Sometimes, you’ll notice that a background tab has an orange dot on it in Edge (or a blue dot in Chrome). If you click on the tab, the dot disappears. Why? The dot indicates that the tab wants “attention” — more specifically, that there’s a dialog in the tab asking for your attention. This mightContinue reading “Q: Why do tabs sometimes show an orange dot?”
Tag Archives: UI
Spooky: Enhancing Dark Mode in Chromium
I am not really a fan of Dark Mode — I like my screens bright and shiny. But it’s October, and it’s sometimes fun to make things dark and spooky. Some users of my Show Browser Version extension wanted it to better support Dark Mode– the default text colors didn’t work well when the browserContinue reading “Spooky: Enhancing Dark Mode in Chromium”
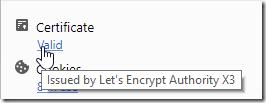
Inspecting Certificates in Edge
Curious about how to see a website’s HTTPS certificate in Microsoft Edge? You’ve got two options: A companion post to 2017’s post Inspecting Certificates in Chrome.
Avoiding Unexpected Navigation
For over twenty years, browsers broadly supported two features that were often convenient but sometimes accidentally invoked, leading to data loss. The first feature was that hitting backspace would send the user back one page in their navigation history. (Dec 2022 Update: I’ve been using this feature for 25 years or so now and onlyContinue reading “Avoiding Unexpected Navigation”
Bypassing AppProtocol Prompts
Starting in Microsoft Edge 77 (and Chrome 77), the prompt shown when launching an AppProtocol from the browser was changed to remove the “Always allow” checkbox. That change was made, in large part, because this prompt is the only thing standing between every arbitrary site on the Internet (loaded inside your browser’s sandbox) and aContinue reading “Bypassing AppProtocol Prompts”
Edge EV UI Requires SmartScreen
A user recently noticed that when loading Paypal.com in Microsoft Edge, the UI shown was the default HTTPS UI (a gray lock): Instead of the fancier “green” UI shown for servers that present Extended Validation (EV) certificates: The user observed this on some Windows 10 machines but not others. The variable that differed between those machines wasContinue reading “Edge EV UI Requires SmartScreen”
Inspecting Certificates in Chrome
Chrome 60 introduces a new option to quickly show Certificate information for the current page.
Security UI in Chrome
The combined address box and search bar at the top of the Chrome window is called the omnibox. The icon and optional verbose state text adjacent to that icon are collectively known as the Security Chip: The security chip can render in a number of states, depending on the status of the page: Secure –Continue reading “Security UI in Chrome”