I recently bought a few new domain names under the brand new .app top-level-domain (TLD). The .app TLD is awesome because it’s on the HSTSPreload list, meaning that browsers will automatically use only HTTPS for every request on every domain under .app, keeping connections secure and improving performance.
I’m not doing anything terribly exciting with these domains for now, but I’d like to at least put up a simple welcome page on each one. Now, in the old days of HTTP, this was trivial, but because .app requires HTTPS, that means I must get a certificate for each of my sites for them to load at all.
Fortunately, GitHub recently started supporting HTTPS on GitHub Pages with custom domains, meaning that I can easily get a HTTPS site up in running in just a few minutes.
1. Log into GitHub, go to your Repositories page and click New:

2. Name your new repository something reasonable:
3. Click to create a simple README file:
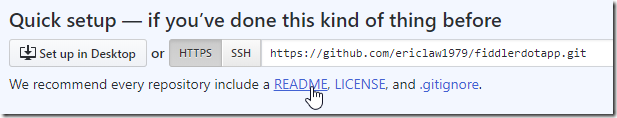
4. Edit the file
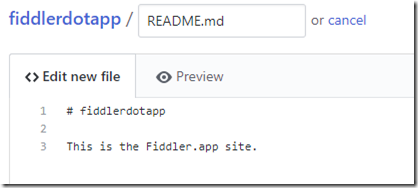
5. Click Commit new file
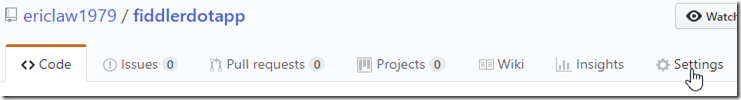
6. Click Settings on the repository
7. Scroll to the GitHub Pages section and choose master branch and click Save:

8. Enter your domain name in the Custom domain box and click Save

9. Login to NameCheap (or whatever DNS registrar you used) and click Manage for the target domain name:
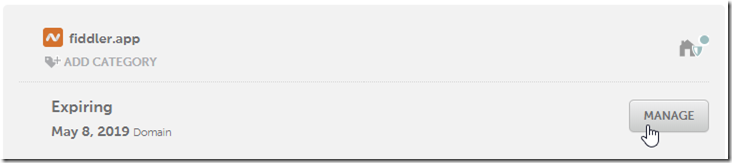
10. Click the Advanced DNS tab:
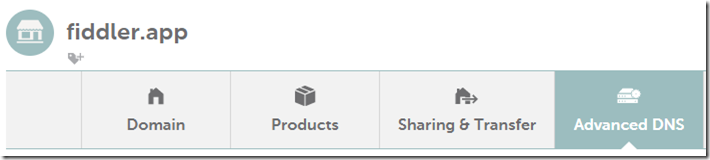
11. Click Add New Record:
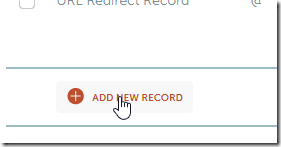
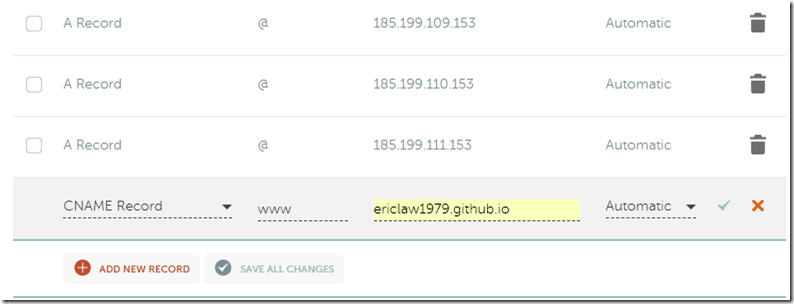
12. Enter four new A Records for host of @ with the list of IP addresses GitHub pages use:
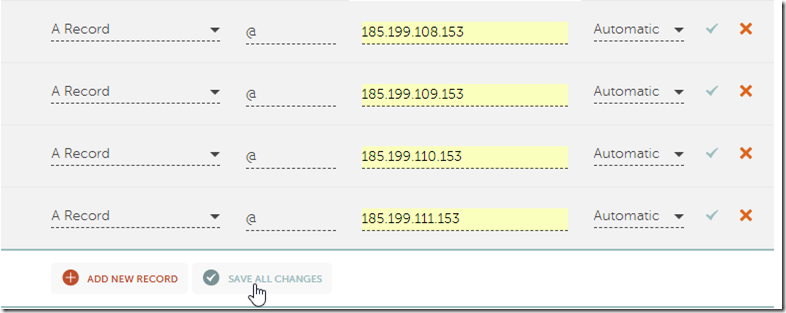
13. Click Save All Changes.
14. Click Add New Record and add a new CNAME Record. Enter the host www and a target value of username.github.io. Click Save All Changes:
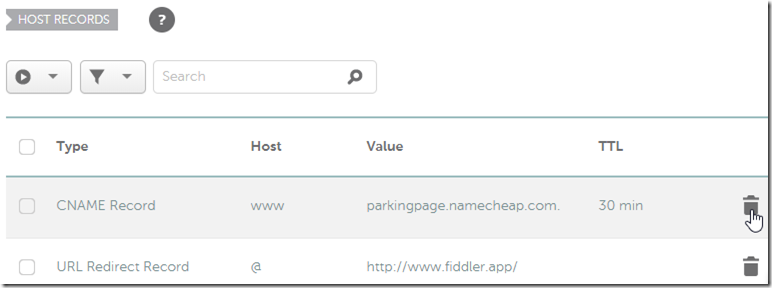
15. Click the trash can icons to delete the two default DNS entries that NameCheap had for your domain previously:
16. Try loading your new site.
- If you get a connection error, wait a few minutes for DNS to propagate and re-verify the DNS records you just added.
- If you get a certificate error, look at the certificate. It’s probably the default GitHub certificate. If so, look in the GitHub Pages settings page and you may see a note that your certificate is awaiting issuance by LetsEncrypt.org. If so, just wait a little while.

- After the certificate is issued, your site without errors:
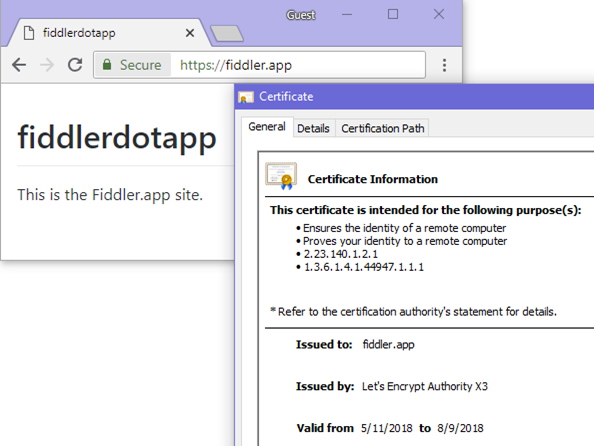
Go forth and build great (secure) things!
-Eric Lawrence