INVALID
Subject: mail.google.com
Issuer: Google Internet Authority G3
Expires on: Jan 24, 2018
Current date: Dec 29, 2017
Please see https://textslashplain.com/2017/10/23/google-internet-authority-g3/
https://www.facebook.com/ Wystawca certyfikatu uczestnika komunikacji nie został rozpoznany.
—–BEGIN CERTIFICATE—– MIIFsTCCBJmgAwIBAgIDBv3gMA0GCSqGSIb3DQEBCwUAMEcxCzAJBgNVBAYTAlVT MRYwFAYDVQQKEw1HZW9UcnVzdCBJbmMuMSAwHgYDVQQDExdSYXBpZFNTTCBTSEEy NTYgQ0EgLSBHMzAeFw0xNTA5MTYwMDMzMDJaFw0xNzA5MTgwNDAzNDVaMIGbMRMw EQYDVQQLEwpHVDU4MDczMzAyMTEwLwYDVQQLEyhTZWUgd3d3LnJhcGlkc3NsLmNv bS9yZXNvdXJjZXMvY3BzIChjKTE1MS8wLQYDVQQLEyZEb21haW4gQ29udHJvbCBW YWxpZGF0ZWQgLSBSYXBpZFNTTChSKTEgMB4GA1UEAxMXc2VhcmNoLmRuc2FkdmFu dGFnZS5jb20wggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCwktbK5LPl uxgTMNXpsrnP/FeT474yEim1KqdD/jsQFYIAZKVSbxU2oMqRqWqTSWVGbrOfNGcO Wm8wt8ZsW74RBDPnmta7TSCmXqMKWYSUOrBSCz9+WKZhubLjLKmfm89sxeoH793b OABGhdc/DK+fbZC2wnINx7oSV3WrVrq6QlcenOlqlLOiO/ec5CKWy7SEk0ahm0Xj xwrj2iY/Z3hhcMe7M0g0i7Vy+y6tEak+sMmfCZaq0VYlmQbbCaMjltgXLkJvNYPI rt/K8ttC5EZuTeVWTeWnY02LIUZT4qsvZQmgwnCQzlumY3gXabH5qgEUGy6NuB2/ lDD9wm+OAO8FH72DwNggfiJWtPnqd8R4oqNrXhoHzl7RPpr6s4siQv7ql4PbCSbY N/iraMPqJksl+Zi6gjnk1u2MGa6c93lhiea8tTeZgDZV3vpw+IuQC5YW+/ZYlz8V Np1kkUIl4kp/HptDUTsrA83xNXQ6WuYEzJ/fSHwTg33i559tMIVVwJx5OBRkXC9k +kvUiWzyEuhUXO6l9tECebrV5YT2wPMc1RZvcxbyWlxqal7KKIzsxKtKYF0FqZ/c IF2amCHTbS3k+8Rdwl0SOGfFeSdSO4N7MoyGlBAg5GSjC9F96pxkLNZR1BYJauZD pm/OsouqSYOez1BlMwF//dzyDI/gu3+JXwIDAQABo4IBTzCCAUswHwYDVR0jBBgw FoAUw5zz/NNGCDS7zkZ/oHxb8+IIy1kwVwYIKwYBBQUHAQEESzBJMB8GCCsGAQUF BzABhhNodHRwOi8vZ3Yuc3ltY2QuY29tMCYGCCsGAQUFBzAChhpodHRwOi8vZ3Yu c3ltY2IuY29tL2d2LmNydDAOBgNVHQ8BAf8EBAMCBaAwHQYDVR0lBBYwFAYIKwYB BQUHAwEGCCsGAQUFBwMCMCIGA1UdEQQbMBmCF3NlYXJjaC5kbnNhZHZhbnRhZ2Uu Y29tMCsGA1UdHwQkMCIwIKAeoByGGmh0dHA6Ly9ndi5zeW1jYi5jb20vZ3YuY3Js MAwGA1UdEwEB/wQCMAAwQQYDVR0gBDowODA2BgZngQwBAgEwLDAqBggrBgEFBQcC ARYeaHR0cHM6Ly93d3cucmFwaWRzc2wuY29tL2xlZ2FsMA0GCSqGSIb3DQEBCwUA A4IBAQCsluwg3oAwyL6opH9Hjopmc1Ufb12ByI+DG+TglevvvDn/UNa5oxjTo87V EWqCKrYvzB9AUT62KVtlu8B+J01eo4vLunhZLGxxQW25VMrwmWPF03rAwDNPsP0L /S5+VmxeCvvXUu/2Hy/K36/xjsezALgKZgigPeyb2gTciXl7PlybDIpM2vDtklBr nW4JB8j9jb+L8S6sK9JHPv6V++wFvWCR/b82wdaBakgqXmu4Pw/NzolckM9Zkd2f vD2XalV31iAWQ3hLtBHv/b9zI4C/Y1N3zvp6E1FGCBG2DTWqbS+7iyrlipQ7Ly6U bER4APY1wPEt+CQcRF/AMyCN/bmS
—–END CERTIFICATE—–
Your computer is infected with malware called DNSAdvantage. You’ll need to remove it.
HOW I CAN REMOVE IT ?
please help me…
i don’t know what is mean…..
NET::ERR_CERT_COMMON_NAME_INVALID
Subject: http://www.google.co.kr
Issuer: GeoTrust_Global_CA
Expires on: 2028. 1. 8.
Current date: 2018. 1. 11.
PEM encoded chain:
—–BEGIN CERTIFICATE—–
MIIDCTCCAnKgAwIBAgIQa809jtUr65ZAzm6/APHqnDANBgkqhkiG9w0BAQsFADBp
MSUwIwYDVQQLExxJc3N1ZWQgYnkgR2VvVHJ1c3QgR2xvYmFsIENBMREwDwYDVQQK
EwhHZW9UcnVzdDEtMCsGA1UEAx4kAEcAZQBvAFQAcgB1AHMAdABfAEcAbABvAGIA
YQBsAF8AQwBBMB4XDTE3MDEwODE1MDAwMFoXDTI4MDEwODE0NTk1OVowVTElMCMG
A1UECxMcSXNzdWVkIGJ5IEdlb1RydXN0IEdsb2JhbCBDQTERMA8GA1UEChMIR2Vv
VHJ1c3QxGTAXBgNVBAMTEHd3dy5nb29nbGUuY28ua3IwgZ8wDQYJKoZIhvcNAQEB
BQADgY0AMIGJAoGBAM8Wtz4ATLsZNoDwwG3GU9LiPntbWnkWutU8f/9kCWdTu6Wx
WEIHIU6/jPu4dt06H+xlfhcMoQlw9RHQtxJy8/Q1ATMTosBfXn9O+8ruSXFO22iO
e7BKXaxdv1wFTtPZthCU3he9CnT+obEqzJPt5y9YJ86Pw0D+OGYUAtaiRpfBAgMB
AAGjgcUwgcIwDAYDVR0TAQH/BAIwADATBgNVHSUEDDAKBggrBgEFBQcDATCBnAYD
VR0BBIGUMIGRgBCSSjjUQklKPWUY2b+r/I6BoWswaTElMCMGA1UECxMcSXNzdWVk
IGJ5IEdlb1RydXN0IEdsb2JhbCBDQTERMA8GA1UEChMIR2VvVHJ1c3QxLTArBgNV
BAMeJABHAGUAbwBUAHIAdQBzAHQAXwBHAGwAbwBiAGEAbABfAEMAQYIQ558LDCat
kKFExvIp5+OBmDANBgkqhkiG9w0BAQsFAAOBgQDKFafJvWJfgKoxr4CwwY3/ETXV
Vfp1ZAc/K3biFkpVOl+7pFW42U8xsUyHjl7UEnbmO0UXpxeVSUJ65padutBq1coN
P9JYaBEXxGBX9LdFkTHmH2j36rUIrazY3tU2gSOsoMEPr0ecq2YIhLvRAreQqy5v
JQqbiWHIQhxttT0uog==
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIDIzCCAoygAwIBAgIQ558LDCatkKFExvIp5+OBmDANBgkqhkiG9w0BAQsFADBp
MSUwIwYDVQQLExxJc3N1ZWQgYnkgR2VvVHJ1c3QgR2xvYmFsIENBMREwDwYDVQQK
EwhHZW9UcnVzdDEtMCsGA1UEAx4kAEcAZQBvAFQAcgB1AHMAdABfAEcAbABvAGIA
YQBsAF8AQwBBMB4XDTE3MDEwNzE1MDAwMFoXDTI4MDEwNzE0NTk1OVowaTElMCMG
A1UECxMcSXNzdWVkIGJ5IEdlb1RydXN0IEdsb2JhbCBDQTERMA8GA1UEChMIR2Vv
VHJ1c3QxLTArBgNVBAMeJABHAGUAbwBUAHIAdQBzAHQAXwBHAGwAbwBiAGEAbABf
AEMAQTCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEA2bljdKBfO9Jm7Qirl4Go
l776edRnkurohhRKBeob2MF4y+Qjte8RLNg1slBi/VPIoHDXPutHNITY/MJAO0oI
eCISVax3IwF5fhX/9sZjjFsG9qy/cEOUxwx2BqTJR0zvsQyqyS03EaKSqQ++lsZY
7Z5cDHY7kdXqysjhQTIFy7ECAwEAAaOByzCByDASBgNVHRMBAf8ECDAGAQH/AgEB
MBMGA1UdJQQMMAoGCCsGAQUFBwMBMIGcBgNVHQEEgZQwgZGAEJJKONRCSUo9ZRjZ
v6v8joGhazBpMSUwIwYDVQQLExxJc3N1ZWQgYnkgR2VvVHJ1c3QgR2xvYmFsIENB
MREwDwYDVQQKEwhHZW9UcnVzdDEtMCsGA1UEAx4kAEcAZQBvAFQAcgB1AHMAdABf
AEcAbABvAGIAYQBsAF8AQwBBghDnnwsMJq2QoUTG8inn44GYMA0GCSqGSIb3DQEB
CwUAA4GBAFr7kZNOKOH7cIHn6L2sn1iAm+ZNarizv5Ssv0pbSWy/WXLdLACy/wt6
L7DAzLjAva8cEfR5czb1A1Kpx+7T6NoyIRcvyJjHmU++owyq8biu3A47SJvKV18/
3KDjaETmRyNrm7tX91Xl+malJ89EPSDyE8oQDrv1xw/+KEbgECEE
—–END CERTIFICATE—–
This appears to be an attack. The certificate claims to be from “GeoTrust_Global_CA” which uses the name of an actual CA, but the certificate has a lifetime of 11 years (fake), lacks a SubjectAltName (invalid) and was likely to have been generated by malicious software running on your PC.
You should scan your PC for malware immediately. If none is found, it’s possible that your network is compromised or malicious.
Eric: The GeoTrust_Global_CA cert is sometimes installed with a private key. Does this help trying to track down the source? See the 12/24 (screenshot) and my 12/26 reply to Tomasz. His case was still unresolved per last contact.
Ref:
https://productforums.google.com/forum/#!topic/chrome/XOhcyt_myeg
If the private key is present, it means that the malware is installed locally.
Agreed: local. Any tips on back tracking from the private key to the malware?
please help!
NET::ERR_CERT_COMMON_NAME_INVALID
Subject: *.cs30.my.salesforce.com
Issuer: DigiCert SHA2 Secure Server CA
Expires on: Dec 14, 2019
Current date: Jan 11, 2018
PEM encoded chain:
—–BEGIN CERTIFICATE—–
MIIGxzCCBa+gAwIBAgIQAp8Dt+oRlRTGaK3XMgH4DjANBgkqhkiG9w0BAQsFADBN
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMScwJQYDVQQDEx5E
aWdpQ2VydCBTSEEyIFNlY3VyZSBTZXJ2ZXIgQ0EwHhcNMTcxMjE0MDAwMDAwWhcN
MTkxMjE0MTIwMDAwWjCBjzELMAkGA1UEBhMCVVMxEzARBgNVBAgTCkNhbGlmb3Ju
aWExFjAUBgNVBAcTDVNhbiBGcmFuY2lzY28xHTAbBgNVBAoTFHNhbGVzZm9yY2Uu
Y29tLCBpbmMuMREwDwYDVQQLEwhJbmZyYVNlYzEhMB8GA1UEAwwYKi5jczMwLm15
LnNhbGVzZm9yY2UuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA
xv2Szs7b/+1vP3VHAPyOjV3geObZVj8MFIfXBS/pY4udedEm2S848ZjuuLEH6e7G
oy5hyS803K9InXC95A6n5DjMPMGmsP16o6G+/ivk+0W6wgDqqGNzonM+2+EwjtZa
Fro+vYIOr5fu0sfseELWyhqzDsMNHzfTtVX2Y5VUQXtCe0n5Ci3FKGm2PA29CxBN
nqtB7puSOeFGQWJnZuq2/nLsnNN20Vj48pdoQ2AAIW0AYlYC+1OdLne377Avym1x
Gg2d2T6CekEDodeoAzTn9KQRjBo6ZBFNcwGg1qhZg4cnyi7HBuv+3SDGc+D6/w33
irnoCSeMhS9zqiPO2u7SEwIDAQABo4IDXjCCA1owHwYDVR0jBBgwFoAUD4BhHIIx
YdUvKOeNRji0LOHG2eIwHQYDVR0OBBYEFM3nInm/qk9ERmiFQGjucfhJpxrBMCMG
A1UdEQQcMBqCGCouY3MzMC5teS5zYWxlc2ZvcmNlLmNvbTAOBgNVHQ8BAf8EBAMC
BaAwHQYDVR0lBBYwFAYIKwYBBQUHAwEGCCsGAQUFBwMCMGsGA1UdHwRkMGIwL6At
oCuGKWh0dHA6Ly9jcmwzLmRpZ2ljZXJ0LmNvbS9zc2NhLXNoYTItZzYuY3JsMC+g
LaArhilodHRwOi8vY3JsNC5kaWdpY2VydC5jb20vc3NjYS1zaGEyLWc2LmNybDBM
BgNVHSAERTBDMDcGCWCGSAGG/WwBATAqMCgGCCsGAQUFBwIBFhxodHRwczovL3d3
dy5kaWdpY2VydC5jb20vQ1BTMAgGBmeBDAECAjB8BggrBgEFBQcBAQRwMG4wJAYI
KwYBBQUHMAGGGGh0dHA6Ly9vY3NwLmRpZ2ljZXJ0LmNvbTBGBggrBgEFBQcwAoY6
aHR0cDovL2NhY2VydHMuZGlnaWNlcnQuY29tL0RpZ2lDZXJ0U0hBMlNlY3VyZVNl
cnZlckNBLmNydDAJBgNVHRMEAjAAMIIBfgYKKwYBBAHWeQIEAgSCAW4EggFqAWgA
dQCkuQmQtBhYFIe7E6LMZ3AKPDWYBPkb37jjd80OyA3cEAAAAWBTtkW4AAAEAwBG
MEQCICH7+JHJaewV7JMaGbuoHv9wuh3xCq3Albu6L5WGeLL9AiAUOpxOljzrq0PX
vSrdWt9nP9KI/OnqVT/Ik7zMD9vkJwB3AId1v+dZfPiMQ5lfvfNu/1aNR1Y2/0q1
YMG06v9eoIMPAAABYFO2RwkAAAQDAEgwRgIhAL9HsafwGe4qZ6S1+z87invePl3R
SXolw5jOjemNSDskAiEAk6KRRuBG4cXzFdfYv7jAVroFaGVe26my8tSr2qU5S50A
dgC72d+8H4pxtZOUI5eqkntHOFeVCqtS6BqQlmQ2jh7RhQAAAWBTtkZcAAAEAwBH
MEUCIHzVLgiZt17CvtMchiQzsG8tHhUE0h5Dl6zAbihyeba4AiEA4VwmM8fv4V5G
25a48ZMO6EAhku8YLVL94IUuMUDv9a4wDQYJKoZIhvcNAQELBQADggEBAE9S1xIS
BPJ8DNWLzSJRSE/B2DMiV5yKvSs75bOuHrdSLKdwqbKJQklSqL92lRJHbEw/OcXX
B1e14iGXsn28FMmTl502s6QkOyR9YVbp5LosfN80HjstFchlGSUTOXDEOeVJ+UVO
wnyll6Qd2oaMTDsg2ETb7x2lkfDAV8Ljzpp5DHYIpWKj3QKJrmOySeLlpfUCxHbD
0tae5+BXHdF0RMqtiZ+OmwZve/I+nFbgjmVQLR5CSIrxUgjBcV1QNcEVfZz4YdVH
dTDZ/6g4oD2/BccjUQEGEL7c2QLVuMoLIIvU+V5YGFHNSsU7DvfipU33NQIBpEts
/r2M9GEwju9YCUU=
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIElDCCA3ygAwIBAgIQAf2j627KdciIQ4tyS8+8kTANBgkqhkiG9w0BAQsFADBh
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3
d3cuZGlnaWNlcnQuY29tMSAwHgYDVQQDExdEaWdpQ2VydCBHbG9iYWwgUm9vdCBD
QTAeFw0xMzAzMDgxMjAwMDBaFw0yMzAzMDgxMjAwMDBaME0xCzAJBgNVBAYTAlVT
MRUwEwYDVQQKEwxEaWdpQ2VydCBJbmMxJzAlBgNVBAMTHkRpZ2lDZXJ0IFNIQTIg
U2VjdXJlIFNlcnZlciBDQTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEB
ANyuWJBNwcQwFZA1W248ghX1LFy949v/cUP6ZCWA1O4Yok3wZtAKc24RmDYXZK83
nf36QYSvx6+M/hpzTc8zl5CilodTgyu5pnVILR1WN3vaMTIa16yrBvSqXUu3R0bd
KpPDkC55gIDvEwRqFDu1m5K+wgdlTvza/P96rtxcflUxDOg5B6TXvi/TC2rSsd9f
/ld0Uzs1gN2ujkSYs58O09rg1/RrKatEp0tYhG2SS4HD2nOLEpdIkARFdRrdNzGX
kujNVA075ME/OV4uuPNcfhCOhkEAjUVmR7ChZc6gqikJTvOX6+guqw9ypzAO+sf0
/RR3w6RbKFfCs/mC/bdFWJsCAwEAAaOCAVowggFWMBIGA1UdEwEB/wQIMAYBAf8C
AQAwDgYDVR0PAQH/BAQDAgGGMDQGCCsGAQUFBwEBBCgwJjAkBggrBgEFBQcwAYYY
aHR0cDovL29jc3AuZGlnaWNlcnQuY29tMHsGA1UdHwR0MHIwN6A1oDOGMWh0dHA6
Ly9jcmwzLmRpZ2ljZXJ0LmNvbS9EaWdpQ2VydEdsb2JhbFJvb3RDQS5jcmwwN6A1
oDOGMWh0dHA6Ly9jcmw0LmRpZ2ljZXJ0LmNvbS9EaWdpQ2VydEdsb2JhbFJvb3RD
QS5jcmwwPQYDVR0gBDYwNDAyBgRVHSAAMCowKAYIKwYBBQUHAgEWHGh0dHBzOi8v
d3d3LmRpZ2ljZXJ0LmNvbS9DUFMwHQYDVR0OBBYEFA+AYRyCMWHVLyjnjUY4tCzh
xtniMB8GA1UdIwQYMBaAFAPeUDVW0Uy7ZvCj4hsbw5eyPdFVMA0GCSqGSIb3DQEB
CwUAA4IBAQAjPt9L0jFCpbZ+QlwaRMxp0Wi0XUvgBCFsS+JtzLHgl4+mUwnNqipl
5TlPHoOlblyYoiQm5vuh7ZPHLgLGTUq/sELfeNqzqPlt/yGFUzZgTHbO7Djc1lGA
8MXW5dRNJ2Srm8c+cftIl7gzbckTB+6WohsYFfZcTEDts8Ls/3HB40f/1LkAtDdC
2iDJ6m6K7hQGrn2iWZiIqBtvLfTyyRRfJs8sjX7tN8Cp1Tm5gr8ZDOo0rwAhaPit
c+LJMto4JQtV05od8GiG7S5BNO98pVAdvzr508EIDObtHopYJeS4d60tbvVS3bR0
j6tJLp07kzQoH3jOlOrHvdPJbRzeXDLz
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIDrzCCApegAwIBAgIQCDvgVpBCRrGhdWrJWZHHSjANBgkqhkiG9w0BAQUFADBh
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3
d3cuZGlnaWNlcnQuY29tMSAwHgYDVQQDExdEaWdpQ2VydCBHbG9iYWwgUm9vdCBD
QTAeFw0wNjExMTAwMDAwMDBaFw0zMTExMTAwMDAwMDBaMGExCzAJBgNVBAYTAlVT
MRUwEwYDVQQKEwxEaWdpQ2VydCBJbmMxGTAXBgNVBAsTEHd3dy5kaWdpY2VydC5j
b20xIDAeBgNVBAMTF0RpZ2lDZXJ0IEdsb2JhbCBSb290IENBMIIBIjANBgkqhkiG
9w0BAQEFAAOCAQ8AMIIBCgKCAQEA4jvhEXLeqKTTo1eqUKKPC3eQyaKl7hLOllsB
CSDMAZOnTjC3U/dDxGkAV53ijSLdhwZAAIEJzs4bg7/fzTtxRuLWZscFs3YnFo97
nh6Vfe63SKMI2tavegw5BmV/Sl0fvBf4q77uKNd0f3p4mVmFaG5cIzJLv07A6Fpt
43C/dxC//AH2hdmoRBBYMql1GNXRor5H4idq9Joz+EkIYIvUX7Q6hL+hqkpMfT7P
T19sdl6gSzeRntwi5m3OFBqOasv+zbMUZBfHWymeMr/y7vrTC0LUq7dBMtoM1O/4
gdW7jVg/tRvoSSiicNoxBN33shbyTApOB6jtSj1etX+jkMOvJwIDAQABo2MwYTAO
BgNVHQ8BAf8EBAMCAYYwDwYDVR0TAQH/BAUwAwEB/zAdBgNVHQ4EFgQUA95QNVbR
TLtm8KPiGxvDl7I90VUwHwYDVR0jBBgwFoAUA95QNVbRTLtm8KPiGxvDl7I90VUw
DQYJKoZIhvcNAQEFBQADggEBAMucN6pIExIK+t1EnE9SsPTfrgT1eXkIoyQY/Esr
hMAtudXH/vTBH1jLuG2cenTnmCmrEbXjcKChzUyImZOMkXDiqw8cvpOp/2PV5Adg
06O/nVsJ8dWO41P0jmP6P6fbtGbfYmbW0W5BjfIttep3Sp+dWOIrWcBAI+0tKIJF
PnlUkiaY4IBIqDfv8NZ5YBberOgOzW6sRBc4L0na4UU+Krk2U886UAb3LujEV0ls
YSEY1QSteDwsOoBrp+uvFRTp2InBuThs4pFsiv9kuXclVzDAGySj4dzp30d8tbQk
CAUw7C29C79Fv1C5qfPrmAESrciIxpg0X40KPMbp1ZWVbd4=
—–END CERTIFICATE—–
What’s the URL of the page that sent this certificate?
me puedes ayudar, me falla solo con google chrome,
NET::ERR_CERT_INVALID
Subject: *.facebook.com
Issuer: DigiCert SHA2 High Assurance Server CA
Expires on: 22/03/2019
Current date: 15/01/2018
PEM encoded chain:
—–BEGIN CERTIFICATE—–
MIIGsjCCBZqgAwIBAgIQCzw7YBoY9Z7itrsFYF7ywDANBgkqhkiG9w0BAQsFADBw
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3
d3cuZGlnaWNlcnQuY29tMS8wLQYDVQQDEyZEaWdpQ2VydCBTSEEyIEhpZ2ggQXNz
dXJhbmNlIFNlcnZlciBDQTAeFw0xNzEyMTUwMDAwMDBaFw0xOTAzMjIxMjAwMDBa
MGkxCzAJBgNVBAYTAlVTMRMwEQYDVQQIEwpDYWxpZm9ybmlhMRMwEQYDVQQHEwpN
ZW5sbyBQYXJrMRcwFQYDVQQKEw5GYWNlYm9vaywgSW5jLjEXMBUGA1UEAwwOKi5m
YWNlYm9vay5jb20wWTATBgcqhkjOPQIBBggqhkjOPQMBBwNCAASIA87IjqqM6JBX
puN20BXCVsDjoP9wnF2rSV60qC130oLTrgfOQ3Uk1dv1R6LFCx4gs2pJUu6iDKBS
/b+BXOUbo4IEGDCCBBQwHwYDVR0jBBgwFoAUUWj/kK8CB3U8zNllZGKiErhZcjsw
HQYDVR0OBBYEFMD9dPV9y8Yn8QPTYqJF14QcFSEIMIHHBgNVHREEgb8wgbyCDiou
ZmFjZWJvb2suY29tgg4qLnh4LmZiY2RuLm5ldIILKi5mYnNieC5jb22CDioueHou
ZmJjZG4ubmV0gg4qLmZhY2Vib29rLm5ldIIOKi54eS5mYmNkbi5uZXSCDyoubWVz
c2VuZ2VyLmNvbYIGZmIuY29tggsqLmZiY2RuLm5ldIIIKi5mYi5jb22CECoubS5m
YWNlYm9vay5jb22CDW1lc3Nlbmdlci5jb22CDGZhY2Vib29rLmNvbTAOBgNVHQ8B
Af8EBAMCB4AwHQYDVR0lBBYwFAYIKwYBBQUHAwEGCCsGAQUFBwMCMHUGA1UdHwRu
MGwwNKAyoDCGLmh0dHA6Ly9jcmwzLmRpZ2ljZXJ0LmNvbS9zaGEyLWhhLXNlcnZl
ci1nNi5jcmwwNKAyoDCGLmh0dHA6Ly9jcmw0LmRpZ2ljZXJ0LmNvbS9zaGEyLWhh
LXNlcnZlci1nNi5jcmwwTAYDVR0gBEUwQzA3BglghkgBhv1sAQEwKjAoBggrBgEF
BQcCARYcaHR0cHM6Ly93d3cuZGlnaWNlcnQuY29tL0NQUzAIBgZngQwBAgIwgYMG
CCsGAQUFBwEBBHcwdTAkBggrBgEFBQcwAYYYaHR0cDovL29jc3AuZGlnaWNlcnQu
Y29tME0GCCsGAQUFBzAChkFodHRwOi8vY2FjZXJ0cy5kaWdpY2VydC5jb20vRGln
aUNlcnRTSEEySGlnaEFzc3VyYW5jZVNlcnZlckNBLmNydDAMBgNVHRMBAf8EAjAA
MIIBfgYKKwYBBAHWeQIEAgSCAW4EggFqAWgAdgCkuQmQtBhYFIe7E6LMZ3AKPDWY
BPkb37jjd80OyA3cEAAAAWBXnEHoAAAEAwBHMEUCIBC3Rn4i2bhLyR344u3vl7be
vxoi+WPJBhGT+j1gJmg5AiEAwQ3rzH1mmMSYNYKtVNDZMo+l6e8Z35t+X9NDR7Du
gWAAdwCHdb/nWXz4jEOZX73zbv9WjUdWNv9KtWDBtOr/XqCDDwAAAWBXnEL7AAAE
AwBIMEYCIQCRjvvPARW3J1ENmo2Nz1cxisa1BcbDuqvSrfuXkz8btAIhAPmllqgF
8JjlVHUChiFzghsKVBeTxRagi55tgsAciaoZAHUAu9nfvB+KcbWTlCOXqpJ7RzhX
lQqrUugakJZkNo4e0YUAAAFgV5xCUgAABAMARjBEAiBY6qdNgMoQAqVTl3zRrTmy
+X/1f/esBUczsb3MWdZ1ZgIgXdxZNTrDBgyTzxgbVRObkqU3tZZdaiwsw4WI0xI0
BtQwDQYJKoZIhvcNAQELBQADggEBAGu0uxZD+IRXXlFWLPvknRkXA7J08NyVKG70
M2vDi2xF2YB8qlZgoxW8YiiV86IpwtOhYLZinSO0iCBDQmTf627LTPfuDcF6qOuO
WFTvj1IbplPvGWIu5tNBiFWNQxFAIL2Rf+5vmIe+YezUHTLGGqwRtFa2ImS17IMk
YjZ90LYXXO5qb1RKkFJtAvEBTbJsv8kr+J6Rx+YNJy17LnBX+MbWiyBbvUQoM3sY
MmcWmcaQmECz9ZHWYjZeufSHbHKG6KDYLU8x6DyhgtxK2rsoIMlNnJkNHaLjw+b8
7VCYa+EMWppvVuNyXOk9Jkbx7Q3SEoodT77kkHUX0bF2OkZy6cc=
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIEsTCCA5mgAwIBAgIQBOHnpNxc8vNtwCtCuF0VnzANBgkqhkiG9w0BAQsFADBs
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3
d3cuZGlnaWNlcnQuY29tMSswKQYDVQQDEyJEaWdpQ2VydCBIaWdoIEFzc3VyYW5j
ZSBFViBSb290IENBMB4XDTEzMTAyMjEyMDAwMFoXDTI4MTAyMjEyMDAwMFowcDEL
MAkGA1UEBhMCVVMxFTATBgNVBAoTDERpZ2lDZXJ0IEluYzEZMBcGA1UECxMQd3d3
LmRpZ2ljZXJ0LmNvbTEvMC0GA1UEAxMmRGlnaUNlcnQgU0hBMiBIaWdoIEFzc3Vy
YW5jZSBTZXJ2ZXIgQ0EwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQC2
4C/CJAbIbQRf1+8KZAayfSImZRauQkCbztyfn3YHPsMwVYcZuU+UDlqUH1VWtMIC
Kq/QmO4LQNfE0DtyyBSe75CxEamu0si4QzrZCwvV1ZX1QK/IHe1NnF9Xt4ZQaJn1
itrSxwUfqJfJ3KSxgoQtxq2lnMcZgqaFD15EWCo3j/018QsIJzJa9buLnqS9UdAn
4t07QjOjBSjEuyjMmqwrIw14xnvmXnG3Sj4I+4G3FhahnSMSTeXXkgisdaScuM0X
sh5ENWV/UyU50RwKmmMbGZJ0aAo3wsJSSMs5WqK24V3B3aAguCGikyZvFEohQcft
bZvySC/zA/WiaJJTL17jAgMBAAGjggFJMIIBRTASBgNVHRMBAf8ECDAGAQH/AgEA
MA4GA1UdDwEB/wQEAwIBhjAdBgNVHSUEFjAUBggrBgEFBQcDAQYIKwYBBQUHAwIw
NAYIKwYBBQUHAQEEKDAmMCQGCCsGAQUFBzABhhhodHRwOi8vb2NzcC5kaWdpY2Vy
dC5jb20wSwYDVR0fBEQwQjBAoD6gPIY6aHR0cDovL2NybDQuZGlnaWNlcnQuY29t
L0RpZ2lDZXJ0SGlnaEFzc3VyYW5jZUVWUm9vdENBLmNybDA9BgNVHSAENjA0MDIG
BFUdIAAwKjAoBggrBgEFBQcCARYcaHR0cHM6Ly93d3cuZGlnaWNlcnQuY29tL0NQ
UzAdBgNVHQ4EFgQUUWj/kK8CB3U8zNllZGKiErhZcjswHwYDVR0jBBgwFoAUsT7D
aQP4v0cB1JgmGggC72NkK8MwDQYJKoZIhvcNAQELBQADggEBABiKlYkD5m3fXPwd
aOpKj4PWUS+Na0QWnqxj9dJubISZi6qBcYRb7TROsLd5kinMLYBq8I4g4Xmk/gNH
E+r1hspZcX30BJZr01lYPf7TMSVcGDiEo+afgv2MW5gxTs14nhr9hctJqvIni5ly
/D6q1UEL2tU2ob8cbkdJf17ZSHwD2f2LSaCYJkJA69aSEaRkCldUxPUd1gJea6zu
xICaEnL6VpPX/78whQYwvwt/Tv9XBZ0k7YXDK/umdaisLRbvfXknsuvCnQsH6qqF
0wGjIChBWUMo0oHjqvbsezt3tkBigAVBRQHvFwY+3sAzm2fTYS5yh+Rp/BIAV0Ae
cPUeybQ=
—–END CERTIFICATE—–
—–BEGIN CERTIFICATE—–
MIIDxTCCAq2gAwIBAgIQAqxcJmoLQJuPC3nyrkYldzANBgkqhkiG9w0BAQUFADBs
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3
d3cuZGlnaWNlcnQuY29tMSswKQYDVQQDEyJEaWdpQ2VydCBIaWdoIEFzc3VyYW5j
ZSBFViBSb290IENBMB4XDTA2MTExMDAwMDAwMFoXDTMxMTExMDAwMDAwMFowbDEL
MAkGA1UEBhMCVVMxFTATBgNVBAoTDERpZ2lDZXJ0IEluYzEZMBcGA1UECxMQd3d3
LmRpZ2ljZXJ0LmNvbTErMCkGA1UEAxMiRGlnaUNlcnQgSGlnaCBBc3N1cmFuY2Ug
RVYgUm9vdCBDQTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAMbM5XPm
+9S75S0tMqbf5YE/yc0lSbZxKsPVlDRnogocsF9ppkCxxLeyj9CYpKlBWTrT3JTW
PNt0OKRKzE0lgvdKpVMSOO7zSW1xkX5jtqumX8OkhPhPYlG++MXs2ziS4wblCJEM
xChBVfvLWokVfnHoNb9Ncgk9vjo4UFt3MRuNs8ckRZqnrG0AFFoEt7oT61EKmEFB
Ik5lYYeBQVCmeVyJ3hlKV9Uu5l0cUyx+mM0aBhakaHPQNAQTXKFx01p8VdteZOE3
hzBWBOURtCmAEvF5OYiiAhF8J2a3iLd48soKqDirCmTCv2ZdlYTBoSUeh10aUAsg
EsxBu24LUTi4S8sCAwEAAaNjMGEwDgYDVR0PAQH/BAQDAgGGMA8GA1UdEwEB/wQF
MAMBAf8wHQYDVR0OBBYEFLE+w2kD+L9HAdSYJhoIAu9jZCvDMB8GA1UdIwQYMBaA
FLE+w2kD+L9HAdSYJhoIAu9jZCvDMA0GCSqGSIb3DQEBBQUAA4IBAQAcGgaX3Nec
nzyIZgYIVyHbIUf4KmeqvxgydkAQV8GK83rZEWWONfqe/EW1ntlMMUu4kehDLI6z
eM7b41N5cdblIZQB2lWHmiRk9opmzN6cN82oNLFpmyPInngiK3BD41VHMWEZ71jF
hS9OMPagMRYjyOfiZRYzy78aG6A9+MpeizGLYAiJLQwGXFK3xPkKmNEVX58Svnw2
Yzi9RKR/5CYrCsSXaQ3pjOLAEFe4yHYSkVXySGnYvCoCWw9E1CAx2/S6cCZdkGCe
vEsXCS+0yx5DaMkHJ8HSXPfqIbloEpw8nL+e/IBcm2PN7EeqJSdnoDfzAIJ9VNep
+OkuE6N36B9K
—–END CERTIFICATE—–
The server certificate here (the one for Facebook) looks good. However, the intermediate certificate, for “DigiCert SHA2 High Assurance Server CA” is corrupt by a single byte. This causes the validation to fail.
On what OS are you having this problem? The most likely explanation (if you see this all the time, not just once) is that something has corrupted the operating system’s certificate cache. On Windows, deleting the intermediate certificate using CertMgr.msc may resolve the problem.
HOW DO I FIX THIS??
NET::ERR_CERT_AUTHORITY_INVALID
Subject: mail.google.com
Issuer: Cisco Umbrella Secondary SubCA lax-SG
Expires on: Jan 25, 2018
Current date: Jan 22, 2018
You are using a network that is spying on your HTTPS traffic. If this is expected, talk to the network administrator about how you are expected to install the “Cisco Umbrella” certificate so that these warnings disappear and they can spy on your traffic without warnings.
!Oops. (My last) Should read: M65 update should NOT require a WiFi reboot
This is my error certificate.
NET::ERR_CERT_COMMON_NAME_INVALID
Subject: *.researchnow.com
Issuer: Symantec Class 3 Secure Server CA – G4
Expires on: Jan 21, 2019
Current date: Apr 24, 2018
That’s your certificate for what URL in the address bar?
Based on the Subject field, my guess is that your computer has local “spyware” installed that watches every website you visit as a part of a consumer research project (e.g. you let them spy on you, they give you points for gift cards or whatever). That spyware is supposed to be using a valid certificate, but its configuration is corrupt on your PC for whatever reason. You should check your system’s Add/Remove Programs control panel and remove any unwanted software.